强网杯2023 wp
本文最后更新于 2024年1月1日 下午
队伍信息

Web
happygame
发现是grpc服务
用postman的grpc模式发包
ysoserial生成cc7
反弹shell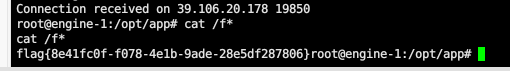
1 | |
Crypto
discrete_log
题目
1 | |
解题思路
DLP问题,p=2q+1,一开始看这个p作为安全素数,怎么能分解,然后查到了几个帖子。
How can I solve the discrete logarithm modulo 2q+1 if I can solve it in the subgroup of order q?
On getting beyond LSB in discrete log
第一个告诉我们安全素数可以从Zp群降到Zq群,其实就是方便分解也没啥特别了。第二个贴说了一个 $r^{x}=hg^{-x_0}\bmod p$ 的办法,结合给出的
1 | |
可以知道去掉flag头和flag尾,还有pad,字符串应该不大,选择大概在10~20左右进行爆破,(其实是一个一个试。。。就是中间人相遇的问题了,硬爆。
1 | |
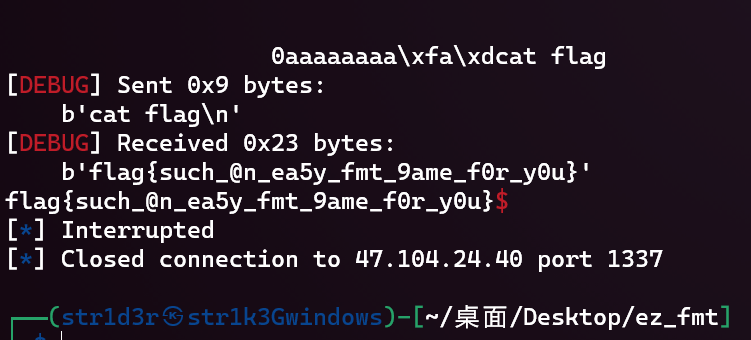
b’flag{61e8007dd65f}’
Misc
谍影重重2.0
题目说明
题目内容:
小明是某间谍组织的一员,他终日监听着我国某重点军事基地的飞行动态,妄图通过分析参数找到我国飞的最快的飞机。我国费尽千辛万苦抓住了他,并在他的电脑上找到了一段他监听的信息,请分析出这段信息中飞的最快的飞机。
格式为flag{md5(ICAO CODE of the fastest plane)}
解题思路
由提示知是飞机流量https://mode-s.org/decode/content/ads-b/1-basics.html
导出有tcp.payload字段的流 为1.pcapng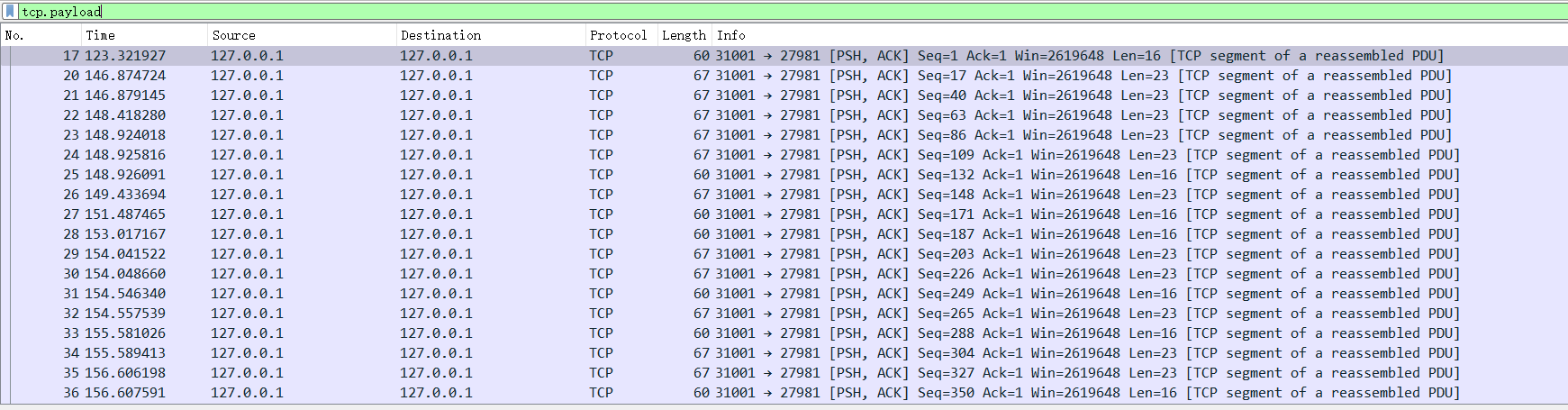
1 | |
提取数据pip install pyModeS
1 | |
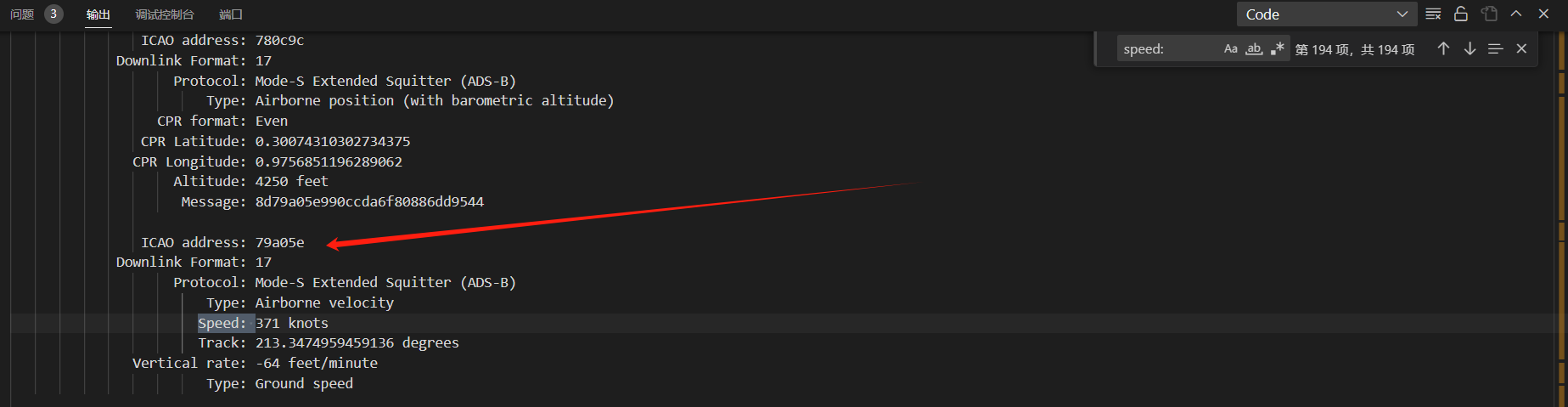
ICAO 要大写
1 | |
Pyjail ! It’s myFILTER !!!
题目说明
题目内容:
你能否能帮助她绕过filter呢?是时候拿出真本事!提示:本题需要一定的成功率,如果你认为你的payload能够工作,请多尝试几遍!
1 | |
解题思路
限制了payload长度小于65
过滤了很多Print 和 open、read 没过滤,可以配合读文件并打印
读取当前进程的环境变量
1 | |
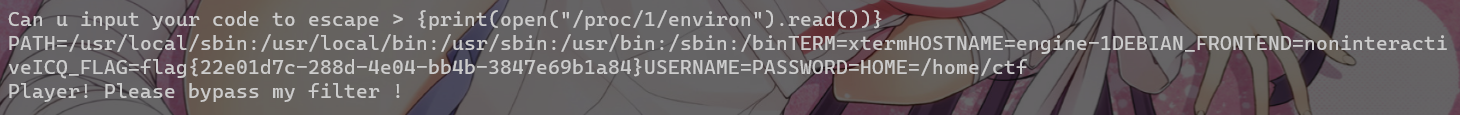
easyfuzz
解题思路
一个个遍历9位字符
返回的0代表该位字符不对,1则代表该位字符正确
1 | |
00qwbGood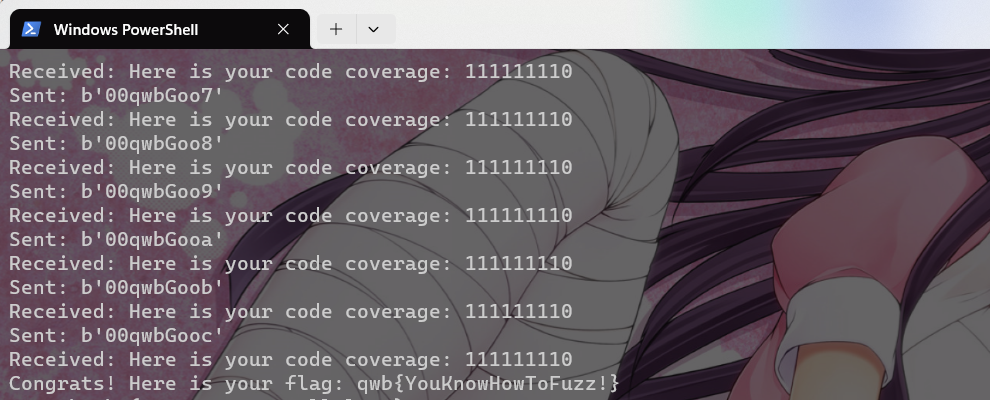
Happy Chess
解题思路
每轮输入1 1时观察靶机返回值,怀疑存在逻辑漏洞
然后每轮输入1 1 来循环最后以exit结束对局并开启下一局,循环10轮后就拿到了flag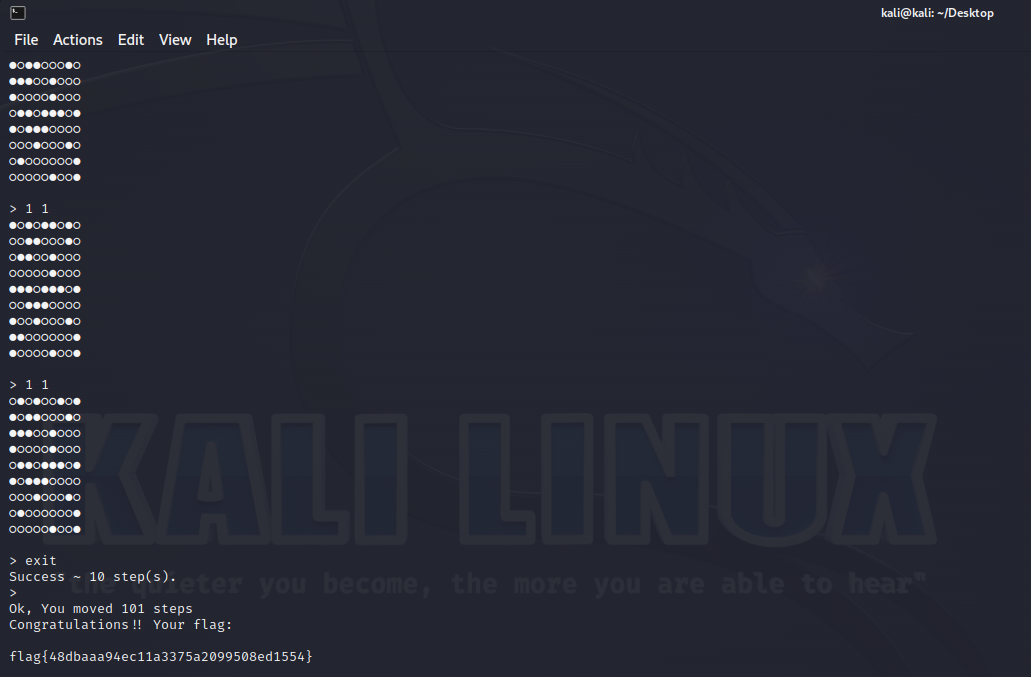
强网先锋
石头剪刀布
解题思路
1 | |
SpeedUp
解题思路
https://oeis.org/A244060/list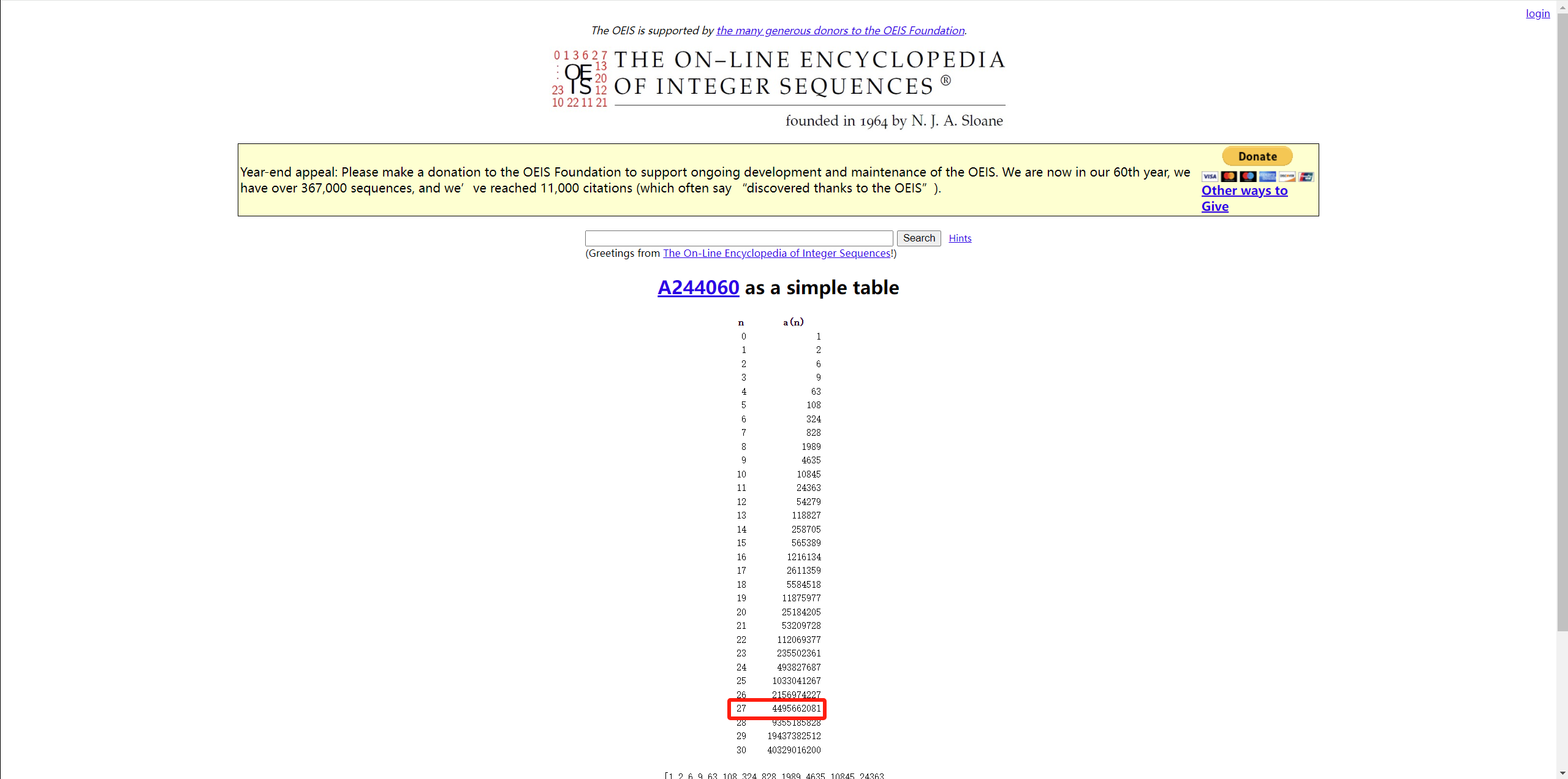
找到PNG了吗
题目说明
解题思路
不太会Linux内存取证,用R-studio看了一下,没找到啥有用的东西,直接Strings 找到PNG了吗.mem(这个过程要耗一点时间,文件太大了)
然后在字符串中翻看到一处加密程序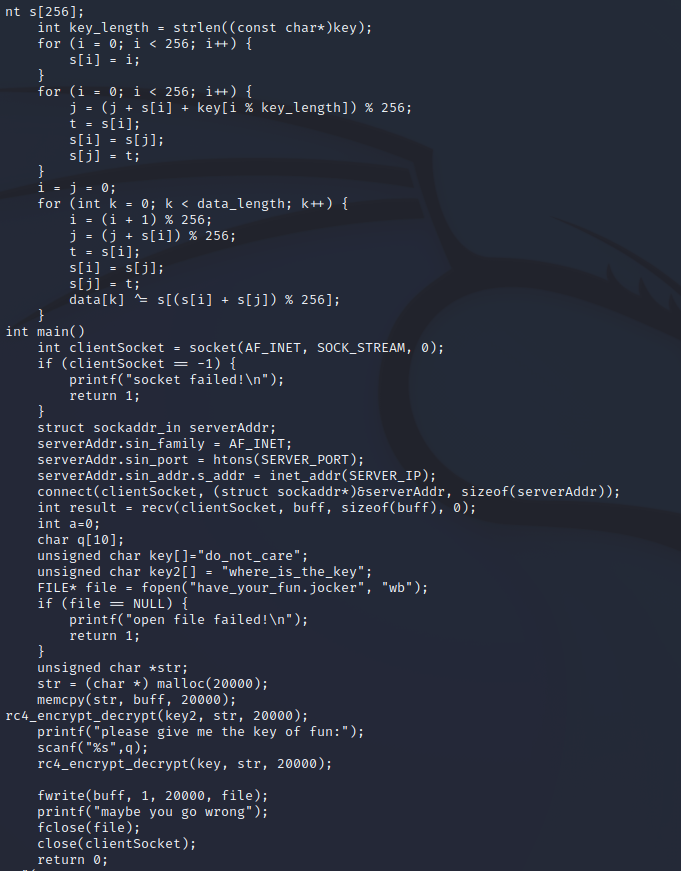
主要加密函数如下,根据 rc4_encrypt_decrypt可以看出这是一个对文件进行RC4加密的程序
1 | |
再根据题目信息猜测这个加密程序对发送的png图片做了处理,所以我们逆向思维去找加密后的png图片,以png文件头为特征值RC4加密得到,新的文件头0e 3c b4 2f 99 96 95 56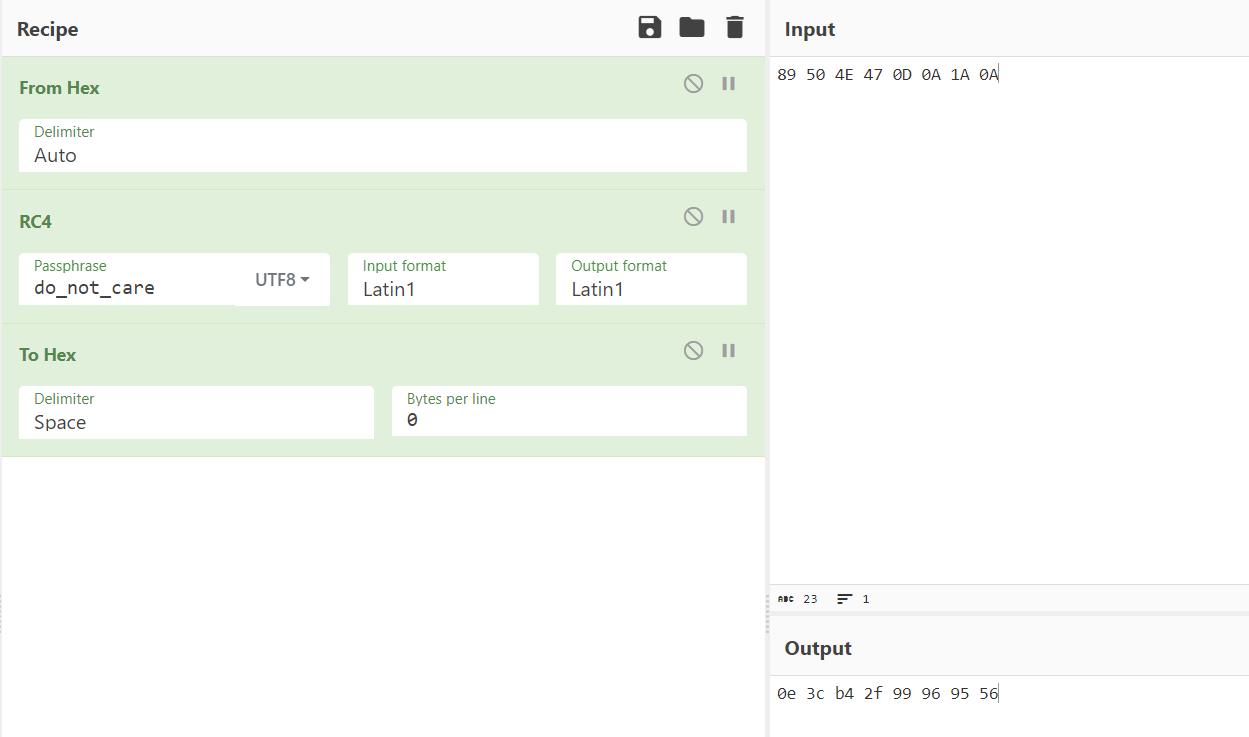
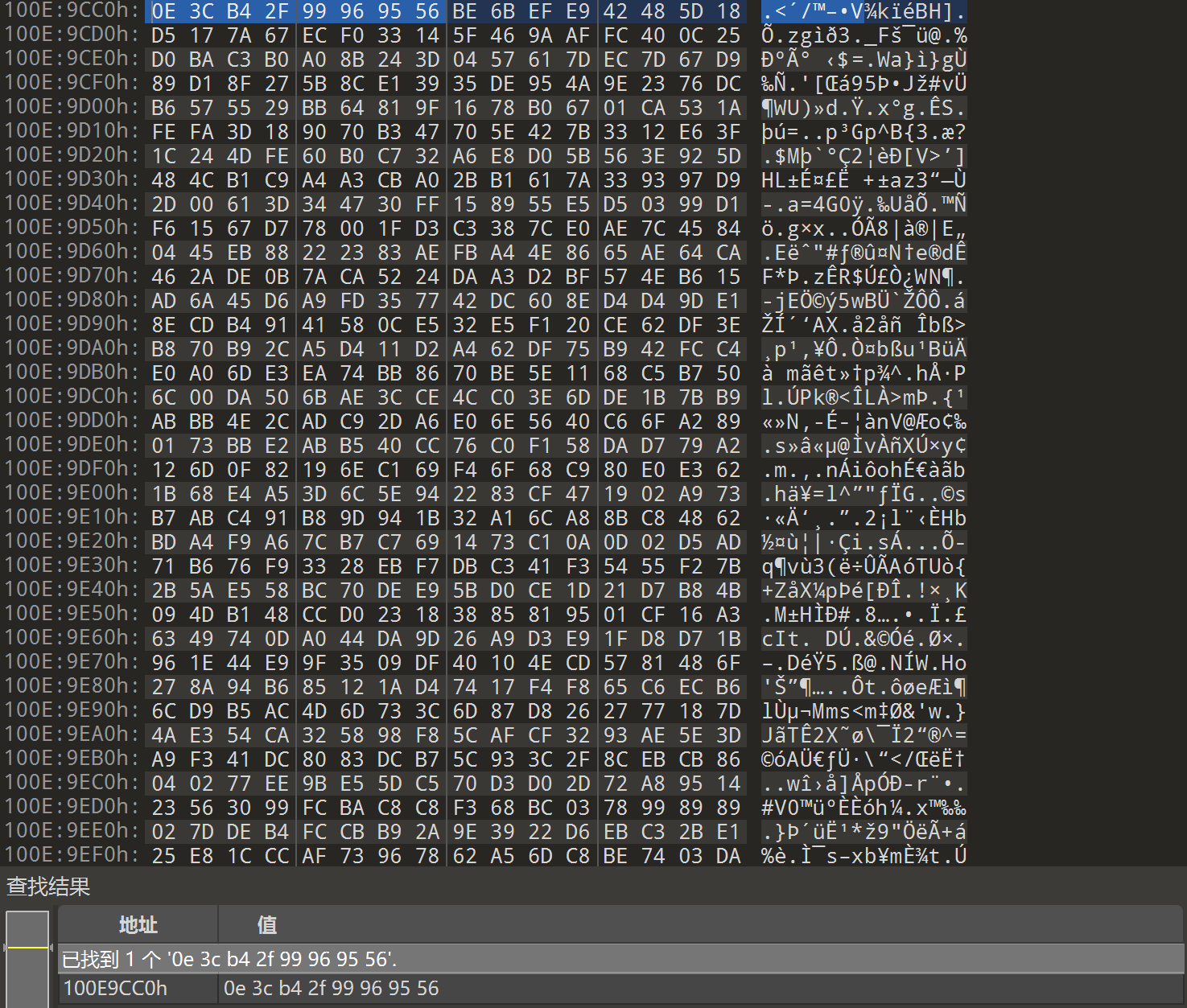
往下翻,看到一些无效数据,所以在这里下断点,将上面的hex数据另存为文件,再用赛博厨子解密即可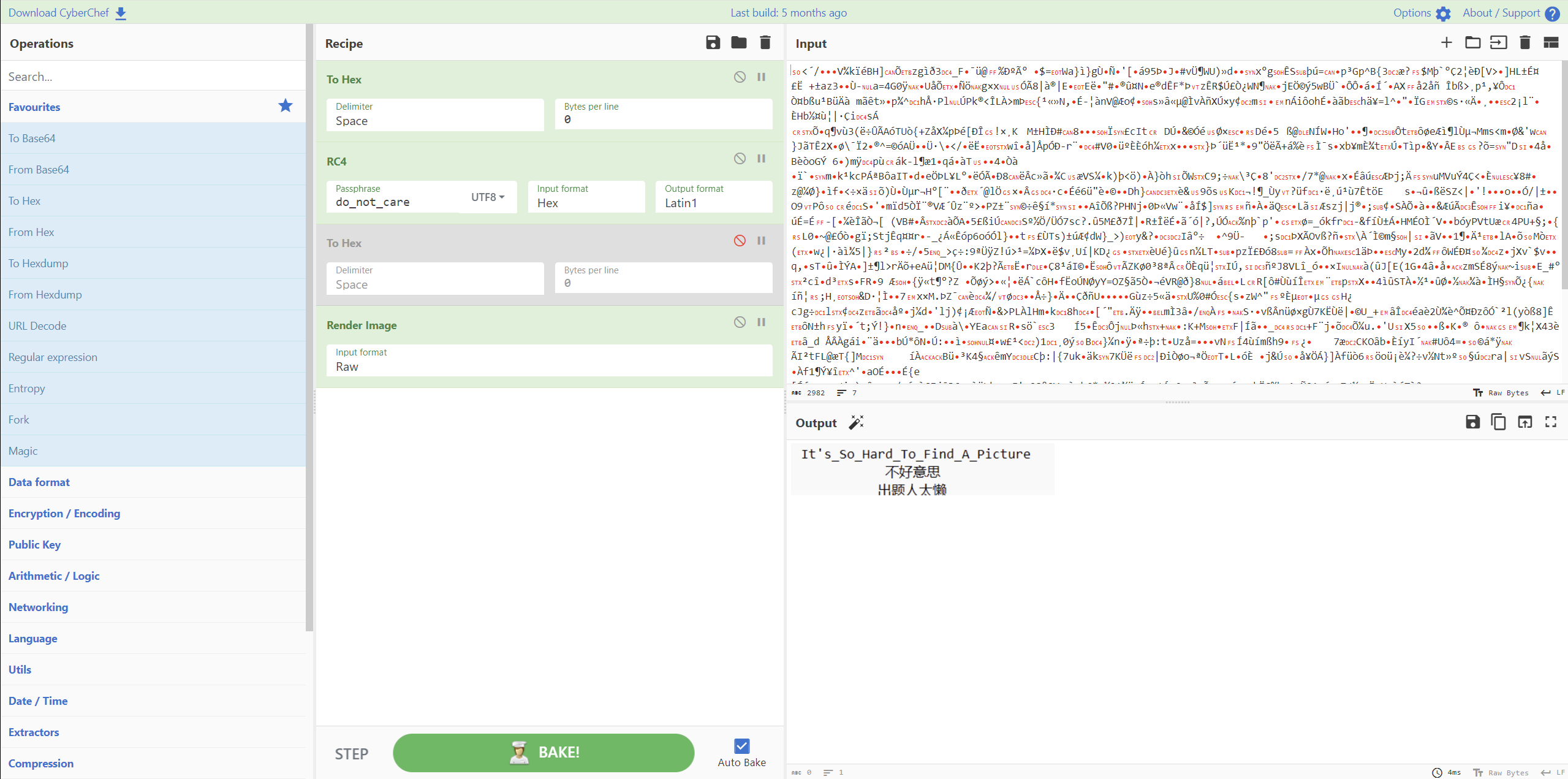

F | ez_fmt | 解题人
题目说明
格式化字符串漏洞
解题思路
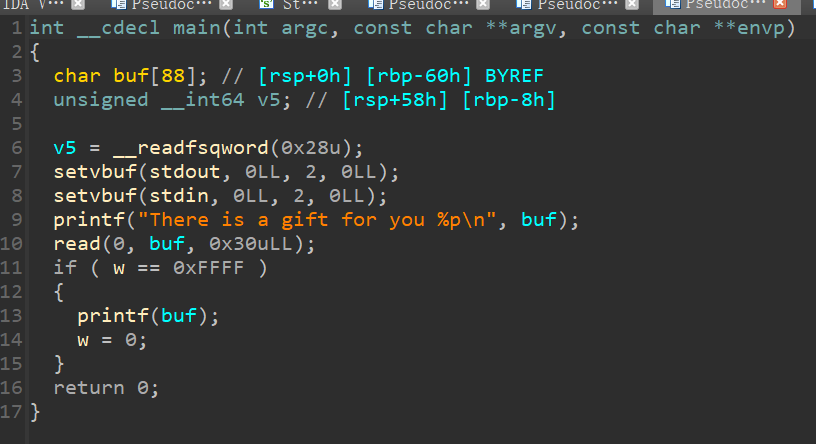
gift会泄露栈顶地址,动调可以算出ret参数的地址
格式化字符串漏洞任意地址写,可以劫持返回地址,利用printf函数泄露libc地址
给了libc文件,直接尝试打one_gadget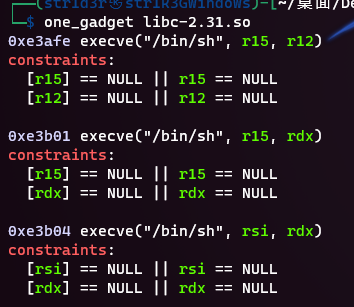
第二个成功
(onegadget地址计算没分情况,概率出)
1 | |